SwOS/CSS106: Difference between revisions
No edit summary |
No edit summary |
||
| (9 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
{{Warning|This manual is moved to https://help.mikrotik.com/docs/display/SWOS/CSS106+%28RB260%29+series+Manual}} | |||
==Summary== | ==Summary== | ||
<p> | <p> | ||
| Line 6: | Line 9: | ||
SwOS is configurable from your web browser. It gives you all the basic functionality for a managed switch, plus more: allows to manage port-to-port forwarding, broadcast storm control, apply MAC filter, configure VLANs, mirror traffic, apply bandwidth limitation and even adjust some MAC and IP header fields. | SwOS is configurable from your web browser. It gives you all the basic functionality for a managed switch, plus more: allows to manage port-to-port forwarding, broadcast storm control, apply MAC filter, configure VLANs, mirror traffic, apply bandwidth limitation and even adjust some MAC and IP header fields. | ||
</p> | </p> | ||
{{Warning | Each | {{Warning | Each RouterBOARD switch series have their own firmware which cannot be installed on other series models! New RB260GS (CSS106-5G-1S), new RB260GSP(CSS106-1G-4P-1S) supports SwOS v2.0 and newer. | ||
When upgrading the device, it will first load primary firmware and then make an upgrade. In case a wrong firmware file is chosen, the device will continue to operate with primary firmware and you will be able to choose the correct file.}} | |||
==CSS106 series features== | ==CSS106 series features== | ||
| Line 232: | Line 236: | ||
</tr> | </tr> | ||
</table> | </table> | ||
{{ Note | Using SFP+ 1m/3m DAC cable or S-RJ01 module, the device always shows that link is established even if nothing is connected on other end.}} | |||
===PoE (CSS106-1G-4P-1S)=== | ===PoE (CSS106-1G-4P-1S)=== | ||
| Line 301: | Line 307: | ||
<tr> | <tr> | ||
<td><b>Port Lock</b></td><td> | <td><b>Port Lock</b></td><td> | ||
* <code><b>Port Lock</b></code> - | * <code><b>Port Lock</b></code> - Enables or disables MAC address learning on this port. When option is enabled, it will restrict MAC address learning and static MAC addresses should be configured | ||
* <code><b>Lock On First</b></code> - enable or disable MAC address learning on this port (MAC address from the first recieved packet will still be learnt)</td> | * <code><b>Lock On First</b></code> - enable or disable MAC address learning on this port (MAC address from the first recieved packet will still be learnt)</td> | ||
</tr> | </tr> | ||
| Line 419: | Line 425: | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td><b>Default VLAN ID</b></td><td>Switch will treat both untagged and "Default VLAN ID" tagged ingress packets as they are tagged with this VLAN ID. VLAN tag itself will be added | <td><b>Default VLAN ID</b></td><td>Switch will treat both untagged and "Default VLAN ID" tagged ingress packets as they are tagged with this VLAN ID. It is also used to untag egress traffic if packet's VLAN ID matches "Default VLAN ID". The VLAN tag itself will only be added if there is <code>VLAN Header = add if missing</code> specified on egress port</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 435: | Line 441: | ||
{{ Note | VLAN modes <code><b>enabled</b></code> and <code><b>strict</b></code> require VLAN ID 1 in VLANs table to allow access of untagged traffic to switch itself.}} | {{ Note | VLAN modes <code><b>enabled</b></code> and <code><b>strict</b></code> require VLAN ID 1 in VLANs table to allow access of untagged traffic to switch itself.}} | ||
=== | ===VLAN Configuration Examples=== | ||
Simple trunk and access port configuration, as well as trunk and hybrid port configuration examples can be found in this article - [[SwOS/CSS106-VLAN-Example]]. | |||
==VLANs== | ==VLANs== | ||
<p>VLAN tables specifies certain forwarding rules for packets that have specific IEEE 802.1Q tag. Basically the table contains entries that map specific VLAN tag IDs to a group of one or more ports. Packets with VLAN tags leave switch through one or more ports that are set in corresponding table entry. VLAN table works together with destination MAC lookup to determine egress ports. VLAN table supports up to | <p>VLAN tables specifies certain forwarding rules for packets that have specific IEEE 802.1Q tag. Basically the table contains entries that map specific VLAN tag IDs to a group of one or more ports. Packets with VLAN tags leave switch through one or more ports that are set in corresponding table entry. VLAN table works together with destination MAC lookup to determine egress ports. VLAN table supports up to 250 entries.</p> | ||
[[File:Swos_vlan_css106.png|center|alt=Alt text|CSS106 VLANs settings|center|frame]] | [[File:Swos_vlan_css106.png|center|alt=Alt text|CSS106 VLANs settings|center|frame]] | ||
| Line 539: | Line 544: | ||
==SNMP== | ==SNMP== | ||
<p>SNMP | <p>SwOS supports SNMP v1 and uses IF-MIB, SNMPv2-MIB, BRIDGE-MIB and MIKROTIK-MIB (only for health, PoE-out and SFP diagnostics) for SNMP reporting.</p> | ||
Available SNMP data: | Available SNMP data: | ||
| Line 546: | Line 551: | ||
* <code><b>Port status</b></code> | * <code><b>Port status</b></code> | ||
* <code><b>Interface statistics</b></code> | * <code><b>Interface statistics</b></code> | ||
* <code><b>Host table information</b></code> | |||
[[File:swos-snmp2.png|alt=Alt text|SNMP settings|center|frame]] | [[File:swos-snmp2.png|alt=Alt text|SNMP settings|center|frame]] | ||
| Line 568: | Line 574: | ||
</tr> | </tr> | ||
</table> | </table> | ||
==ACL== | ==ACL== | ||
Latest revision as of 16:29, 21 July 2021

Warning: This manual is moved to https://help.mikrotik.com/docs/display/SWOS/CSS106+%28RB260%29+series+Manual
Summary
SwOS is an operating system designed specifically for administration of MikroTik Switch products.
SwOS is configurable from your web browser. It gives you all the basic functionality for a managed switch, plus more: allows to manage port-to-port forwarding, broadcast storm control, apply MAC filter, configure VLANs, mirror traffic, apply bandwidth limitation and even adjust some MAC and IP header fields.

Warning: Each RouterBOARD switch series have their own firmware which cannot be installed on other series models! New RB260GS (CSS106-5G-1S), new RB260GSP(CSS106-1G-4P-1S) supports SwOS v2.0 and newer. When upgrading the device, it will first load primary firmware and then make an upgrade. In case a wrong firmware file is chosen, the device will continue to operate with primary firmware and you will be able to choose the correct file.
CSS106 series features
| Features | Description |
|---|---|
| Forwarding |
|
| Spanning Tree Protocol |
|
| Multicast Forwarding |
|
| Mirroring |
|
| VLAN |
|
| Quality of Service (QoS) |
|
| Access Control List |
|
Connecting to the Switch
Open your web browser and enter IP address of your Switch (192.168.88.1 by default) and login screen will appear.
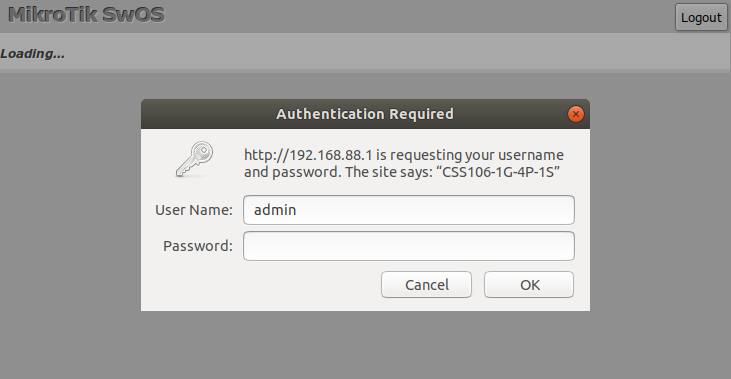
SwOS default IP address: 192.168.88.1, user name: admin and there is no password.

Note: MikroTik neighbor discovery protocol tools can be used to discover IP address of Mikrotik Switch. Manual:IP/Neighbor_discovery. Currently LLDP is not supported.
Interface Overview
SwOS interface menu consists of several tabs: Link, SFP, Forwarding, RST, Statistics, Errors, VLAN, VLANs, Hosts, IGMP Groups, SNMP, ACL, System and Upgrade.
Description of buttons in SwOS configuration tool:
- Append - add new item to the end of the list
- Apply All - applies current configuration changes
- Cut - removes item from the list
- Clear - resets properties of the item
- Discard Changes - removes unsaved configuration
- Insert - add new item to the list (places it before current item)
- Sort - sort VLAN table by VLAN-IDs; sort host table by MAC addresses
- Change Password - changes password of the switch
- Logout - logout from current Switch
- Reboot - reboot the switch
- Reset Configuration - reset configuration back to factory defaults
- Choose File - browse for upgrade or backup file
- Upgrade - upgrade firmware of the Switch
- Restore Backup - restore Switch using selected backup file
- Save Backup - generate and download backup file from the Switch
System
System Tab performs the following functions:
- General information about Switch
- Switch management
- Configuration reset
- Backup and restore configuration

Note: SwOS uses a simple algorithm to ensure TCP/IP communication - it just replies to the same IP and MAC address packet came from. This way there is no need for Default Gateway on the device itself.
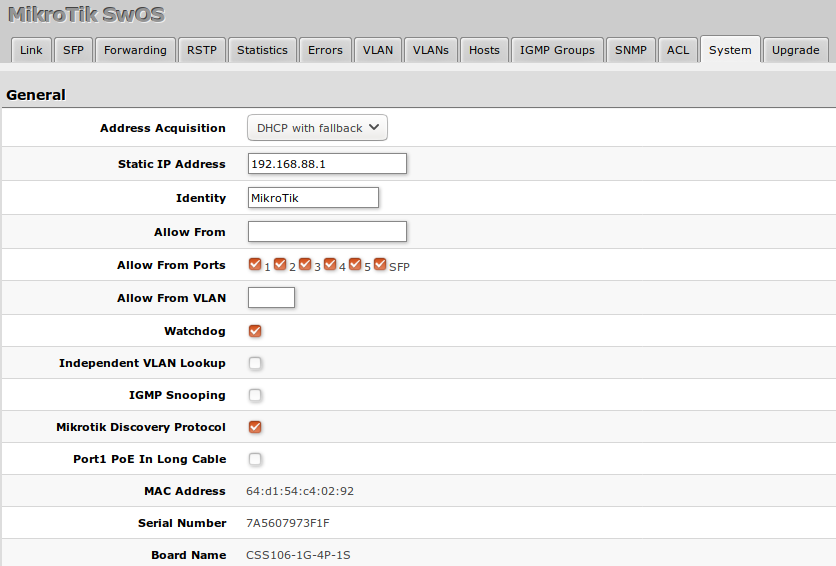
| Property | Description |
|---|---|
| Address Acquisition | Specify which address acquisition method to use:
|
| Static IP Address | IP address of the switch in case of Address Acquisition is set as DHCP with fallback or static |
| Identity | Name of the Switch (for Mikrotik neighbor discovery protocol) |
| Allow From | IP address from which the service is accessible. Default value is '0.0.0.0/0' - any address |
| Allow From Ports | List of switch ports from which the service is accessible |
| Allow From VLAN | VLAN ID with which the service is accessible (VLAN Mode on ingress port must be other than disabled in order to connect)
|
| Watchdog | Enable or disable system watchdog. It will reset CPU of the switch in case of fault condition |
| Independent VLAN Lookup | Enable or disable independent VLAN lookup in the Host table for packet forwarding |
| IGMP Snooping | Enable or disable IGMP Snooping |
| Mikrotik Discovery Protocol | Enable or disable Mikrotik neighbor discovery protocol |
| Port1 PoE In Long Cable | If enabled, it will turn off short detection on all PoE out ports to allow use of longer ethernet cables. This is potentially dangerous setting and should be used with caution. (CSS106-1G-4P-1S model) |
| MAC Address | MAC address of the Switch (Read-only) |
| Serial Number | Serial number of the switch (Read-only) |
| Board Name | MikroTik model name of the switch (CSS106 model, Read-only) |
Health (CSS106-1G-4P-1S)
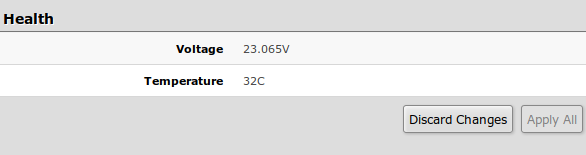
| Property | Description |
|---|---|
| Voltage | Shows the input voltage measured in volts |
| Temperature | Shows PCB temperature in celsius temperature scale |
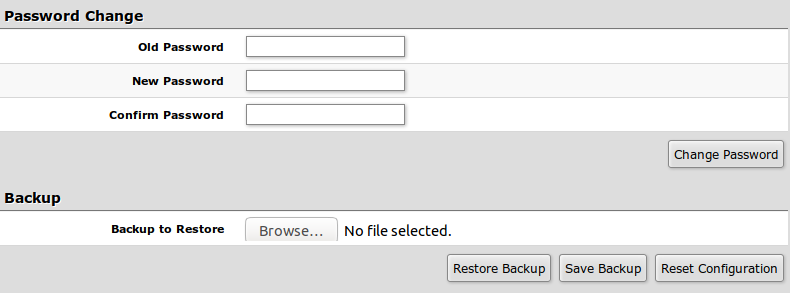
Password and Backup
Link
Link Tab allows you to:
- Configure Ethernet and SFP ports
- Monitor status of Ethernet and SFP ports
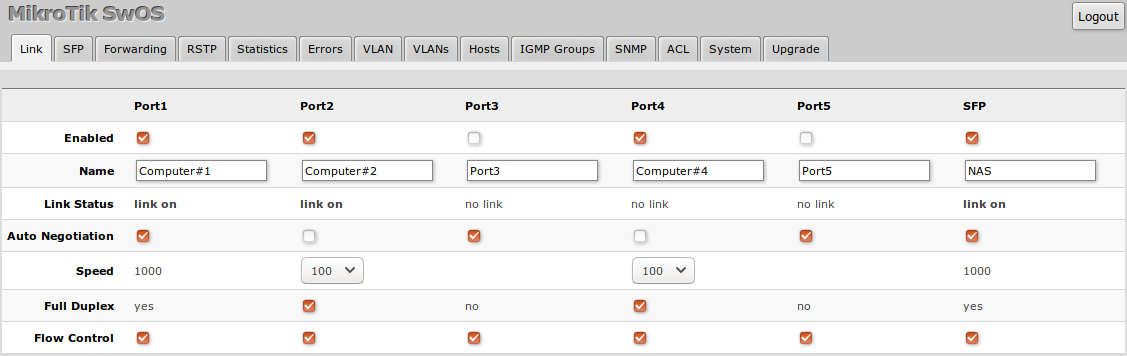
| Property | Description |
|---|---|
| Enabled | Enable or disable port |
| Name | Editable port name |
| Link Status | Current link status (Read-only) |
| Auto Negotiation | Enable or disable auto negotiation (some SFP modules may required it disabled in order to work) |
| Speed | Specify speed setting of the port (requires auto negotiation to be disabled) |
| Full Duplex | Specify duplex mode of the port (requires auto negotiation to be disabled) |
| Flow control | Enable or disable 802.3x Flow control |

Note: Using SFP+ 1m/3m DAC cable or S-RJ01 module, the device always shows that link is established even if nothing is connected on other end.
PoE (CSS106-1G-4P-1S)
PoE settings configure Power over Ethernet output on CSS106-1G-4P-1S port2-port5 and show PoE status and measurements.
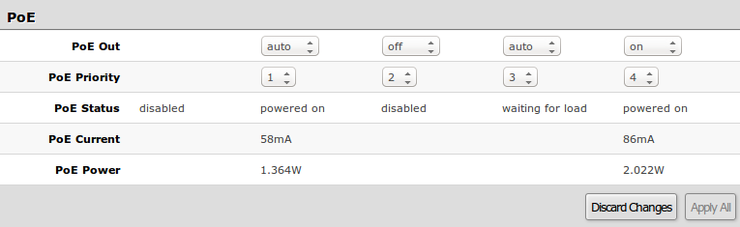
| Property | Description |
|---|---|
| PoE Out |
Sets PoE out mode of the port:
|
| PoE Priority | Port priority for PoE out supply. If installation is going over power budged, port with the lowest priority is going to be turned off first. 1 - the highest priority port; 4 - the lowest priority port |
| PoE Status |
Current PoE out status of the port:
|
| PoE Current | Shows current usage on the port measured in miliamperes |
| PoE Power | Shows PoE out power on the port measured in watts |
SFP
SFP tab allows you to monitor status of SFP modules.
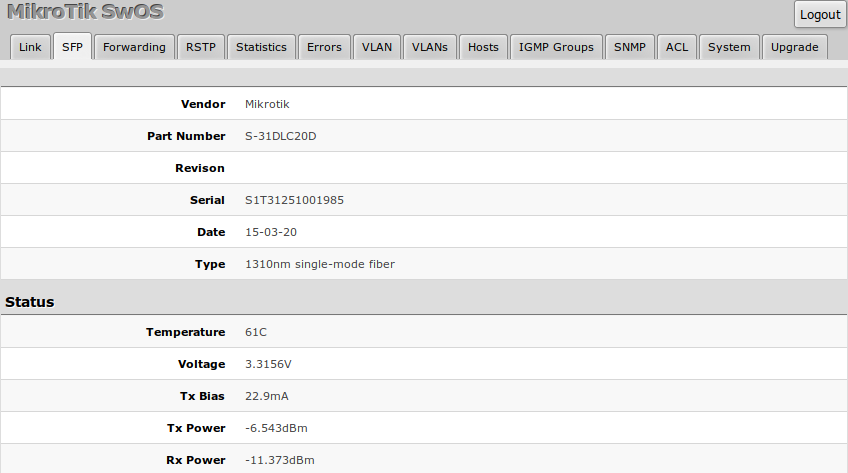
Forwarding
Forwarding Tab provides advanced forwarding options among switch ports, port isolation, port locking, port mirroring and egress bandwidth limit features.
Ingress rate per port as well as rate for broadcast traffic can be configured with Access Control List by setting Rate. ACL must have one port per entry to provide bandwidth limiting properly.
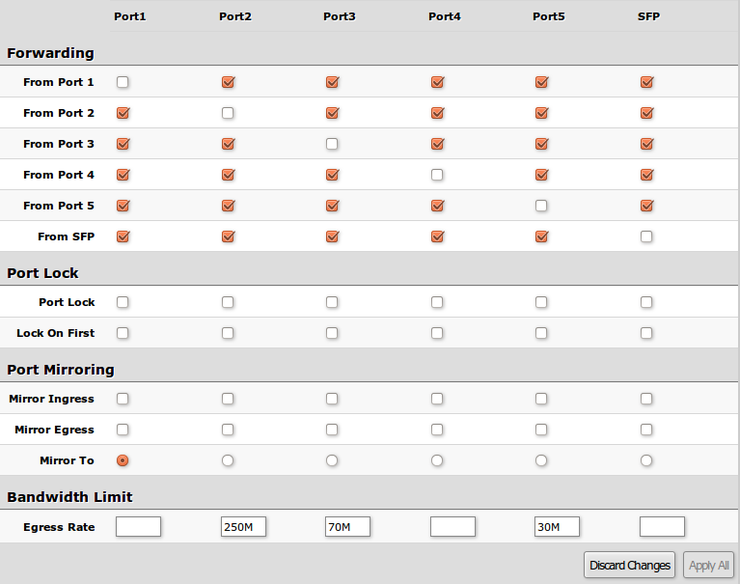
| Property | Description |
|---|---|
| Forwarding | Forwarding table - allows or restricts traffic flow between specific ports |
| Port Lock |
|
| Port Mirroring |
|
| Bandwidth Limit |
|
RSTP
Per port and global RSTP configuration and monitoring is available in the RSTP menu.
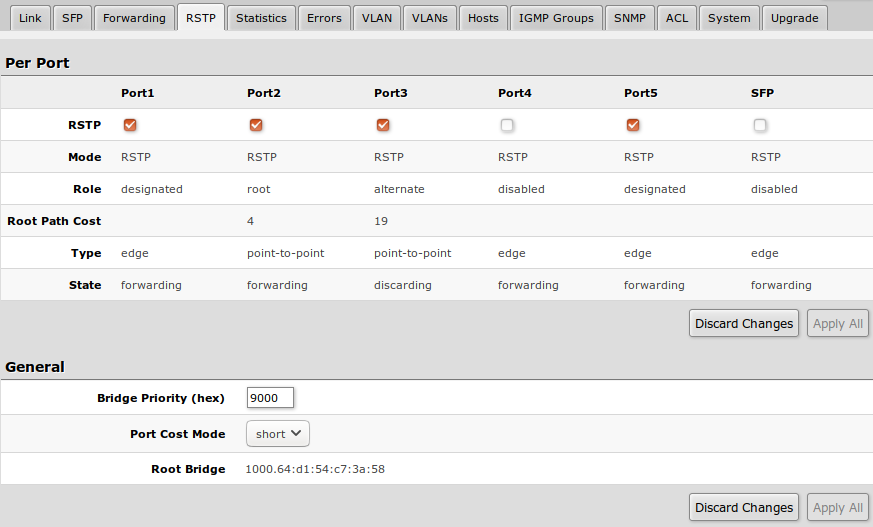
| Property | Description |
|---|---|
| RSTP | Enable or disable STP/RSTP functionality on this port |
| Mode | Shows STP/RSTP functionality mode on specific port (Read-only):
|
| Role | Shows specific port role (Read-only):
|
| Root Path Cost | Shows root path cost for ports that are facing root bridge (Read-only) |
| Type |
|
| State | Shows each port state (Read-only):
|
| Property | Description |
|---|---|
| Bridge Priority (hex) | RSTP bridge priority for Root Bridge selection |
| Port Cost Mode | There are two methods for automatically detecting RSTP port cost depending on link speed.
|
| Root Bridge | The priority and MAC address of the selected Root Bridge in the network (Read-only) |
Statistics, Errors
Provides detailed information about received and transmitted packets.
VLAN
VLAN configuration for Switch ports.
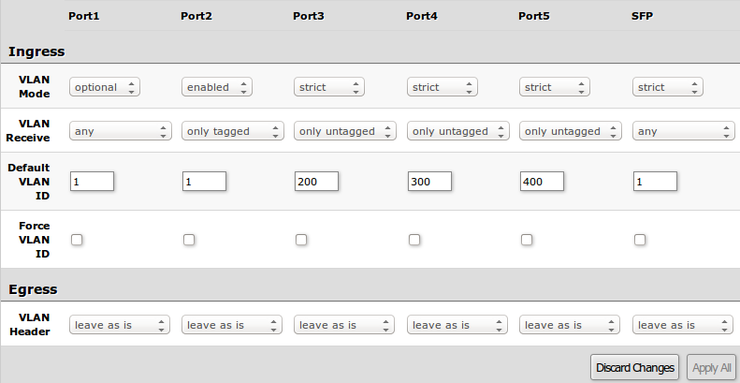
| Property | Description |
|---|---|
| VLAN Mode |
VLAN mode for ingress port:
|
| VLAN Receive | Defines the type of allowed packets on ingress port:
|
| Default VLAN ID | Switch will treat both untagged and "Default VLAN ID" tagged ingress packets as they are tagged with this VLAN ID. It is also used to untag egress traffic if packet's VLAN ID matches "Default VLAN ID". The VLAN tag itself will only be added if there is VLAN Header = add if missing specified on egress port |
| Force VLAN ID | Whether to apply Default VLAN ID to incoming packets with VLAN tag |
| VLAN Header |
|

Note: VLAN modes enabled and strict require VLAN ID 1 in VLANs table to allow access of untagged traffic to switch itself.
VLAN Configuration Examples
Simple trunk and access port configuration, as well as trunk and hybrid port configuration examples can be found in this article - SwOS/CSS106-VLAN-Example.
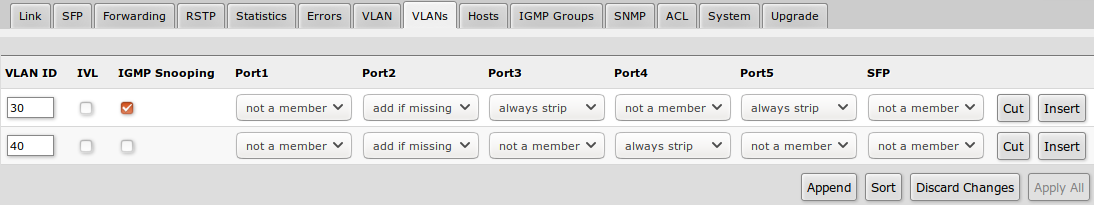
VLANs
VLAN tables specifies certain forwarding rules for packets that have specific IEEE 802.1Q tag. Basically the table contains entries that map specific VLAN tag IDs to a group of one or more ports. Packets with VLAN tags leave switch through one or more ports that are set in corresponding table entry. VLAN table works together with destination MAC lookup to determine egress ports. VLAN table supports up to 250 entries.
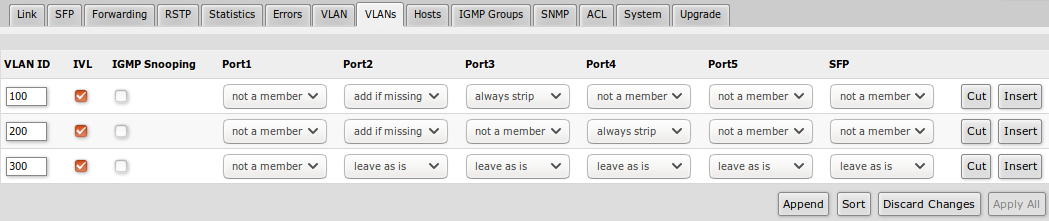
| Property | Description |
|---|---|
| VLAN ID | VLAN ID of the packet |
| IVL | Enables or disables independent VLAN learning (IVL) |
| IGMP Snooping | Enables or disables IGMP Snooping on the defined VLAN. When enabled, the switch will listen to IGMP Join and Leave requests from the defined VLAN and only forward traffic to ports, which have sent IGMP membership requests from the defined VLAN. When disabled, the switch will flood all VLAN member ports with Multicast traffic. |
| Ports | Each port has individual VLAN header options for each VLAN ID. Depending on VLAN mode if lookup is done in this table, egress action of packets is processed by this option. Egress option from VLAN tab is ignored. |
Hosts
This table represents dynamically learnt MAC address to port mapping entries. It can contain two kinds of entries: dynamic and static. Dynamic entries get added automatically, this is also called a learning process: when switch receives a packet from certain port, it adds the packet's source MAC address X and port it received the packet from to host table, so when a packet comes in with destination MAC address X it knows to which port it should forward the packet. If the destination MAC address is not present in host table then it forwards the packet to all ports in the group. Dynamic entries take about 5 minutes to time out.
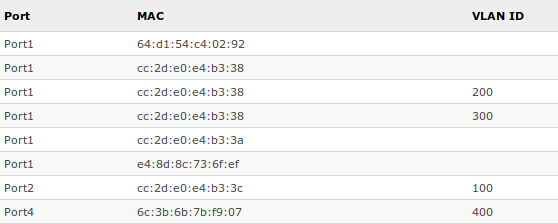
| Property | Description |
|---|---|
| Port | Ports the packet should be forwarded to (Read-only) |
| MAC | Learned MAC address (Read-only) |
| VLAN ID | Learned VLAN ID (Read-only) |
Static Hosts
Static entries will take over dynamic if dynamic entry with same mac-address already exists. Also by adding a static entry you get access to some more functionality.
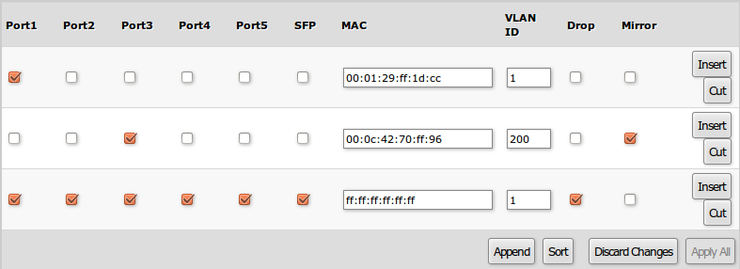
| Property | Description |
|---|---|
| Ports | Ports the packet should be forwarded to |
| MAC | MAC address |
| VLAN ID | VLAN ID (only supported on RB260GS/RB260GSP) |
| Drop | Packet with certain MAC address coming from certain ports can be dropped |
| Mirror | Packet can be cloned and sent to mirror-target port |
IGMP Groups
IGMP Snooping which controls multicast streams and prevents multicast flooding is implemented in SwOS starting from version 2.5. The feature allows a switch to listen in the IGMP conversation between hosts and routers.
First, enable option under System tab.
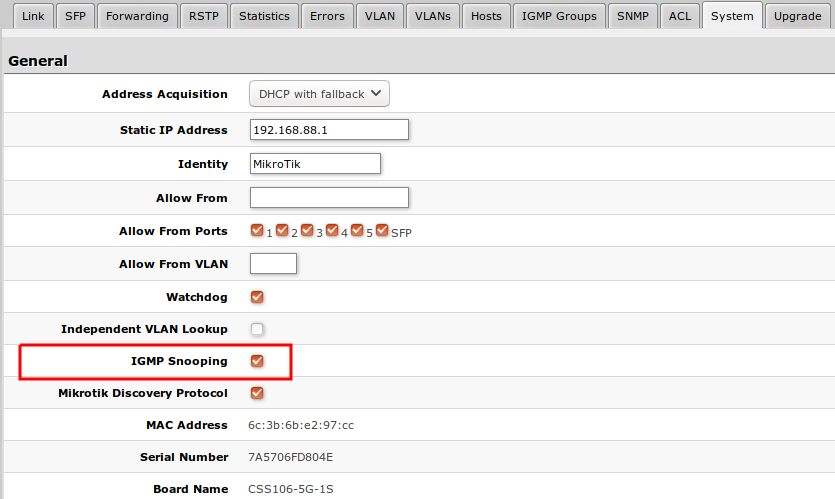
Available IGMP snooping data can be found under IGMP Group tab:
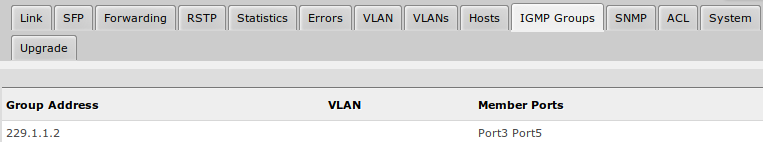
Possibility to enable IGMP Snooping for specific VLAN ID.
SNMP
SwOS supports SNMP v1 and uses IF-MIB, SNMPv2-MIB, BRIDGE-MIB and MIKROTIK-MIB (only for health, PoE-out and SFP diagnostics) for SNMP reporting.
Available SNMP data:
System informationSystem uptimePort statusInterface statisticsHost table information
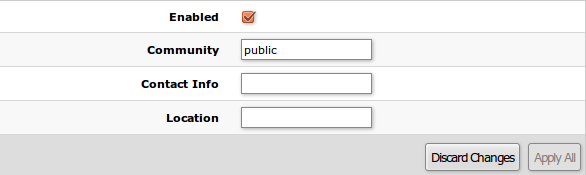
| Property | Description |
|---|---|
| Enabled | Enable or disable SNMP service |
| Community | SNMP community name |
| Contact Info | Contact information for the NMS |
| Location | Location information for the NMS |
ACL
An access control list (ACL) rule table is very powerful tool allowing wire speed packet filtering, forwarding and VLAN tagging based on L2,L3 protocol header field conditions. SwOS allow you to implement limited number of access control list rules (32 simple rules (only L2 conditions are used); 16 rules where both L2 and L3 conditions are used; or 8 advanced rules where all L2,L3 and L4 conditions are used). Each rule contains a conditions part and an action part.
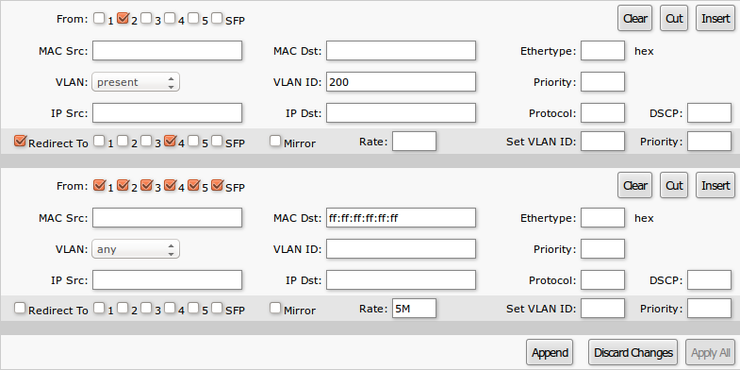
Conditions part parameters
| Property | Description |
|---|---|
| From | Port that packet came in from |
| MAC Src | Source MAC address and mask |
| MAC Dst | Destination MAC address and mask |
| Ethertype | Protocol encapsulated in the payload of an Ethernet Frame |
| VLAN |
VLAN header presence:
|
| VLAN ID | VLAN tag ID |
| Priority | Priority in VLAN tag |
| IP Src (IP/netmask:port) | Source IPv4 address, netmask and L4 port number |
| IP Dst (IP/netmask:port) | Destination IPv4 address, netmask and L4 port number |
| Protocol | IP protocol |
| DSCP | IP DSCP field |
Action part parameters
| Property | Description |
|---|---|
| Redirect To | Whether to force new destination ports (If Redirect To is enabled and no ports specified in Redirect To Ports, packet will be dropped ) |
| Redirect To Ports | Destination ports for |
| Mirror | Clones packet and sends it to mirror-target port |
| Rate | Limits bandwidth (bps) |
| Set VLAN ID | Changes the VLAN tag ID, if VLAN tag is present |
| Priority | Changes the VLAN tag priority bits, if VLAN tag is present |
Reset
The CSS106-5G-1S and CSS106-1G-4P-1S has built-in backup SwOS firmware which can be loaded in case standard firmware breaks or upgrade fails:
- Holding Reset button for few seconds while device is booting resets configuration and loads backup firmware SwOS 2.0p.
- After loading backup firmware SwOS 2.0p it is possible to connect to 192.168.88.1 using web browser and install new SwOS firmware.