Manual:Failover with firewall marking: Difference between revisions
Created page with "<h2>Summary</h2> This example demonstrates how to set up failover with a Firewall mangle, filter and NAT rules. <h2>Application example</h2> [[File:Dual-wan.png|300px|center]..." |
No edit summary |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 15: | Line 15: | ||
</pre> | </pre> | ||
<h4>Mangle and | <h4>Mangle, NAT and Filter rules</h4> | ||
Connections going through the | Connections going through the ether1 interface is marked as <b>"first"</b> and packets going through the ether2 is marked as <b>"other"</b>. | ||
<pre> | <pre> | ||
/ip firewall mangle | /ip firewall mangle | ||
| Line 33: | Line 33: | ||
When the primary link will fail, we will reject all the established connections, so a new connections will pass through the secondary link. The same behavior will happen when a primary link will come back again and here we will prevent local IP leakage to a public network, which is one of <span class="plainlinks">[https://wiki.mikrotik.com/wiki/Manual:IP/Firewall/NAT#Masquerade masquerades disadvantages]</span>. | When the primary link will fail, we will reject all the established connections, so a new connections will pass through the secondary link. The same behavior will happen when a primary link will come back again and here we will prevent local IP leakage to a public network, which is one of <span class="plainlinks">[https://wiki.mikrotik.com/wiki/Manual:IP/Firewall/NAT#Masquerade masquerades disadvantages]</span>. | ||
<pre> | <pre> | ||
/ip firewall filter | |||
add action=reject chain=forward connection-mark=other out-interface=ether1 reject-with=icmp-network-unreachable | add action=reject chain=forward connection-mark=other out-interface=ether1 reject-with=icmp-network-unreachable | ||
add action=reject chain=forward connection-mark=first out-interface=ether2 reject-with=icmp-network-unreachable | add action=reject chain=forward connection-mark=first out-interface=ether2 reject-with=icmp-network-unreachable | ||
Latest revision as of 09:55, 24 July 2019
Summary
This example demonstrates how to set up failover with a Firewall mangle, filter and NAT rules.
Application example
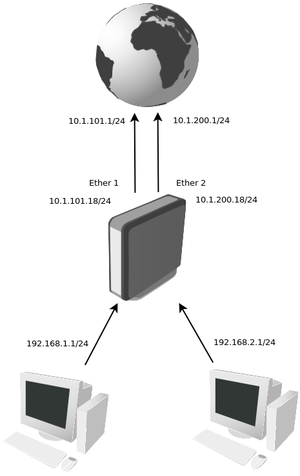
IP address
In this example our provider assigned two upstream links, one connected to ether1 and other to ether2. Our local network has two subnets 192.168.1.0/24 and 192.168.2.0/24
/ip address add address=10.1.101.18/24 interface=ether1 add address=10.1.200.18/24 interface=ether2 add address=192.168.1.1/24 interface=Local add address=192.168.2.1/24 interface=Local
Mangle, NAT and Filter rules
Connections going through the ether1 interface is marked as "first" and packets going through the ether2 is marked as "other".
/ip firewall mangle add action=mark-connection chain=forward connection-mark=no-mark new-connection-mark=first out-interface=ether1 passthrough=yes add action=mark-connection chain=forward connection-mark=no-mark new-connection-mark=other out-interface=ether2 passthrough=yes
Instead of masquerade, we will use src-nat for our local networks, because we do not want to purge connections which is one of masquarades main features when a primary link fails. We will restrict them with a firewall rules (later in this example)
/ip firewall nat add action=src-nat chain=srcnat out-interface=ether1 to-address=10.1.101.18/24 add action=src-nat chain=srcnat out-interface=ether2 to-address=10.1.200.18/24
When the primary link will fail, we will reject all the established connections, so a new connections will pass through the secondary link. The same behavior will happen when a primary link will come back again and here we will prevent local IP leakage to a public network, which is one of masquerades disadvantages.
/ip firewall filter add action=reject chain=forward connection-mark=other out-interface=ether1 reject-with=icmp-network-unreachable add action=reject chain=forward connection-mark=first out-interface=ether2 reject-with=icmp-network-unreachable
Routes
We will add two default routes. With distance parameter we set route preference:
/ip route add gateway=10.1.101.1 distance=1 check-gateway=ping /ip route add gateway=10.1.200.1 distance=2