Manual:Switch Router: Difference between revisions
Created page with "{{Versions| v6.41 +}} __TOC__ Many MikroTik's devices come with a built-in switch chip that can be used to greatly improve overall throughput when configured properly. Devic..." |
No edit summary |
||
| (6 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
{{Versions| v6.41 +}} | {{Versions| v6.41 +}} | ||
{{Warning|This manual is moved to https://help.mikrotik.com/docs/display/ROS/Switch+Chip+Features#SwitchChipFeatures-Inter-VLANrouting}} | |||
__TOC__ | __TOC__ | ||
| Line 9: | Line 11: | ||
{{Warning | Not all devices are designed to handle large amounts of traffic through the CPU, for this reason be very careful when designing your network since large amounts of traffic that are passing through the CPU will overload it. Functions that depend on the CPU (for example, NAT and DHCP) will not work properly when the CPU is overloaded.}} | {{Warning | Not all devices are designed to handle large amounts of traffic through the CPU, for this reason be very careful when designing your network since large amounts of traffic that are passing through the CPU will overload it. Functions that depend on the CPU (for example, NAT and DHCP) will not work properly when the CPU is overloaded.}} | ||
{{ Note | This guide is meant for devices that have a switch chip and are capable of using the switch chip's VLAN table, make sure that your device has hardware support for this feature, feature list per switch chip can be found [[Manual:Switch_Chip_Features#Introduction | here]]. For CRS series devices you should check the [[Manual:CRS_Router | CRS Router]] guide.}} | {{ Note | This guide is meant for devices that have a switch chip and are capable of using the switch chip's VLAN table, make sure that your device has hardware support for this feature, feature list per switch chip can be found [[Manual:Switch_Chip_Features#Introduction | here]]. For CRS series devices you should check the [[Manual:CRS_Router | CRS Router]] guide, this guide should be used for devices that don't have a built-in switch chip as well (should be configured like CRS3xx series switches). }} | ||
=Port switching= | =Port switching= | ||
| Line 16: | Line 18: | ||
<pre> | <pre> | ||
/interface bridge | /interface bridge | ||
add name=bridge1 | add name=bridge1 | ||
/interface bridge port | /interface bridge port | ||
add bridge=bridge1 interface=ether2 | add bridge=bridge1 interface=ether2 hw=yes | ||
add bridge=bridge1 interface=ether3 | add bridge=bridge1 interface=ether3 hw=yes | ||
</pre> | </pre> | ||
{{ Note | By default, the bridge interface is configured with <var>protocol-mode</var> set to <code>rstp</code>. For some devices, this can disable hardware offloading because specific switch chips do not support this feature. See the [[Manual:Interface/Bridge#Bridge_Hardware_Offloading | Bridge Hardware Offloading]] section with supported features. }} | |||
=DHCP and NAT= | =DHCP and NAT= | ||
| Line 53: | Line 57: | ||
=VLAN switching= | =VLAN switching= | ||
Add each port to the VLAN table and allow these ports to access the CPU in order to make DHCP and routing | Add each port to the VLAN table and allow these ports to access the CPU in order to make DHCP and routing work: | ||
<pre> | <pre> | ||
/interface ethernet switch vlan | /interface ethernet switch vlan | ||
| Line 69: | Line 73: | ||
=Isolated VLANs= | =Isolated VLANs= | ||
If your device has a rule table, then you can limit access between VLANs on a hardware level. As soon as you add an IP address on the VLAN interface you enable interVLAN routing, but this can be limited on a hardware level yet preserving DHCP Server and other router related services' functionality. To do so, use these ACL rules: | |||
<pre> | <pre> | ||
/interface ethernet switch rule | /interface ethernet switch rule | ||
Latest revision as of 15:37, 26 May 2022

Warning: This manual is moved to https://help.mikrotik.com/docs/display/ROS/Switch+Chip+Features#SwitchChipFeatures-Inter-VLANrouting
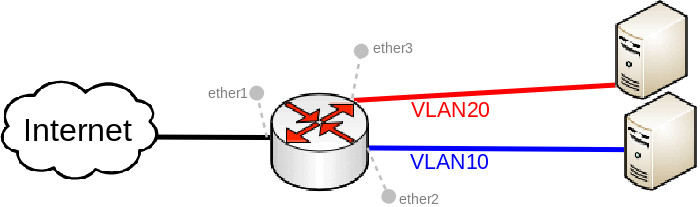
Many MikroTik's devices come with a built-in switch chip that can be used to greatly improve overall throughput when configured properly. Devices with a switch chip can be used as a router and a switch at the same time, this gives you the possibility to use a single device instead of multiple devices for your network.

Warning: Not all devices are designed to handle large amounts of traffic through the CPU, for this reason be very careful when designing your network since large amounts of traffic that are passing through the CPU will overload it. Functions that depend on the CPU (for example, NAT and DHCP) will not work properly when the CPU is overloaded.

Note: This guide is meant for devices that have a switch chip and are capable of using the switch chip's VLAN table, make sure that your device has hardware support for this feature, feature list per switch chip can be found here. For CRS series devices you should check the CRS Router guide, this guide should be used for devices that don't have a built-in switch chip as well (should be configured like CRS3xx series switches).
Port switching
For this type of setup to work, you must switch all required ports together:
/interface bridge add name=bridge1 /interface bridge port add bridge=bridge1 interface=ether2 hw=yes add bridge=bridge1 interface=ether3 hw=yes

Note: By default, the bridge interface is configured with protocol-mode set to rstp. For some devices, this can disable hardware offloading because specific switch chips do not support this feature. See the Bridge Hardware Offloading section with supported features.
DHCP and NAT
Create a VLAN interface for each VLAN ID and assign an IP address on it:
/interface vlan add interface=bridge1 name=VLAN10 vlan-id=10 add interface=bridge1 name=VLAN20 vlan-id=20 /ip address add address=192.168.10.1/24 interface=VLAN10 add address=192.168.20.1/24 interface=VLAN20
Setup a DHCP Server for each VLAN:
/ip pool add name=POOL10 ranges=192.168.10.100-192.168.10.200 add name=POOL20 ranges=192.168.20.100-192.168.20.200 /ip dhcp-server add address-pool=POOL10 disabled=no interface=VLAN10 name=DHCP10 add address-pool=POOL20 disabled=no interface=VLAN20 name=DHCP20 /ip dhcp-server network add address=192.168.10.0/24 dns-server=8.8.8.8 gateway=192.168.10.1 add address=192.168.20.0/24 dns-server=8.8.8.8 gateway=192.168.20.1
Enable NAT on the device:
/ip firewall nat add action=masquerade chain=srcnat out-interface=ether1
VLAN switching
Add each port to the VLAN table and allow these ports to access the CPU in order to make DHCP and routing work:
/interface ethernet switch vlan add independent-learning=yes ports=ether2,switch1-cpu switch=switch1 vlan-id=10 add independent-learning=yes ports=ether3,switch1-cpu switch=switch1 vlan-id=20
Specify each port to be as an access port, enable secure VLAN mode on each port and on the switch1-cpu port:
/interface ethernet switch port set ether2 default-vlan-id=10 vlan-header=always-strip vlan-mode=secure set ether3 default-vlan-id=20 vlan-header=always-strip vlan-mode=secure set switch1-cpu vlan-mode=secure
Isolated VLANs
If your device has a rule table, then you can limit access between VLANs on a hardware level. As soon as you add an IP address on the VLAN interface you enable interVLAN routing, but this can be limited on a hardware level yet preserving DHCP Server and other router related services' functionality. To do so, use these ACL rules:
/interface ethernet switch rule add dst-address=192.168.20.0/24 new-dst-ports="" ports=ether2 switch=switch1 add dst-address=192.168.10.0/24 new-dst-ports="" ports=ether3 switch=switch1
And you are done! With this type of configuration you can achieve isolated port groups using VLANs.
[ Top | Back to Content ]
