Manual:Packet Flow: Difference between revisions
No edit summary |
|||
| (3 intermediate revisions by the same user not shown) | |||
| Line 18: | Line 18: | ||
|- | |- | ||
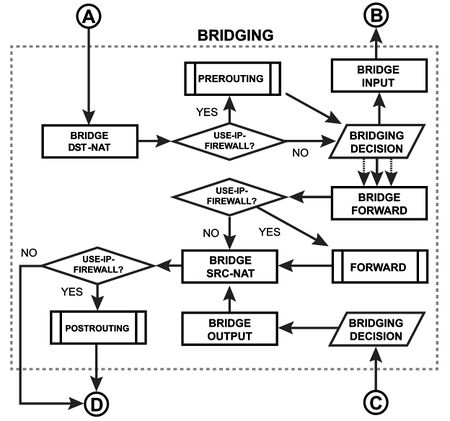
|[[Image:Bridging-Diagram.jpg|450px|Bridging Diagram|center]] | |[[Image:Bridging-Diagram.jpg|450px|Bridging Diagram|center]] | ||
|In this subsection you can inspect how packet are going through the bridge. For example, if you configure <code>/interface bridge settings set use-ip-firewall=yes</code>, then packet will go through the one of | |In this subsection you can inspect how packet are going through the bridge. For example, if you configure <code>/interface bridge settings set use-ip-firewall=yes</code>, then packet will go through the one of three predefined ip firewall chains: prerouting, forward, postrouting. | ||
|} | |} | ||
===MPLS Diagram=== | ===MPLS Diagram=== | ||
| Line 47: | Line 47: | ||
|- | |- | ||
|[[Image: | |[[Image:Physical_in_interface.png|Input Interface|100px]] | ||
|Starting point in packets way through the router facilities. | |Starting point in packets way through the router facilities. Packet is received it will start its way from here. | ||
|- | |- | ||
|[[Image: | |[[Image:Physical_out_interface.png|Output Interface|100px]] | ||
|Last point in packets way through the router facilities. Just before the packet is actually sent out. | |Last point in packets way through the router facilities. Just before the packet is actually sent out. | ||
|- | |||
|[[Image:Logical_in_interface.png|Input Interface|100px]] | |||
|Intermediate interface where packet continues to process through the device after decapsulation | |||
|- | |||
|[[Image:Logical_out_interface.png |Output Interface|100px]] | |||
|Intermediate interface where packet continue to process through the device before encapsulation | |||
|- | |- | ||
| Line 62: | Line 70: | ||
|Starting point for packets generated by router itself | |Starting point for packets generated by router itself | ||
|} | |} | ||
===Configurable Facilities=== | ===Configurable Facilities=== | ||
| Line 84: | Line 93: | ||
|- | |- | ||
| [[Image:src_nat.jpg|Source NAT|100px]] | | [[Image:src_nat.jpg|Source NAT|100px]] | ||
| <code>/ip firewall nat</code> | |||
|- | |||
| [[Image:dst_nat.jpg|Destination NAT|100px]] | |||
| <code>/ip firewall nat</code> | | <code>/ip firewall nat</code> | ||
|- | |- | ||
| Line 145: | Line 157: | ||
|Check if the ''actual input interface'' is a port for bridge OR checks if ''input interface'' is bridge | |Check if the ''actual input interface'' is a port for bridge OR checks if ''input interface'' is bridge | ||
|- | |- | ||
|[[Image: | |[[Image:HOTSPOT_in.png|Hotspot In|100px]] | ||
|Allow to capture traffic witch otherwise would be discarded by connection tracking - this way our Hotspot feature are able to provide connectivity even if networks settings are in complete mess | |Allow to capture traffic witch otherwise would be discarded by connection tracking - this way our Hotspot feature are able to provide connectivity even if networks settings are in complete mess | ||
|- | |- | ||
| Line 160: | Line 172: | ||
|This is a workaround that allows to set-up policy routing in mangle chain output | |This is a workaround that allows to set-up policy routing in mangle chain output | ||
|- | |- | ||
|[[Image:TTL | |[[Image:TTL.png|TTL Adjustment|100px]] | ||
|Indicates exact place where Time To Live (TTL) of the routed packet is reduced by 1. If it become 0 packet will be discarded | |Indicates exact place where Time To Live (TTL) of the routed packet is reduced by 1. If it become 0 packet will be discarded | ||
|- | |- | ||
|[[Image: | |[[Image:IPSEC_decryption.png|IPSec_Decryption|100px]] | ||
|Self explanatory | |Self explanatory | ||
|- | |- | ||
|[[Image: | |[[Image:IPSEC_encryption.png|IPSec_Encryption|100px]] | ||
|Self explanatory | |Self explanatory | ||
|- | |- | ||
| Line 172: | Line 184: | ||
|Check if the ''actual output interface'' is a port for bridge OR checks if ''output interface'' is bridge | |Check if the ''actual output interface'' is a port for bridge OR checks if ''output interface'' is bridge | ||
|- | |- | ||
|[[Image: | |[[Image:Hotspot_out2.png|Hotspot Out|100px]] | ||
|Undo all that was done by hotspot-in for the packets that is going back to client. | |Undo all that was done by hotspot-in for the packets that is going back to client. | ||
|} | |} | ||
==Examples== | ==Examples== | ||
| Line 189: | Line 200: | ||
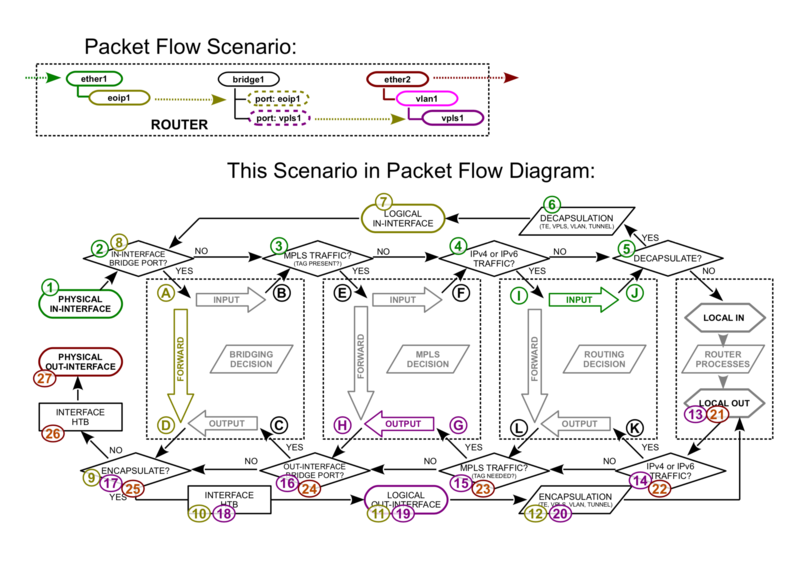
===EoIP with VPLS out=== | ===EoIP with VPLS out=== | ||
[[File:Packetflow6-d.png|Example 4|800px|center]] | [[File:Packetflow6-d.png|Example 4|800px|center]] | ||
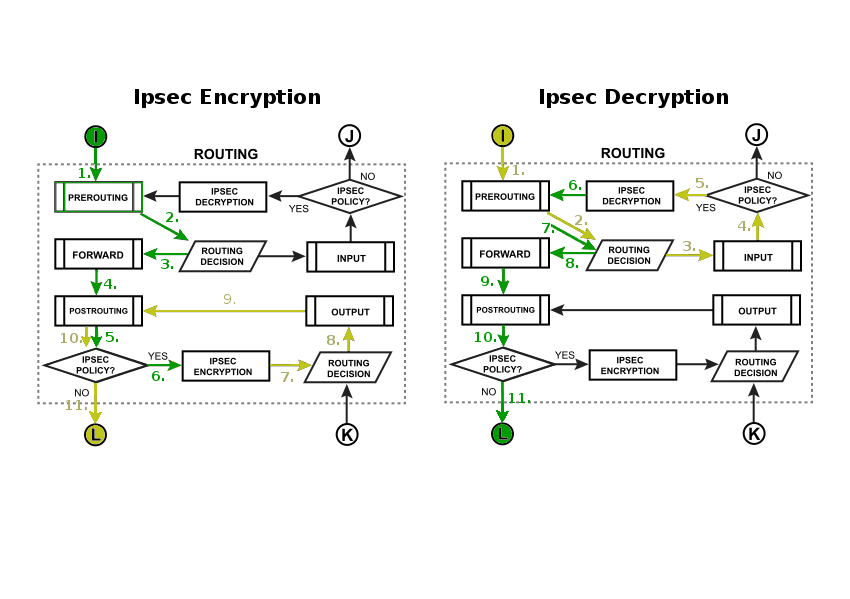
=== | ===IPsec Encryption/Decryption=== | ||
[https://wiki.mikrotik.com/wiki/Manual:IP/IPsec Internet Protocol Security (IPsec)] is a set of protocols defined by the Internet Engineering Task Force (IETF) to secure packet exchange over unprotected IP/IPv6 networks such as Internet. | [https://wiki.mikrotik.com/wiki/Manual:IP/IPsec Internet Protocol Security (IPsec)] is a set of protocols defined by the Internet Engineering Task Force (IETF) to secure packet exchange over unprotected IP/IPv6 networks such as Internet. | ||
[[Image:IpsecFlow.png|Example 5|center]] | [[Image:IpsecFlow.png|Example 5|center]] | ||
Latest revision as of 12:30, 8 January 2019
Overview
MikroTik RouterOS is designed to be easy to operate in various aspects of network configuration. Therefore creating limitation for individual IP or NATting internal clients to a public address or Hotspot configuration can be done without the knowledge about how the packets are processed in the router - you just go to corresponding menu and create necessary configuration.
However more complicated tasks, such as traffic prioritization, routing policies, where it is necessary to utilize more than one RouterOS facility, requires knowledge: How these facilities work together? What happens when and why?
To address these questions we created a packet flow diagram.
Diagrams
For MikroTik RouterOS v6.0 was created detailed diagrams to ease understanding of packet flow.
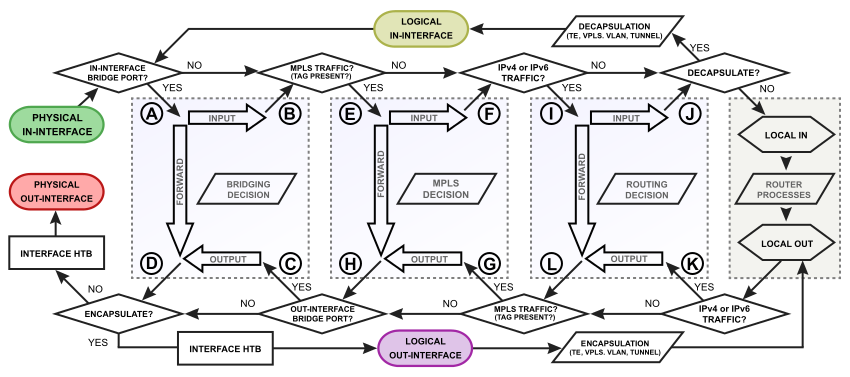
Overall Packetflow Diagram
Bridging Diagram
MPLS Diagram
| Packet-forwarding decisions are made solely on the contents of this label, without the need to examine the packet itself. Diagram describe MPLS label movement in RouterOS. | 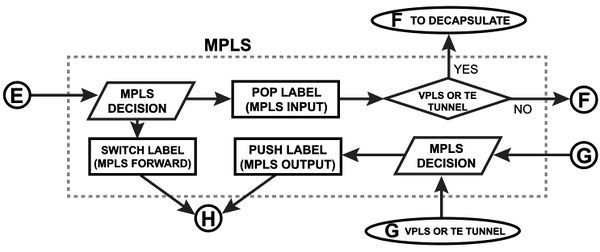 |
Routing Diagram
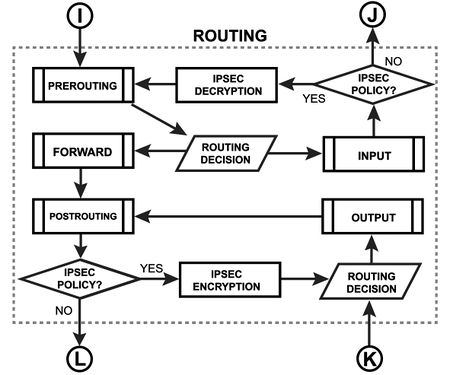 |
Each routing protocol (except BGP) has it's own internal tables. This is where per-protocol routing decisions are made. BGP does not have internal routing tables and stores complete routing information from all peers in the RIB. RIB contains routes grouped in separate routing tables based on their value of routing-mark. All routes without routing-mark are kept in the main routing table. These tables are used for best route selection. The main table is also used for nexthop lookup. |
Packet Flow Chains
This diagram explains in detail each section of the Overall Packetflow Diagram.
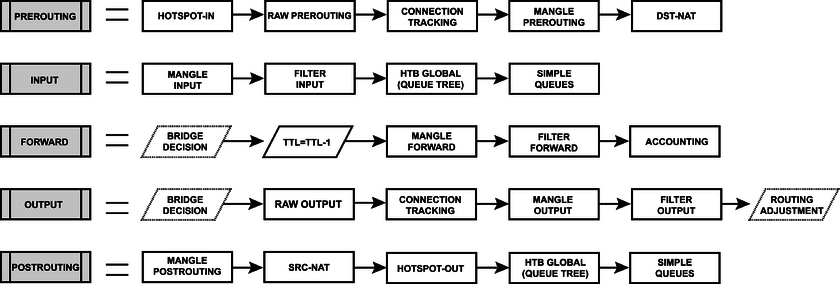
Diagram Analaysis
Basic Concepts
Configurable Facilities
Each and every facilities in this section corresponds with one particular menu in RouterOS. Users are able to access those menu and configure these facilities directly
Automated processes and decisions
Examples
In this subsection you can overview different protocol packet processing in RouterOS.
Bridge port in with PPPoE-out
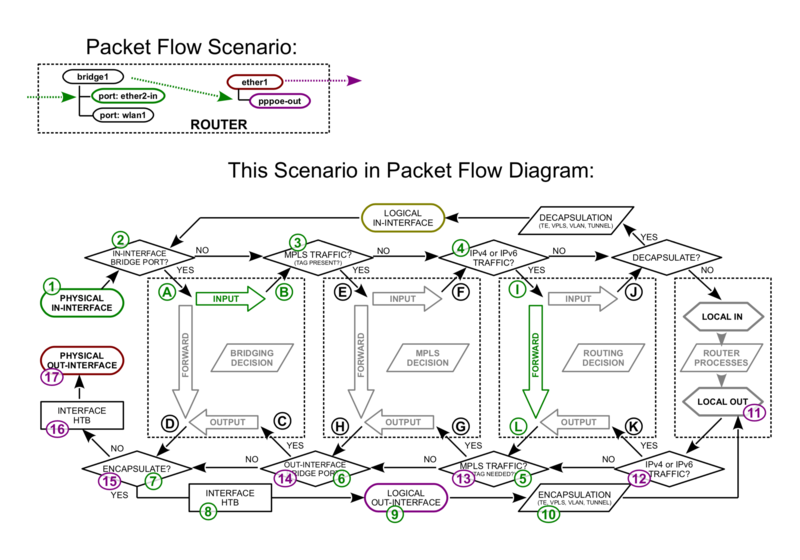
PPPoE-in with bridge port out
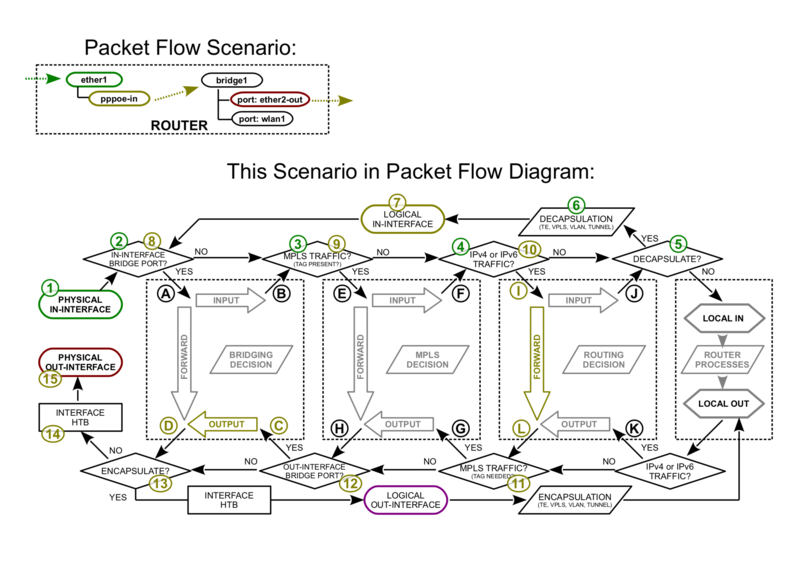
Vlan Untagging/Tagging in the bridge interface
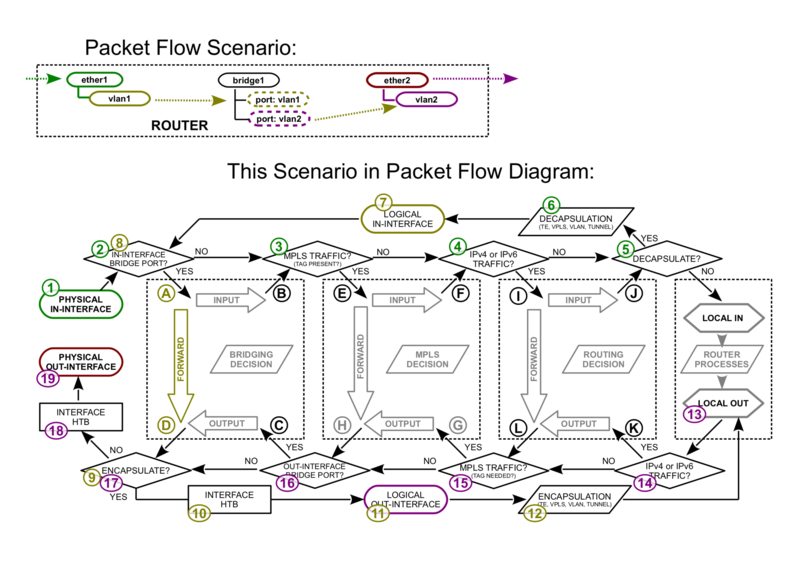
EoIP with VPLS out
IPsec Encryption/Decryption
Internet Protocol Security (IPsec) is a set of protocols defined by the Internet Engineering Task Force (IETF) to secure packet exchange over unprotected IP/IPv6 networks such as Internet.