Manual:IP/Firewall/Connection tracking: Difference between revisions
Jump to navigation
Jump to search
| (25 intermediate revisions by 4 users not shown) | |||
| Line 15: | Line 15: | ||
=== Properties === | === Properties === | ||
All properties in connection list are read-only | |||
{{Mr-arg-table-h | |||
|prop=Property | |||
|desc=Description | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=assured | |||
|type=yes {{!}} no | |||
|desc=Indicates that this connection is assured and that it will not be erased if maximum possible tracked connection count is reached. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=confirmed | |||
|type=yes {{!}} no | |||
|desc=Connection is confirmed and a packet is sent out from the device. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=connection-mark | |||
|type=string | |||
|desc=Connection mark that was set by [[M:IP/Firewall/Mangle | mangle]] rule. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=connection-type | |||
|type=pptp {{!}} ftp | |||
|desc=Type of connection, property is empty if connection tracking is unable to determine predefined connection type. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=dst-address | |||
|type=ip[:port] | |||
|desc=Destination address and port (if protocol is port based). | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=dstnat | |||
|type=yes {{!}} no | |||
|desc=Connection has gone through DST-NAT (for example, port forwarding). | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=dying | |||
|type=yes {{!}} no | |||
|desc=Connection is dying due to connection timeout. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=expected | |||
|type=yes {{!}} no | |||
|desc=Connection is setup using connection helpers (pre-defined service rules). | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=fasttrack | |||
|type=yes {{!}} no | |||
|desc=Whether the connection is FastTracked. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=gre-key | |||
|type=integer | |||
|desc=Contents of the GRE Key field. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=gre-protocol | |||
|type=string | |||
|desc=Protocol of the encapsulated payload. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=gre-version | |||
|type=string | |||
|desc=Version of GRE protocol used in the connection. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=icmp-code | |||
|type=string | |||
|desc=ICMP Code Field | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=icmp-id | |||
|type=integer | |||
|desc=Contains the ICMP ID | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=icmp-type | |||
|type=integer | |||
|desc=ICMP Type Number | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=orig-bytes | |||
|type=integer | |||
|desc=Amount of bytes sent out from the source address using the specific connection. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=orig-fasttrack-bytes | |||
|type=integer | |||
|desc=Amount of FastTracked bytes sent out from the source address using the specific connection. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=orig-fasttrack-packets | |||
|type=integer | |||
|desc=Amount of FastTracked packets sent out from the source address using the specific connection. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=orig-packets | |||
|type=integer | |||
|desc=Amount of packets sent out from the source address using the specific connection. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=orig-rate | |||
|type=integer | |||
|desc=Data rate at which packets are sent out from the source address using the specific connection. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=protocol | |||
|type=string | |||
|desc=IP protocol type | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=repl-bytes | |||
|type=integer | |||
|desc=Amount of bytes received from the destination address using the specific connection. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=repl-fasttrack-bytes | |||
|type=string | |||
|desc=Amount of FastTracked bytes received from the destination address using the specific connection. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=repl-fasttrack-packets | |||
|type=integer | |||
|desc=Amount of FastTracked packets received from the destination address using the specific connection. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=repl-packets | |||
|type=integer | |||
|desc=Amount of packets received from the destination address using the specific connection. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=repl-rate | |||
|type=string | |||
|desc=Data rate at which packets are received from the destination address using the specific connection. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=reply-dst-address | |||
|type=ip[:port] | |||
|desc=Destination address (and port) expected of return packets. Usually the same as "src-address:port" | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=reply-src-address | |||
|type=ip[:port] | |||
|desc=Source address (and port) expected of return packets. Usually the same as "dst-address:port" | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=seen-reply | |||
|type=yes {{!}} no | |||
|desc=Destination address has replied to the source address. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=src-address | |||
|type=ip[:port] | |||
|desc=Source address and port (if protocol is port based). | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=srcnat | |||
|type=yes {{!}} no | |||
|desc=Connection is going through SRC-NAT, including packets that were masqueraded through NAT. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=tcp-state | |||
|type=string | |||
|desc=Current state of TCP connection : | |||
* "established" | |||
* "time-wait" | |||
* "close" | |||
* "syn-sent" | |||
* "syn-received" | |||
}} | |||
{{Mr-arg-ro-table-end | |||
|arg=timeout | |||
|type=time | |||
|desc=Time after connection will be removed from connection list. | |||
}} | |||
==Connection tracking settings== | ==Connection tracking settings== | ||
| Line 29: | Line 239: | ||
{{Mr-arg-table | {{Mr-arg-table | ||
|arg=enabled | |arg=enabled | ||
|type=yes {{!}} no | |type=yes {{!}} no {{!}} auto | ||
|default=auto | |||
|desc=Allows to disable or enable connection tracking. Disabling connection tracking will cause several firewall features to stop working. See the [[#Features affected by connection tracking | list]] of affected features. Starting from v6.0rc2 default value is auto. Which means that connection tracing is disabled until at least one firewall rule is added. | |||
}} | |||
{{Mr-arg-table | |||
|arg=loose-tcp-tracking | |||
|type=yes | no | |||
|default=yes | |default=yes | ||
|desc= | |desc=Disable picking up already established connections | ||
}} | }} | ||
| Line 94: | Line 311: | ||
|type=time | |type=time | ||
|default=10s | |default=10s | ||
|desc= | |desc=Specifies the timeout for udp connections that has seen packets in one direction | ||
}} | }} | ||
| Line 101: | Line 318: | ||
|type=time | |type=time | ||
|default=3m | |default=3m | ||
|desc= | |desc=Specifies the timeout of udp connections that has seen packets in both directions | ||
}} | }} | ||
| Line 108: | Line 325: | ||
|type=time | |type=time | ||
|default=10s | |default=10s | ||
|desc= | |desc=ICMP connection timeout | ||
}} | }} | ||
{{Mr-arg-table | {{Mr-arg-table-end | ||
|arg=generic-timeout | |arg=generic-timeout | ||
|type=time | |type=time | ||
|default=10m | |default=10m | ||
|desc=Timeout for all other connection entries | |desc=Timeout for all other connection entries | ||
}} | }} | ||
| Line 135: | Line 345: | ||
|arg=max-entries | |arg=max-entries | ||
|type=integer | |type=integer | ||
|desc=Max amount of entries that connection tracking table can hold. This value depends on installed amount of RAM. | |desc=Max amount of entries that connection tracking table can hold. This value depends on installed amount of RAM. Note that system does not create maximum size connection tracking table when it starts, maximum entry amount can increase if situation demands it and router still has free ram left. | ||
}} | }} | ||
| Line 155: | Line 365: | ||
** connection-rate | ** connection-rate | ||
** layer7-protocol | ** layer7-protocol | ||
** new-connection-mark | ** new-connection-mark | ||
** tarpit | ** tarpit | ||
[[Category:Manual|Connection tracking]] | [[Category:Manual|Connection tracking]] | ||
[[Category:IP|Connection tracking]] | [[Category:IP|Connection tracking]] | ||
[[Category:Firewall|Connection tracking]] | [[Category:Firewall|Connection tracking]] | ||
Latest revision as of 12:09, 12 April 2019
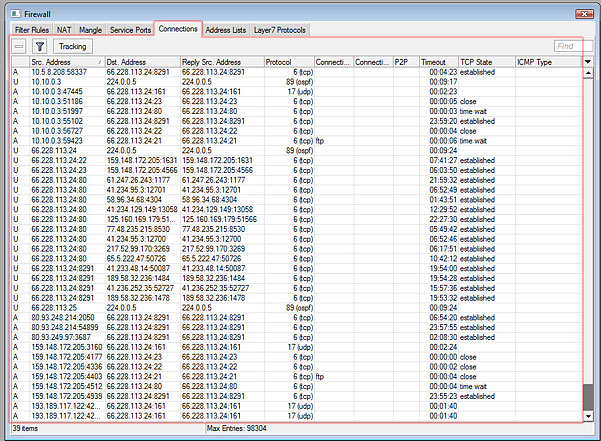
Connection tracking entries
Sub-menu: /ip firewall connection
There are several ways to see what connections are making their way though the router.
In the Winbox Firewall window, you can switch to the Connections tab, to see current connections to/from/through your router. It looks like this:
Properties
All properties in connection list are read-only
| Property | Description |
|---|---|
| assured (yes | no) | Indicates that this connection is assured and that it will not be erased if maximum possible tracked connection count is reached. |
| confirmed (yes | no) | Connection is confirmed and a packet is sent out from the device. |
| connection-mark (string) | Connection mark that was set by mangle rule. |
| connection-type (pptp | ftp) | Type of connection, property is empty if connection tracking is unable to determine predefined connection type. |
| dst-address (ip[:port]) | Destination address and port (if protocol is port based). |
| dstnat (yes | no) | Connection has gone through DST-NAT (for example, port forwarding). |
| dying (yes | no) | Connection is dying due to connection timeout. |
| expected (yes | no) | Connection is setup using connection helpers (pre-defined service rules). |
| fasttrack (yes | no) | Whether the connection is FastTracked. |
| gre-key (integer) | Contents of the GRE Key field. |
| gre-protocol (string) | Protocol of the encapsulated payload. |
| gre-version (string) | Version of GRE protocol used in the connection. |
| icmp-code (string) | ICMP Code Field |
| icmp-id (integer) | Contains the ICMP ID |
| icmp-type (integer) | ICMP Type Number |
| orig-bytes (integer) | Amount of bytes sent out from the source address using the specific connection. |
| orig-fasttrack-bytes (integer) | Amount of FastTracked bytes sent out from the source address using the specific connection. |
| orig-fasttrack-packets (integer) | Amount of FastTracked packets sent out from the source address using the specific connection. |
| orig-packets (integer) | Amount of packets sent out from the source address using the specific connection. |
| orig-rate (integer) | Data rate at which packets are sent out from the source address using the specific connection. |
| protocol (string) | IP protocol type |
| repl-bytes (integer) | Amount of bytes received from the destination address using the specific connection. |
| repl-fasttrack-bytes (string) | Amount of FastTracked bytes received from the destination address using the specific connection. |
| repl-fasttrack-packets (integer) | Amount of FastTracked packets received from the destination address using the specific connection. |
| repl-packets (integer) | Amount of packets received from the destination address using the specific connection. |
| repl-rate (string) | Data rate at which packets are received from the destination address using the specific connection. |
| reply-dst-address (ip[:port]) | Destination address (and port) expected of return packets. Usually the same as "src-address:port" |
| reply-src-address (ip[:port]) | Source address (and port) expected of return packets. Usually the same as "dst-address:port" |
| seen-reply (yes | no) | Destination address has replied to the source address. |
| src-address (ip[:port]) | Source address and port (if protocol is port based). |
| srcnat (yes | no) | Connection is going through SRC-NAT, including packets that were masqueraded through NAT. |
| tcp-state (string) | Current state of TCP connection :
|
| timeout (time) | Time after connection will be removed from connection list. |
Connection tracking settings
Sub-menu: /ip firewall connection tracking
Properties
| Property | Description |
|---|---|
| enabled (yes | no | auto; Default: auto) | Allows to disable or enable connection tracking. Disabling connection tracking will cause several firewall features to stop working. See the list of affected features. Starting from v6.0rc2 default value is auto. Which means that connection tracing is disabled until at least one firewall rule is added. |
| loose-tcp-tracking (yes; Default: yes) | Disable picking up already established connections |
| tcp-syn-sent-timeout (time; Default: 5s) | TCP SYN timeout. |
| tcp-syn-received-timeout (time; Default: 5s) | TCP SYN timeout. |
| tcp-established-timeout (time; Default: 1d) | Time when established TCP connection times out. |
| tcp-fin-wait-timeout (time; Default: 10s) | |
| tcp-close-wait-timeout (time; Default: 10s) | |
| tcp-last-ack-timeout (time; Default: 10s) | |
| tcp-time-wait-timeout (time; Default: 10s) | |
| tcp-close-timeout (time; Default: 10s) | |
| udp-timeout (time; Default: 10s) | Specifies the timeout for udp connections that has seen packets in one direction |
| udp-stream-timeout (time; Default: 3m) | Specifies the timeout of udp connections that has seen packets in both directions |
| icmp-timeout (time; Default: 10s) | ICMP connection timeout |
| generic-timeout (time; Default: 10m) | Timeout for all other connection entries |
Read-only properties
| Property | Description |
|---|---|
| max-entries (integer) | Max amount of entries that connection tracking table can hold. This value depends on installed amount of RAM. Note that system does not create maximum size connection tracking table when it starts, maximum entry amount can increase if situation demands it and router still has free ram left. |
| total-entries (integer) | Amount of connections that currently connection table holds. |
Features affected by connection tracking
- NAT
- firewall:
- connection-bytes
- connection-mark
- connection-type
- connection-state
- connection-limit
- connection-rate
- layer7-protocol
- new-connection-mark
- tarpit