Manual:Wireless PEAP client with FreeRADIUS: Difference between revisions
m →Summary: Linux -> Debian |
No edit summary |
||
| (3 intermediate revisions by one other user not shown) | |||
| Line 2: | Line 2: | ||
=Summary= | =Summary= | ||
The Enterprise variants of WPA and WPA2, also known as 802.1x uses a RADIUS server for authentication purposes. Authentication is achieved using variants of the EAP protocol. | |||
PEAP protocol often is used for wireless EAP authentification. It is considered a secure way to establish EAP authentification. | PEAP protocol often is used for wireless EAP authentification. It is considered a secure way to establish EAP authentification. | ||
| Line 26: | Line 28: | ||
==FreeRADIUS== | ==FreeRADIUS== | ||
Assuming that you have already installed FreeRADIUS server, go to the FreeRADIUS configuration folder: | |||
<pre> | <pre> | ||
~# cd /usr/local/etc/raddb/ | ~# cd /usr/local/etc/raddb/ | ||
</pre> | </pre> | ||
{{Note|Based on your operating system and FreeRADIUS version configuration folder can be located elsewhere.}} | |||
In this folder, you should find files like <code>clients.conf</code>, <code>users</code>, <code>radiusd.conf</code> etc. | In this folder, you should find files like <code>clients.conf</code>, <code>users</code>, <code>radiusd.conf</code> etc. | ||
| Line 48: | Line 49: | ||
* <code>Access-point</code> - can put any name here that describes the Radius client; | * <code>Access-point</code> - can put any name here that describes the Radius client; | ||
* <code>ipaddr</code> - IP address of access point; | * <code>ipaddr</code> - IP address of access point; | ||
* <code>secret</code> - secret password that will allow access point to use RADIUS service. | * <code>secret</code> - secret password that will allow an access point to use RADIUS service. | ||
<b>Add User</b> | <b>Add User</b> | ||
| Line 56: | Line 57: | ||
testing Cleartext-Password := "password" | testing Cleartext-Password := "password" | ||
</pre> | </pre> | ||
* <code>testing</code> - username of user, it will be | * <code>testing</code> - username of the user, it will be necessary to provide this when connecting to access point; | ||
* <code>password</code> - password for the user. | * <code>password</code> - password for the user. | ||
By default, this entry will allow the user with username <code>testing</code> and password <code>password</code> to authenticate. | By default, this entry will allow the user with username <code>testing</code> and password <code>password</code> to authenticate. | ||
| Line 66: | Line 67: | ||
==Access Point== | ==Access Point== | ||
Assuming that you have already configured access points wireless and other settings, we will need to configure security profile and RADIUS client. | |||
<b>Security Profile</b> | <b>Security Profile</b> | ||
| Line 74: | Line 75: | ||
/interface wireless security-profiles add name=EAP_AP mode=dynamic-keys authentication-types=wpa2-eap eap-methods=passthrough | /interface wireless security-profiles add name=EAP_AP mode=dynamic-keys authentication-types=wpa2-eap eap-methods=passthrough | ||
</pre> | </pre> | ||
* <code>name</code> - use any name here, you will reference security profile by it when | * <code>name</code> - use any name here, you will reference security profile by it when assigning to wireless interface; | ||
* <code>mode</code> - set to use <code>dynamic-keys</code> to use | * <code>mode</code> - set to use <code>dynamic-keys</code> to use encryption, otherwise use <code>none</code> to have open access point; | ||
* <code>authentication-types</code> - set security protocol, most devices support <code>wpa2-eap</code> which is considered more secure than <code>wpa-eap</code>; | * <code>authentication-types</code> - set security protocol, most devices support <code>wpa2-eap</code> which is considered more secure than <code>wpa-eap</code>; | ||
* <code>eap-methods</code> - by setting to <code>passthrough</code> EAP authentication packets from wireless client are forwarded to RADIUS server. <code>passthrough</code> is default value for this property. | * <code>eap-methods</code> - by setting to <code>passthrough</code> EAP authentication packets from the wireless client are forwarded to the RADIUS server. <code>passthrough</code> is a default value for this property. | ||
Other settings are can be left to default values. When a security profile is created, for it to take effect it should be set to the wireless interface: | Other settings are can be left to default values. When a security profile is created, for it to take effect it should be set to the wireless interface: | ||
| Line 85: | Line 86: | ||
</pre> | </pre> | ||
* <code>wlan1</code> - name of the wireless interface you are using as client; | * <code>wlan1</code> - a name of the wireless interface you are using as a client; | ||
* <code>security-profile</code> - set to the name of security profile just | * <code>security-profile</code> - set to the name of security profile just created for interface to use it. | ||
Assuming that other properties of the wireless interface are already configured. Properties you might want to configure include <code>mode</code>, <code>band</code>, <code>channel-width</code>, <code>country</code>, <code>frequency</code>,<code>scan-list</code>, and others. | |||
<b>RADIUS</b> | <b>RADIUS</b> | ||
| Line 100: | Line 101: | ||
* <code>address</code> - IP address of RADIUS server; | * <code>address</code> - IP address of RADIUS server; | ||
* <code>secret</code> - password for RADIUS client to access RADIUS services, use the same which is set on RADIUS in <code>clients.conf</code> file; | * <code>secret</code> - password for RADIUS client to access RADIUS services, use the same which is set on RADIUS in <code>clients.conf</code> file; | ||
* <code>service</code> - set to service which to use particular RADIUS server for, same server can be used for multiple services if needed. | * <code>service</code> - set to service which to use particular RADIUS server for, the same server can be used for multiple services if needed. | ||
==Wireless Client== | ==Wireless Client== | ||
In this guide as a wireless client, we use MikroTik router. | In this guide as a wireless client, we use MikroTik router. Assuming that wireless and other settings are already configured, we only need to configure security profile. | ||
<b>Security Profile</b> | <b>Security Profile</b> | ||
| Line 118: | Line 119: | ||
* <code>name</code> - use any name here, you will reference security profile by it when assigning to wireless interface; | * <code>name</code> - use any name here, you will reference security profile by it when assigning to wireless interface; | ||
* <code>mode</code> - set to use <code>dynamic-keys</code> to use | * <code>mode</code> - set to use <code>dynamic-keys</code> to use encryption, otherwise use <code>none</code>, if your access point is open i.e. has no security; | ||
* <code>authentication-types</code> - set security protocol, most devices support <code>wpa2-eap</code> which is considered more secure than <code>wpa-eap</code>. This setting must overlap with what is set on access point; | * <code>authentication-types</code> - set security protocol, most devices support <code>wpa2-eap</code> which is considered more secure than <code>wpa-eap</code>. This setting must overlap with what is set on the access point; | ||
* <code>eap-methods</code> - set it to <code>peap</code> to use PEAP method | * <code>eap-methods</code> - set it to <code>peap</code> to use PEAP method | ||
* <code>supplicant-identity</code> - use some sting, can be the same as username, will be used in first phase of PEAP authentication to establish TLS-based tunnel with RADIUS server. Don't leave empty; | * <code>supplicant-identity</code> - use some sting, can be the same as username, will be used in the first phase of PEAP authentication to establish a TLS-based tunnel with RADIUS server. Don't leave empty; | ||
* <code>mschapv2-username</code> - set as username of RADIUS user, should match with entry in RADIUS <code>users</code> file; | * <code>mschapv2-username</code> - set as the username of RADIUS user, should match with the entry in RADIUS <code>users</code> file; | ||
* <code>mschapv2-password</code> - set as password of RADIUS user, should match with entry in RADIUS <code>users</code> file; | * <code>mschapv2-password</code> - set as the password of RADIUS user, should match with the entry in RADIUS <code>users</code> file; | ||
* <code>tls-mode</code> - define how to manage TLS | * <code>tls-mode</code> - define how to manage TLS certificates, PEAP usually uses server-side certificates, so set to <code>dont-verify-certificate</code>. | ||
Other settings should be left default. | Other settings should be left default. | ||
| Line 134: | Line 135: | ||
</pre> | </pre> | ||
* <code>wlan1</code> - name of the wireless interface you are using as access point; | * <code>wlan1</code> - a name of the wireless interface you are using as an access point; | ||
* <code>security-profile</code> - set to the name of security profile just | * <code>security-profile</code> - set to the name of security profile just created for interface to use it. | ||
Assuming that other wireless interface settings are configured in order to establish a link with the access point and all other settings are correct, the wireless client should authenticate successfully. | |||
=Conclusion= | =Conclusion= | ||
| Line 160: | Line 161: | ||
/system logging add topics=radius prefix=~~~ | /system logging add topics=radius prefix=~~~ | ||
</pre> | </pre> | ||
* <code>topics</code> - set the topic you want to see in log; | * <code>topics</code> - set the topic you want to see in the log; | ||
* <code>prefix</code> - you can add a prefix to | * <code>prefix</code> - you can add a prefix to distinguish RADIUS related logs from other, this is optional; | ||
Now information about communication with RADIUS server can be seen with <code>/log print follow</code>. | Now information about communication with RADIUS server can be seen with <code>/log print follow</code>. | ||
=See also= | |||
* [[Manual:Interface/Wireless | Wireless manual]] | |||
* [[Manual:RADIUS_Client | RADIUS Client manual]] | |||
* [[Manual:System/Log | Log manual]] | |||
* [[Manual:Wireless_EAP-TLS_using_RouterOS_with_FreeRADIUS | RADIUS EAP-TLS example]] | |||
[[Category:Wireless]] | |||
[[Category:Examples]] | |||
Latest revision as of 14:18, 2 January 2019
Summary
The Enterprise variants of WPA and WPA2, also known as 802.1x uses a RADIUS server for authentication purposes. Authentication is achieved using variants of the EAP protocol.
PEAP protocol often is used for wireless EAP authentification. It is considered a secure way to establish EAP authentification.
This guide will show a basic setup to use PEAP on RouterOS wireless client. We will use FreeRADIUS Version 3 server on Debian with a default configuration, RouterOS access point, and RouterOS wireless client. To follow this manual you will need some basic knowledge of RADIUS server and RouterOS wireless configuration.
Configuration
To ensure that you can follow along easily and get started quickly, configuration this guide uses is as default as possible.
First, we will set up a RADIUS server, then access point and a wireless client. Finally, we will look into basic troubleshooting.
Setup
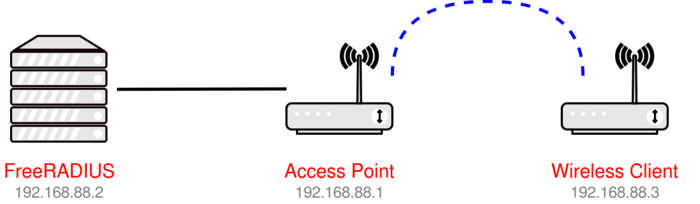
In this guide we will use the following setup:
- 192.168.88.1 - RouterOS Access Point;
- 192.168.88.2 - FreeRADIUS server;
- 192.168.88.3 - RouterOS wireless client.
Please see the network diagram above.
FreeRADIUS
Assuming that you have already installed FreeRADIUS server, go to the FreeRADIUS configuration folder:
~# cd /usr/local/etc/raddb/

Note: Based on your operating system and FreeRADIUS version configuration folder can be located elsewhere.
In this folder, you should find files like clients.conf, users, radiusd.conf etc.
Add Client
Access points that use RADIUS to authenticate their wireless clients from RADIUS point of view are Radius Clients. To allow an access point to use RADIUS you have to edit file clients.conf. The file contains documentation on how to use it. Add the following lines:
client Access-point {
ipaddr = 192.168.88.1
secret = password1234
}
Access-point- can put any name here that describes the Radius client;ipaddr- IP address of access point;secret- secret password that will allow an access point to use RADIUS service.
Add User
To control (allow/limit) access to the wireless client (phone, laptop, another router etc.) you have to edit users file. It is useful to go through documentation of this file, to learn about the vast amount of setting that can be configured for each user. For now just simply add the following line:
testing Cleartext-Password := "password"
testing- username of the user, it will be necessary to provide this when connecting to access point;password- password for the user.
By default, this entry will allow the user with username testing and password password to authenticate.
Run server
To run FreeRADIUS server use radiusd -X. if you want more debug output use radiusd -Xx. If you change any FreeRADIUS settings, you have to restart the server for changes to take effect.
Access Point
Assuming that you have already configured access points wireless and other settings, we will need to configure security profile and RADIUS client.
Security Profile
Security profile must be configured in such way that it will use EAP and passthrough authentication information to RADIUS server. Use the following command line interface command to create a security profile:
/interface wireless security-profiles add name=EAP_AP mode=dynamic-keys authentication-types=wpa2-eap eap-methods=passthrough
name- use any name here, you will reference security profile by it when assigning to wireless interface;mode- set to usedynamic-keysto use encryption, otherwise usenoneto have open access point;authentication-types- set security protocol, most devices supportwpa2-eapwhich is considered more secure thanwpa-eap;eap-methods- by setting topassthroughEAP authentication packets from the wireless client are forwarded to the RADIUS server.passthroughis a default value for this property.
Other settings are can be left to default values. When a security profile is created, for it to take effect it should be set to the wireless interface:
/interface wireless set wlan1 security-profile=EAP_AP
wlan1- a name of the wireless interface you are using as a client;security-profile- set to the name of security profile just created for interface to use it.
Assuming that other properties of the wireless interface are already configured. Properties you might want to configure include mode, band, channel-width, country, frequency,scan-list, and others.
RADIUS
We must specify for the access point which RADIUS server to use for its wireless authentication. Set the following RADIUS setting:
/radius add address=192.168.88.2 secret=password1234 service=wireless
address- IP address of RADIUS server;secret- password for RADIUS client to access RADIUS services, use the same which is set on RADIUS inclients.conffile;service- set to service which to use particular RADIUS server for, the same server can be used for multiple services if needed.
Wireless Client
In this guide as a wireless client, we use MikroTik router. Assuming that wireless and other settings are already configured, we only need to configure security profile.
Security Profile
Security profile must be configured precisely - even slight changes or errors can result in unsuccessful authentication. Add a new security profile:
/interface wireless security-profiles add name=EAP_client \
mode=dynamic-keys authentication-types=wpa2-eap eap-methods=peap \
supplicant-identity=somestring mschapv2-username=testing \
mschapv2-password=password tls-mode=dont-verify-certificate
name- use any name here, you will reference security profile by it when assigning to wireless interface;mode- set to usedynamic-keysto use encryption, otherwise usenone, if your access point is open i.e. has no security;authentication-types- set security protocol, most devices supportwpa2-eapwhich is considered more secure thanwpa-eap. This setting must overlap with what is set on the access point;eap-methods- set it topeapto use PEAP methodsupplicant-identity- use some sting, can be the same as username, will be used in the first phase of PEAP authentication to establish a TLS-based tunnel with RADIUS server. Don't leave empty;mschapv2-username- set as the username of RADIUS user, should match with the entry in RADIUSusersfile;mschapv2-password- set as the password of RADIUS user, should match with the entry in RADIUSusersfile;tls-mode- define how to manage TLS certificates, PEAP usually uses server-side certificates, so set todont-verify-certificate.
Other settings should be left default.
Finally set a newly created security profile to the wireless interface:
/interface wireless set wlan1 security-profile=EAP_client
wlan1- a name of the wireless interface you are using as an access point;security-profile- set to the name of security profile just created for interface to use it.
Assuming that other wireless interface settings are configured in order to establish a link with the access point and all other settings are correct, the wireless client should authenticate successfully.
Conclusion
With this guide should be enough to configure the basic RouterOS wireless client with PEAP authentication. If done correctly, authentication should be successful and you will have a basic setup. However, in real life situations with this setup often is not enough. More advanced configuration should be done to achieve other goals like accounting, limits etc. For other RADIUS configurations you might need to configure access point and/or client differently, some RADIUS configurations might not work with RouterOS devices. RouterOS clients support only MSCHAPv2 as the inner method of PEAP.
Debug
Setuping RADIUS might be challenging and not always everything works as you intend. In these cases, you can use debug logs both on RADIUS server and RouterOS side.
To see debug information while running FreeRADIUS server start it with parameter -X like this:
$ radiusd -X
To get more debug information just add another "x" - radiusd -Xx.
To see debug logs in RouterOS, add logging rule to access point. Use this command to see all packets sent to RADIUS:
/system logging add topics=radius prefix=~~~
topics- set the topic you want to see in the log;prefix- you can add a prefix to distinguish RADIUS related logs from other, this is optional;
Now information about communication with RADIUS server can be seen with /log print follow.
