Manual:CRS1xx/2xx VLANs with Trunks: Difference between revisions
→Port switching: Switch Trunking and STP limitations |
|||
| (3 intermediate revisions by one other user not shown) | |||
| Line 21: | Line 21: | ||
<pre> | <pre> | ||
/interface bridge | /interface bridge | ||
add name=bridge | add name=bridge protocol-mode=none | ||
/interface bridge port | /interface bridge port | ||
add bridge=bridge interface=ether1 | add bridge=bridge interface=ether1 hw=yes | ||
add bridge=bridge interface=ether2 | add bridge=bridge interface=ether2 hw=yes | ||
add bridge=bridge interface=ether3 | add bridge=bridge interface=ether3 hw=yes | ||
add bridge=bridge interface=ether4 | add bridge=bridge interface=ether4 hw=yes | ||
add bridge=bridge interface=ether5 | add bridge=bridge interface=ether5 hw=yes | ||
add bridge=bridge interface=ether6 | add bridge=bridge interface=ether6 hw=yes | ||
add bridge=bridge interface=ether7 | add bridge=bridge interface=ether7 hw=yes | ||
add bridge=bridge interface=ether8 | add bridge=bridge interface=ether8 hw=yes | ||
add bridge=bridge interface=ether9 | add bridge=bridge interface=ether9 hw=yes | ||
add bridge=bridge interface=ether10 | add bridge=bridge interface=ether10 hw=yes | ||
add bridge=bridge interface=ether11 | add bridge=bridge interface=ether11 hw=yes | ||
add bridge=bridge interface=ether12 | add bridge=bridge interface=ether12 hw=yes | ||
add bridge=bridge interface=ether13 | add bridge=bridge interface=ether13 hw=yes | ||
add bridge=bridge interface=ether14 | add bridge=bridge interface=ether14 hw=yes | ||
add bridge=bridge interface=ether15 | add bridge=bridge interface=ether15 hw=yes | ||
add bridge=bridge interface=ether16 | add bridge=bridge interface=ether16 hw=yes | ||
add bridge=bridge interface=ether17 | add bridge=bridge interface=ether17 hw=yes | ||
add bridge=bridge interface=ether18 | add bridge=bridge interface=ether18 hw=yes | ||
add bridge=bridge interface=ether19 | add bridge=bridge interface=ether19 hw=yes | ||
add bridge=bridge interface=ether20 | add bridge=bridge interface=ether20 hw=yes | ||
add bridge=bridge interface=ether21 | add bridge=bridge interface=ether21 hw=yes | ||
add bridge=bridge interface=ether22 | add bridge=bridge interface=ether22 hw=yes | ||
add bridge=bridge interface=ether23 | add bridge=bridge interface=ether23 hw=yes | ||
add bridge=bridge interface=ether24 | add bridge=bridge interface=ether24 hw=yes | ||
add bridge=bridge interface=sfp1 | add bridge=bridge interface=sfp1 hw=yes | ||
</pre> | </pre> | ||
{{ Warning | Bridge (R)STP is not aware of underlying switch trunking configuration and some trunk ports can move to discarding or blocking state. When trunking member ports are connected to other bridges, you should either disable the (R)STP or filter out any BPDU between trunked devices (e.g. with [[Manual:CRS1xx/2xx_series_switches#Access_Control_List | ACL rules]]).}} | |||
Disable SFP interface for security reasons (in case it is not being used): | Disable SFP interface for security reasons (in case it is not being used): | ||
| Line 234: | Line 236: | ||
<pre> | <pre> | ||
/interface vlan | /interface vlan | ||
add interface=bond1 name= | add interface=bond1 name=VLAN10 vlan-id=10 | ||
add interface=bond1 name= | add interface=bond1 name=VLAN20 vlan-id=20 | ||
add interface=bond1 name= | add interface=bond1 name=VLAN30 vlan-id=30 | ||
add interface=bond1 name= | add interface=bond1 name=VLAN40 vlan-id=40 | ||
/ip address | /ip address | ||
add address=192.168.10.1/24 interface= | add address=192.168.10.1/24 interface=VLAN10 | ||
add address=192.168.20.1/24 interface= | add address=192.168.20.1/24 interface=VLAN20 | ||
add address=192.168.30.1/24 interface= | add address=192.168.30.1/24 interface=VLAN30 | ||
add address=192.168.40.1/24 interface= | add address=192.168.40.1/24 interface=VLAN40 | ||
</pre> | </pre> | ||
| Line 254: | Line 256: | ||
<pre> | <pre> | ||
/ip pool | /ip pool | ||
add name= | add name=VLAN10_pool ranges=192.168.10.100-192.168.10.200 | ||
add name= | add name=VLAN20_pool ranges=192.168.20.100-192.168.20.200 | ||
add name= | add name=VLAN30_pool ranges=192.168.30.100-192.168.30.200 | ||
add name= | add name=VLAN40_pool ranges=192.168.40.100-192.168.40.200 | ||
/ip dhcp-server | /ip dhcp-server | ||
add address-pool= | add address-pool=VLAN10_pool disabled=no interface=VLAN10 name=Vlan10_DHCP | ||
add address-pool= | add address-pool=VLAN20_pool disabled=no interface=VLAN20 name=Vlan20_DHCP | ||
add address-pool= | add address-pool=VLAN30_pool disabled=no interface=VLAN30 name=Vlan30_DHCP | ||
add address-pool= | add address-pool=VLAN40_pool disabled=no interface=VLAN40 name=Vlan40_DHCP | ||
/ip dhcp-server network | /ip dhcp-server network | ||
add address=192.168.10.0/24 dns-server=192.168.10.1 gateway=192.168.10.1 | add address=192.168.10.0/24 dns-server=192.168.10.1 gateway=192.168.10.1 | ||
Latest revision as of 10:53, 31 July 2019
Summary
This page will show how to configure multiple switches to use port trunking and port based VLANs, it will also show a working example with a DHCP-Server, interVLAN routing, management IP and invalid VLAN filtering configuration.

Warning: This article applies to CRS1xx and CRS2xx series switches and not to CRS3xx series switches. For a similar setup for CRS3xx series switches you can check the CRS3xx VLANs with Bonds guide.
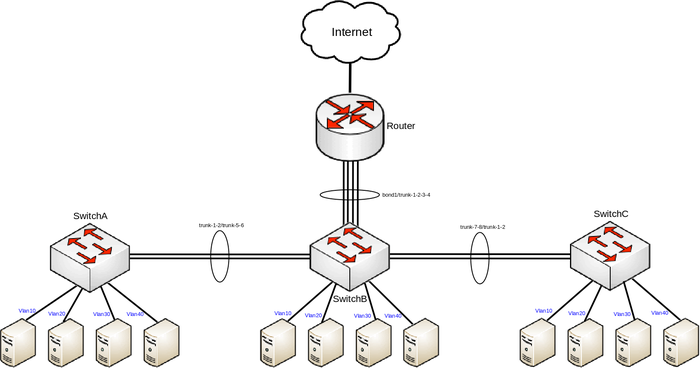

Note: Configuration is written for CRS125-24G-1S and CRS226-24G-2S+, but will work on other CRS1xx/CRS2xx series switches as well.
In this setup SwitchA and SwitchC will tag all traffic from ports ether3-ether6 to VLAN ID 10, ether7-ether12 to VLAN ID 20, ether13-ether18 to VLAN ID 30, ether19-ether24 to VLAN ID 40. SwitchB will tag all traffic from ports ether9-ether12 to VLAN ID 10, ether13-ether16 to VLAN ID 20, ether17-ether20 to VLAN ID 30, ether21-ether24 to VLAN ID 40. Management will only be possible if user is connecting with tagged traffic with VLAN ID 99. SFP port is not used in this setup at all, consider disabling it if not being used.
Port switching
All switches in this setup require that all used ports are switched together. Use these commands on SwitchA, SwitchB, SwitchC:
/interface bridge add name=bridge protocol-mode=none /interface bridge port add bridge=bridge interface=ether1 hw=yes add bridge=bridge interface=ether2 hw=yes add bridge=bridge interface=ether3 hw=yes add bridge=bridge interface=ether4 hw=yes add bridge=bridge interface=ether5 hw=yes add bridge=bridge interface=ether6 hw=yes add bridge=bridge interface=ether7 hw=yes add bridge=bridge interface=ether8 hw=yes add bridge=bridge interface=ether9 hw=yes add bridge=bridge interface=ether10 hw=yes add bridge=bridge interface=ether11 hw=yes add bridge=bridge interface=ether12 hw=yes add bridge=bridge interface=ether13 hw=yes add bridge=bridge interface=ether14 hw=yes add bridge=bridge interface=ether15 hw=yes add bridge=bridge interface=ether16 hw=yes add bridge=bridge interface=ether17 hw=yes add bridge=bridge interface=ether18 hw=yes add bridge=bridge interface=ether19 hw=yes add bridge=bridge interface=ether20 hw=yes add bridge=bridge interface=ether21 hw=yes add bridge=bridge interface=ether22 hw=yes add bridge=bridge interface=ether23 hw=yes add bridge=bridge interface=ether24 hw=yes add bridge=bridge interface=sfp1 hw=yes

Warning: Bridge (R)STP is not aware of underlying switch trunking configuration and some trunk ports can move to discarding or blocking state. When trunking member ports are connected to other bridges, you should either disable the (R)STP or filter out any BPDU between trunked devices (e.g. with ACL rules).
Disable SFP interface for security reasons (in case it is not being used):
/interface ethernet set [find where name~"sfp"] disabled=yes
Port trunking
Port trunking is used when a larger amount of bandwidth is required, this is done by creating a static link aggregation group, which also provides hardware automatic failover and load balancing for CRS1xx/CRS2xx series switches. By adding two 1Gbps interfaces to a trunk, you can increase the theoretical bandwidth limit to 2Gbps. Make sure that all trunked interfaces are linked to the same speed rates.

Note: CRS1xx/CRS2xx series switches aggregate traffic using the built-in Switch Chip without using CPU resources, to route the traffic a router with a powerful CPU is required to handle the aggregated traffic.
To create a 2Gbps port trunk from ether1 and ether2 between SwitchA, SwitchB and SwitchC, use these commands on SwitchA and SwitchC:
/interface ethernet switch trunk add member-ports=ether1,ether2 name=trunk-1-2
To create a 4Gbps port trunk from ether1,ether2,ether3,ether4 between SWitchB and the Router, use these commands on SwitchB:
/interface ethernet switch trunk add member-ports=ether1,ether2,ether3,ether4 name=trunk-1-2-3-4
On SwitchB ether5 and ether6 will be used to connect with SwitchA at 2Gbps and ether7,ether8 will be used to connect with SwitchC at 2Gbps. Use these command on SwitchB:
/interface ethernet switch trunk add member-ports=ether5,ether6 name=trunk-5-6 add member-ports=ether7,ether8 name=trunk-7-8
Management IP
It is very useful to create a management interface and assign an IP address to it in order to preserve access to the switch. This is also very useful when updating your switches since such traffic to the switch will be blocked when enabling invalid VLAN filtering.
Create a VLAN interface on SwitchA, SwitchB, SwitchC:
/interface vlan add interface=bridge1 name=VLAN99 vlan-id=99
For this guide we are going to use these addresses for each device:
| Address | Device |
|---|---|
| 192.168.99.1 | Router |
| 192.168.99.2 | SwitchA |
| 192.168.99.3 | SwitchB |
| 192.168.99.4 | SwitchC |
Add an IP address for each device on the VLAN interface (change X to appropriate number):
/ip address add address=192.168.99.X/24 interface=VLAN99
Don't forget to add the default gateway and specify a DNS server:
/ip route add gateway=192.168.99.1 /ip dns set servers=192.168.99.1
Add the IP address on the Router:
/ip address add address=192.168.99.1/24 interface=VLAN99
Bonding
Unlike CRS1xx/CRS2xx series switches that use the built-in Switch Chip to create a aggregated link group, a router will use the CPU to create the aggregated link group.
To create a bonding interface for ether1,ether2,ether3,ether4, use these commands on the Router:
/interface bonding add mode=balance-xor name=bond1 slaves=ether1,ether2,ether3,ether4\ transmit-hash-policy=layer-2-and-3

Warning: Don't use bonding interfaces on CRS1xx/CRS2xx series devices, bonding interface does NOT use the built-in Switch Chip to create aggregated link group and will overload the CPU instantly. For CRS series device use only port trunking.
Now a VLAN interface can be created on the newly created bonding interface for management and assign an IP address to it, use these commands on the Router:
/interface vlan add interface=bond1 name=VLAN99 vlan-id=99 /ip address add address=192.168.99.1/24 interface=VLAN99
Port based VLAN
When using port trunks, the main difference is that access ports are now trunk ports and they should be used in the Egress VLAN tag table, Ingress VLAN translation table and VLAN table instead of physical Ethernet interfaces.
To create each trunk port as access port, use these commands on SwitchA and SwitchC:
/interface ethernet switch egress-vlan-tag add tagged-ports=trunk-1-2 vlan-id=10 add tagged-ports=trunk-1-2 vlan-id=20 add tagged-ports=trunk-1-2 vlan-id=30 add tagged-ports=trunk-1-2 vlan-id=40
Similarly add entries to the Egress VLAN tag table for SwitchB, use these commands on SwitchB:
/interface ethernet switch egress-vlan-tag add tagged-ports=trunk-1-2-3-4,trunk-5-6,trunk-7-8 vlan-id=10 add tagged-ports=trunk-1-2-3-4,trunk-5-6,trunk-7-8 vlan-id=20 add tagged-ports=trunk-1-2-3-4,trunk-5-6,trunk-7-8 vlan-id=30 add tagged-ports=trunk-1-2-3-4,trunk-5-6,trunk-7-8 vlan-id=40

Note: Management VLAN ID is not addedd to Egress VLAN tag table since a VLAN interface has been already created that will only send out tagged traffic either way.
Specify for each Ethernet interface a VLAN ID that will be assigned for a device that uses the port, use these commands for SwitchA and SwitchC:
/interface ethernet switch ingress-vlan-translation add new-customer-vid=10 ports=ether3,ether4,ether5,ether6 add new-customer-vid=20 ports=ether7,ether8,ether9,ether10,ether11,ether12 add new-customer-vid=30 ports=ether13,ether14,ether15,ether16,ether17,ether18 add new-customer-vid=40 ports=ether19,ether20,ether21,ether22,ether23,ether24
Similarly specify a VLAN ID for each Ethernet interface on SwitchB, use these commands on SwitchB:
/interface ethernet switch ingress-vlan-translation add new-customer-vid=10 ports=ether9,ether10,ether11,ether12 add new-customer-vid=20 ports=ether13,ether14,ether15,ether16 add new-customer-vid=30 ports=ether17,ether18,ether19,ether20 add new-customer-vid=40 ports=ether21,ether22,ether23,ether24
It is required add allowed VLAN IDs to the VLAN table in order for VLAN filtering to work properly. Specify each VLAN ID and each port that is allowed to forward a certain VLAN ID. Use trunk ports instead of physical Ethernet interfaces. Use these commands on SwitchA and SwitchC:
/interface ethernet switch vlan add ports=trunk-1-2,ether3,ether4,ether5,ether6 vlan-id=10 add ports=trunk-1-2,ether7,ether8,ether9,ether10,ether11,ether12 vlan-id=20 add ports=trunk-1-2,ether13,ether14,ether15,ether16,ether17,ether18 vlan-id=30 add ports=trunk-1-2,ether19,ether20,ether21,ether22,ether23,ether24 vlan-id=40 add ports=trunk-1-2,switch1-cpu vlan-id=99
Similarly add entries to the VLAN table for SwitchB, use the commands on SwitchB:
/interface ethernet switch vlan add ports=trunk-1-2-3-4,trunk-5-6,trunk-7-8,ether9,ether10,ether11,ether12 vlan-id=10 add ports=trunk-1-2-3-4,trunk-5-6,trunk-7-8,ether13,ether14,ether15,ether16 vlan-id=20 add ports=trunk-1-2-3-4,trunk-5-6,trunk-7-8,ether17,ether18,ether19,ether20 vlan-id=30 add ports=trunk-1-2-3-4,trunk-5-6,trunk-7-8,ether21,ether22,ether23,ether24 vlan-id=40 add ports=trunk-1-2-3-4,trunk-5-6,trunk-7-8,switch1-cpu vlan-id=99

Note: It is required to specify switch1-cpu port in the VLAN table in order to allow access the the previously created VLAN interface for management purposes.
Invalid VLAN filtering
If ingress VLAN translation table, egress VLAN tag table and VLAN table is properly set, invalid VLAN filtering can be enabled, which will drop any other packet that does not a suitable entry in the VLAN table.

Warning: Double check if port based VLANs are set up properly. If a mistake was made, you might loose access to the switch and it can only be regained by resetting theconfiguration or by using the serial console.
To enable invalid VLAN filtering, use these commands on SwitchA, SwitchB, SwitchC:
/interface ethernet switch set drop-if-invalid-or-src-port-not-member-of-vlan-on-ports="ether1,ether2,ether3,ether4\ ,ether5,ether6,ether7,ether8,ether9,ether10,ether11,ether12,ether13\ ,ether14,ether15,ether16,ether17,ether18,ether19,ether20,ether21,ether22,ether23,ether24"
InterVLAN routing
To create InterVLAN routing, VLAN interface for each customer VLAN ID must be created on the router and must have an IP address assigned to it. The VLAN interface must be created on the bonding interface created previously.
Use these commands on the Router:
/interface vlan add interface=bond1 name=VLAN10 vlan-id=10 add interface=bond1 name=VLAN20 vlan-id=20 add interface=bond1 name=VLAN30 vlan-id=30 add interface=bond1 name=VLAN40 vlan-id=40 /ip address add address=192.168.10.1/24 interface=VLAN10 add address=192.168.20.1/24 interface=VLAN20 add address=192.168.30.1/24 interface=VLAN30 add address=192.168.40.1/24 interface=VLAN40

Note: These commands are required for DHCP-Server. In case interVLAN routing is not desired but a DHCP-Server on a single router is required, then use Firewall Filter to block access between different subnets.
DHCP-Server
To get the DHCP-Server working for each VLAN ID, the server must be set up on the previously created VLAN interfaces (one server for each VLAN ID). Preferably each VLAN ID should have its own subnet and its own IP pool. DNS Server could be specified as the router's IP address for particular VLAN ID or a global DNS Server could be used, but this address must be reachable.
To set up the DHCP-Server, use these commands on the Router:
/ip pool add name=VLAN10_pool ranges=192.168.10.100-192.168.10.200 add name=VLAN20_pool ranges=192.168.20.100-192.168.20.200 add name=VLAN30_pool ranges=192.168.30.100-192.168.30.200 add name=VLAN40_pool ranges=192.168.40.100-192.168.40.200 /ip dhcp-server add address-pool=VLAN10_pool disabled=no interface=VLAN10 name=Vlan10_DHCP add address-pool=VLAN20_pool disabled=no interface=VLAN20 name=Vlan20_DHCP add address-pool=VLAN30_pool disabled=no interface=VLAN30 name=Vlan30_DHCP add address-pool=VLAN40_pool disabled=no interface=VLAN40 name=Vlan40_DHCP /ip dhcp-server network add address=192.168.10.0/24 dns-server=192.168.10.1 gateway=192.168.10.1 add address=192.168.20.0/24 dns-server=192.168.20.1 gateway=192.168.20.1 add address=192.168.30.0/24 dns-server=192.168.30.1 gateway=192.168.30.1 add address=192.168.40.0/24 dns-server=192.168.40.1 gateway=192.168.40.1
In case the router's DNS Server is being used, don't forget to allow remote requests and make sure DNS Servers are configured on the router. Use these commands on the Router:
/ip dns set allow-remote-requests=yes servers=8.8.8.8

Warning: Make sure to secure your local DNS Server with Firewall from the outside when using allow-remote-requests set to yes since your DNS Server can be used for DDoS attacks if it is accessible from the Internet by anyone.
Don't forget to create NAT, assuming that sfp-sfpplus1 is used as WAN port, use these commands on the Router:
/ip firewall nat add action=masquerade chain=srcnat out-interface=sfp-sfpplus1
Jumbo frames
One can increase the total throughput in such a setup by enabling jumbo frames. This reduces the packet overhead by increasing the Maximum Transmission Unit (MTU). If a device in your network does not support jumbo frames, then it will not benefit from a larger MTU. Usually the whole network does not support jumbo frames, but you can still benefit when sending data between devices that support jumbo frames, including all switches in the path.
In this case, if clients behind SwitchA and client behind SwitchC supports jumbo frames, then enabling jumbo frames will be beneficial. Before enabling jumbo frames, determine the MAX-L2MTU by using this command:
[admin@MikroTik] > /interface> print Flags: D - dynamic, X - disabled, R - running, S - slave # NAME TYPE ACTUAL-MTU L2MTU MAX-L2MTU 0 R ether1 ether 1500 1580 4064

Note: More information can be found in MTU manual page.
When MAX-L2MTU is determined, choose the MTU size depending on the traffic on your network, use this command on SwitchA, SwitchB and SwitchC:
/interface ethernet set [ find ] l2mtu=4064 mtu=4040

Note: Don't forget to change the MTU on your client devices too, otherwise above mentioned settings will not have any effect.
See also
- Bonding
- CRS examples
- CRS features
- Switch Chip Features
- IP/DNS
- NAT examples
- Firewall filter examples
- VLAN
- MTU on RouterBOARD
[ Top | Back to Content ]
