Manual:MPLS L2VPN vs Juniper: Difference between revisions
| (17 intermediate revisions by the same user not shown) | |||
| Line 11: | Line 11: | ||
We will be setting up the layer 2 connection between the CE and PE routers as well as the MPLS and L2VPN between PE routers. The layer 2 link between the CE and PE routers will be an Ethernet VLAN circuit. | We will be setting up the layer 2 connection between the CE and PE routers as well as the MPLS and L2VPN between PE routers. The layer 2 link between the CE and PE routers will be an Ethernet VLAN circuit. | ||
===LDP based VPN=== | |||
====Set up VLANs==== | |||
:'''CE1''' and '''CE2''' routers: | |||
<pre> | |||
/interface vlan | |||
add vlan-id=600 name=vlan1 disabled=no interface=ether1 | |||
</pre> | |||
PE1 RouterOS: | :'''PE1''' (RouterOS): | ||
No configuration currently is needed, later we will bridge VPLS tunnel. | |||
PE1 (RouterOS): | :'''PE2''' (JunOS): | ||
<pre> | |||
interfaces { | |||
fe-0/0/1 { | |||
vlan-tagging; | |||
encapsulation vlan-ccc; | |||
unit 1 { | |||
encapsulation vlan-ccc; | |||
vlan-id 600; | |||
} | |||
} | |||
} | |||
</pre> | |||
====Set up IP connection, OSPF and LDP==== | |||
:CE1: | |||
/ip address add address=192.168.88.1/24 interface=vlan1 | |||
:CE2: | |||
/ip address add address=192.168.88.2/24 interface=vlan1 | |||
:'''PE1''' (RouterOS): | |||
<pre> | <pre> | ||
/interface bridge | /interface bridge | ||
| Line 41: | Line 68: | ||
</pre> | </pre> | ||
P (RouterOS): | |||
:'''P''' (RouterOS): | |||
<pre> | <pre> | ||
/interface bridge | /interface bridge | ||
| Line 64: | Line 92: | ||
</pre> | </pre> | ||
PE2 (JunOS): | |||
:'''PE2''' (JunOS): | |||
<pre> | <pre> | ||
interfaces { | interfaces { | ||
| Line 123: | Line 152: | ||
</pre> | </pre> | ||
===Set up L2VPN=== | ====Set up L2VPN==== | ||
PE1 RouterOS: | :'''PE1''' (RouterOS): | ||
<pre> | <pre> | ||
/interface vpls | /interface vpls | ||
| Line 131: | Line 160: | ||
remote-peer=10.255.11.201 | remote-peer=10.255.11.201 | ||
/interface bridge add name=vpn | |||
/interface bridge port | |||
add interface=ether5 bridge=vpn | |||
add interface=junos-l2circuit bridge=vpn | |||
</pre> | </pre> | ||
PE2 | |||
We need to set pw-type='''tagged-ethernet''' since on juniper encapsulation was set to '''vlan-ccc'''. Otherwise Juniper will throw an error ''/EM -- encapsulation mismatch /'' | |||
:'''PE2''' (JunOS): | |||
<pre> | <pre> | ||
protocol { | protocol { | ||
| Line 145: | Line 183: | ||
</pre> | </pre> | ||
===Verify Operation=== | ====Verify Operation==== | ||
'''Verify if LDP neighbors are found and forwarding table is created:''' | |||
PE2: | :'''PE1''': | ||
<pre> | |||
[admin@10.0.11.31] /mpls ldp neighbor> print | |||
Flags: X - disabled, D - dynamic, O - operational, T - sending-targeted-hello, | |||
V - vpls | |||
# TRANSPORT LOCAL-TRANSPORT PEER SEN | |||
0 DO 10.255.11.23 10.255.11.31 10.255.11.23:0 no | |||
1 DOTV 10.255.11.201 10.255.11.31 10.255.11.201:0 yes | |||
</pre> | |||
<pre> | |||
[admin@10.0.11.31] /mpls forwarding-table> print | |||
Flags: L - ldp, V - vpls, T - traffic-eng | |||
# IN-LABEL OUT-LABELS DESTINATION I NEXTHOP | |||
0 expl-null | |||
1 L 17 3396 10.255.11.201/32 e 192.168.168.1 | |||
2 L 19 10.255.11.23/32 e 192.168.168.1 | |||
3 L 23 3390 10.5.101.0/24 e 192.168.168.1 | |||
4 V 29 junos-l2circuit | |||
</pre> | |||
:'''PE2''': | |||
<pre> | |||
juniper@J4300> show ldp neighbor | |||
Address Interface Label space ID Hold time | |||
10.255.11.31 lo0.0 10.255.11.31:0 42 | |||
10.0.11.23 fe-0/0/0.0 10.255.11.23:0 13 | |||
</pre> | |||
'''Verify traffic forwarding over LSP:''' | |||
:'''PE1''': | |||
<pre> | |||
[admin@10.0.11.31] /interface vpls> /tool traceroute 10.255.11.201 | |||
# ADDRESS RT1 RT2 RT3 STATUS | |||
1 192.168.168.1 1ms 1ms 1ms <MPLS:L=3396,E=0> | |||
2 10.255.11.201 2ms 3ms 3ms | |||
</pre> | |||
'''Verify if L2VPN tunnel is up and running:''' | |||
:'''PE1''' | |||
<pre> | |||
[admin@10.0.11.31] /interface vpls> monitor junos-l2circuit once | |||
remote-label: 577168 | |||
local-label: 29 | |||
remote-status: | |||
transport: 10.255.11.201/32 | |||
transport-nexthop: 192.168.168.1 | |||
imposed-labels: 3396,577168 | |||
</pre> | |||
:'''PE2''' | |||
<pre> | |||
juniper@J4300> show l2circuit connections | |||
Layer-2 Circuit Connections: | |||
Legend for connection status (St) | |||
EI -- encapsulation invalid NP -- interface h/w not present | |||
MM -- mtu mismatch Dn -- down | |||
EM -- encapsulation mismatch VC-Dn -- Virtual circuit Down | |||
CM -- control-word mismatch Up -- operational | |||
VM -- vlan id mismatch CF -- Call admission control failure | |||
OL -- no outgoing label IB -- TDM incompatible bitrate | |||
NC -- intf encaps not CCC/TCC TM -- TDM misconfiguration | |||
BK -- Backup Connection ST -- Standby Connection | |||
CB -- rcvd cell-bundle size bad XX -- unknown | |||
Legend for interface status | |||
Up -- operational | |||
Dn -- down | |||
Neighbor: 10.255.11.31 | |||
Interface Type St Time last up # Up trans | |||
fe-0/0/1.1(vc 5) rmt Up Apr 19 12:28:30 2012 2 | |||
Remote PE: 10.255.11.31, Negotiated control-word: No | |||
Incoming label: 577168, Outgoing label: 29 | |||
Local interface: fe-0/0/1.1, Status: Up, Encapsulation: VLAN | |||
juniper@J4300> | |||
</pre> | |||
===BGP Based VPN=== | |||
Lets consider that we have the same network layout as in [[#LDP based VPN | LDP based lab]] and lets assume that IP connectivity, OSPF and LDP are already set up. | |||
In this case we will not use vlans. | |||
First thing to do is to set up BGP peers and then we can add L2VPN configuration. | |||
====Adjust MTUs==== | |||
On RouterOS we do not adjust L2MTU values since I am using RouterBoards that has L2MTU set to 1632 by default. Only MPLS MTU is adjusted. | |||
:'''PE1''' (RouterOS): | |||
<pre> | |||
/mpls interface set 0 mpls-mtu=1526 | |||
</pre> | |||
:'''P''' (RouterOS): | |||
<pre> | |||
/mpls interface set 0 mpls-mtu=1526 | |||
</pre> | |||
On Juniper router we will adjust L2MTU to 1600 and MPLS MTU to 1526 on interface running MPLS. | |||
We will also set up L2MTU to 1514 on cross circuit interface and set encapsulation to ethernet. | |||
:'''PE2''' (JunOS): | |||
<pre> | |||
interfaces { | |||
fe-0/0/0 { | |||
mtu 1600; | |||
unit 0 { | |||
family inet { | |||
mtu 1500; | |||
address 10.0.11.201/24; | |||
} | |||
family mpls { | |||
mtu 1526; | |||
} | |||
} | |||
} | |||
fe-0/0/1 { | |||
mtu 1514; | |||
encapsulation ethernet-ccc; | |||
unit 0 { | |||
family ccc; | |||
} | |||
} | |||
} | |||
</pre> | |||
====Set up BGP==== | |||
:'''PE1''' (RouterOS): | |||
<pre> | |||
/routing bgp instance | |||
set default as=64201 router-id=10.255.11.31 | |||
/routing bgp peer | |||
add address-families=l2vpn name=juniper remote-address=10.255.11.201 \ | |||
remote-as=64201 ttl=default | |||
</pre> | |||
:'''PE2''' (JunOS): | |||
<pre> | |||
routing-options { | |||
router-id 10.255.11.201; | |||
autonomous-system 64201; | |||
} | |||
protocol { | |||
bgp { | |||
log-updown; | |||
group int { | |||
type internal; | |||
local-address 10.255.11.201; | |||
import match-all; | |||
family l2vpn { | |||
signaling; | |||
} | |||
export match-all; | |||
neighbor 10.255.11.31; | |||
} | |||
} | |||
} | |||
policy-options { | |||
policy-statement match-all { | |||
term acceptable { | |||
then accept; | |||
} | |||
} | |||
} | |||
</pre> | |||
====Set up L2VPN==== | |||
:'''PE1''' (RouterOS): | |||
<pre> | |||
/interface bridge | |||
add ame=vpn | |||
/interface bridge port | |||
add interface=ether5 bridge=vpn | |||
/interface vpls bgp-vpls | |||
add bridge=vpn bridge-cost=0 export-route-targets=1:1 \ | |||
import-route-targets=1:1 name=juniper-l2vpn pw-type=tagged-ethernet \ | |||
route-distinguisher=1:1 site-id=20 use-control-word=no | |||
</pre> | |||
{{Note | Parameter '''pw-type''' is available starting from v5.16. It allows to choose advertised encapsulation in NLRI used only for comparison. Available options are raw-ethernet (5), tagged-ethernet (4) and vpls (19) which is default setting and was hard coded in previous versions.}} | |||
:'''PE2''' (JunOS): | |||
At first we define what is allowed to import and export by routing instance: | |||
<pre> | |||
policy-options { | |||
policy-statement vpn-SPA-export { | |||
term a { | |||
then { | |||
community add SPA-com; | |||
accept; | |||
} | |||
} | |||
term b { | |||
then reject; | |||
} | |||
} | |||
policy-statement vpn-SPA-import { | |||
term a { | |||
from { | |||
protocol bgp; | |||
community SPA-com; | |||
} | |||
then accept; | |||
} | |||
term b { | |||
then reject; | |||
} | |||
} | |||
community SPA-com members target:1:1; | |||
} | |||
</pre> | |||
Now we can add L2VPN routing instance: | |||
<pre> | |||
routing-instances { | |||
vpls1 { | |||
instance-type l2vpn; | |||
interface fe-0/0/1.0; | |||
route-distinguisher 1:1; | |||
vrf-import [ match-all vpn-SPA-import ]; | |||
vrf-export vpn-SPA-export; | |||
protocols { | |||
l2vpn { | |||
traceoptions { | |||
file VPLS-TEST size 100000 files 7; | |||
flag all; | |||
} | |||
encapsulation-type ethernet; | |||
no-control-word; | |||
site c2 { | |||
site-identifier 21; | |||
interface fe-0/0/1.0 { | |||
remote-site-id 20; | |||
} | |||
} | |||
} | |||
} | |||
} | |||
} | |||
</pre> | |||
{{ Note | By setting '''encapsulation-type''' (pw-type on RouterOS). Does not change actual encapsulation. It is also possible that configured encapsulation types do not match on both ends. In this case you can use '''ignore-encapsulation-mismatch''' on Juniper routers.}} | |||
In this configuration we also have disabled Cotrol Word usage with '''no-control-word''' on JunOS and '''use-control-word=no''' on RouterOS. | |||
====Verify Operation==== | |||
'''Verify if BGP peer is up''' | |||
:'''PE1''' (RouterOS): | |||
<pre> | |||
[admin@10.0.11.31] /routing bgp peer> print status | |||
Flags: X - disabled, E - established | |||
0 E name="juniper" instance=default remote-address=10.255.11.201 | |||
remote-as=64201 tcp-md5-key="" nexthop-choice=default multihop=no | |||
route-reflect=no hold-time=3m ttl=default in-filter="" out-filter="" | |||
address-families=l2vpn default-originate=never remove-private-as=no | |||
as-override=no passive=no use-bfd=no remote-id=10.255.11.201 | |||
local-address=10.255.11.31 uptime=1h1m26s prefix-count=0 updates-sent=1 | |||
updates-received=1 withdrawn-sent=0 withdrawn-received=0 | |||
remote-hold-time=1m30s used-hold-time=1m30s used-keepalive-time=30s | |||
refresh-capability=yes as4-capability=yes state=established | |||
</pre> | |||
:'''PE2''' (JunOS): | |||
<pre> | |||
juniper@J4300> show bgp summary | |||
Groups: 3 Peers: 4 Down peers: 3 | |||
Table Tot Paths Act Paths Suppressed History Damp State Pending | |||
inet.0 0 0 0 0 0 0 | |||
bgp.l2vpn.0 1 1 0 0 0 0 | |||
Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Rec... | |||
10.255.11.31 64201 148 152 0 2 59:56 Establ | |||
bgp.l2vpn.0: 1/1/1/0 | |||
vpls1.l2vpn.0: 1/1/1/0 | |||
</pre> | |||
'''Verify if L2VPN tunnel is created''' | |||
:'''PE1''' (RouterOS): | |||
<pre> | |||
[admin@10.0.11.31] /interface vpls> print | |||
Flags: X - disabled, R - running, D - dynamic, | |||
B - bgp-signaled, C - cisco-bgp-signaled | |||
0 RDB name="vpls2" mtu=1500 l2mtu=1500 mac-address=02:04:3F:CD:06:97 | |||
arp=enabled disable-running-check=no remote-peer=10.255.11.201 | |||
cisco-style=no cisco-style-id=0 advertised-l2mtu=1500 | |||
pw-type=raw-ethernet vpls=juniper-l2vpn | |||
[admin@10.0.11.31] /interface vpls> monitor 0 | |||
remote-label: 800021 | |||
local-label: 27 | |||
remote-status: | |||
transport: 10.255.11.201/32 | |||
transport-nexthop: 10.0.11.201 | |||
imposed-labels: 800021 | |||
</pre> | |||
:'''PE2''' (JunOS): | |||
<pre> | |||
juniper@J4300> show l2vpn connections extensive | |||
Layer-2 VPN connections: | |||
Legend for connection status (St) | |||
EI -- encapsulation invalid NC -- interface encapsulation not CCC/TCC/VPLS | |||
EM -- encapsulation mismatch WE -- interface and instance encaps not same | |||
VC-Dn -- Virtual circuit down NP -- interface hardware not present | |||
CM -- control-word mismatch -> -- only outbound connection is up | |||
CN -- circuit not provisioned <- -- only inbound connection is up | |||
OR -- out of range Up -- operational | |||
OL -- no outgoing label Dn -- down | |||
LD -- local site signaled down CF -- call admission control failure | |||
RD -- remote site signaled down SC -- local and remote site ID collision | |||
LN -- local site not designated LM -- local site ID not minimum designated | |||
RN -- remote site not designated RM -- remote site ID not minimum designated | |||
XX -- unknown connection status IL -- no incoming label | |||
MM -- MTU mismatch MI -- Mesh-Group ID not availble | |||
BK -- Backup connection ST -- Standby connection | |||
Legend for interface status | |||
Up -- operational | |||
Dn -- down | |||
Instance: vpls1 | |||
Local site: c2 (21) | |||
Number of local interfaces: 1 | |||
Number of local interfaces up: 1 | |||
fe-0/0/1.1 20 | |||
Label-base Offset Range Preference | |||
800020 19 2 100 | |||
status-vector: 80 | |||
connection-site Type St Time last up # Up trans | |||
20 rmt Up Apr 24 07:30:50 2012 1 | |||
Remote PE: 10.255.11.31, Negotiated control-word: No | |||
Incoming label: 800021, Outgoing label: 27 | |||
Local interface: fe-0/0/1.0, Status: Up, Encapsulation: ETHERNET | |||
Connection History: | |||
Apr 24 07:30:50 2012 status update timer | |||
Apr 24 07:30:50 2012 PE route changed | |||
Apr 24 07:30:50 2012 Out lbl Update 27 | |||
Apr 24 07:30:50 2012 In lbl Update 800021 | |||
Apr 24 07:30:50 2012 loc intf up fe-0/0/1.1 | |||
juniper@J4300> | |||
</pre> | |||
==See Also== | ==See Also== | ||
| Line 155: | Line 573: | ||
* [[M:BGP_based_VPLS | BGP Based VPLS]] | * [[M:BGP_based_VPLS | BGP Based VPLS]] | ||
* [[M:Cisco_VPLS | Cisco style VPLS]] | * [[M:Cisco_VPLS | Cisco style VPLS]] | ||
* [[M:EoMPLS_vs_Cisco | EoMPLS vs Cisco configuration example]] | |||
[[Category:Routing|B]] | [[Category:Routing|B]] | ||
Latest revision as of 13:38, 25 May 2012
Summary
This article describes the basic setup of Point-to-Point L2VPN with Juniper J-series routers.
Configuration
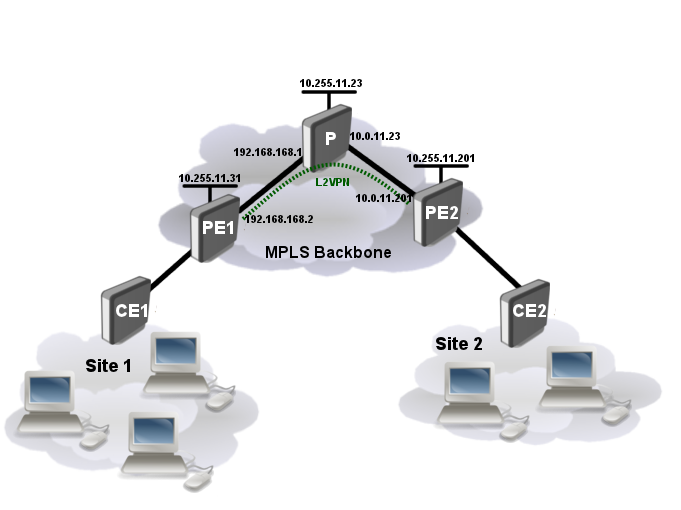
Consider network setup as ilustrated below:
We will be setting up the layer 2 connection between the CE and PE routers as well as the MPLS and L2VPN between PE routers. The layer 2 link between the CE and PE routers will be an Ethernet VLAN circuit.
LDP based VPN
Set up VLANs
- CE1 and CE2 routers:
/interface vlan add vlan-id=600 name=vlan1 disabled=no interface=ether1
- PE1 (RouterOS):
No configuration currently is needed, later we will bridge VPLS tunnel.
- PE2 (JunOS):
interfaces {
fe-0/0/1 {
vlan-tagging;
encapsulation vlan-ccc;
unit 1 {
encapsulation vlan-ccc;
vlan-id 600;
}
}
}
Set up IP connection, OSPF and LDP
- CE1:
/ip address add address=192.168.88.1/24 interface=vlan1
- CE2:
/ip address add address=192.168.88.2/24 interface=vlan1
- PE1 (RouterOS):
/interface bridge add name=loopback /ip address add address=192.168.168.2/24 interface=ether3 add address=10.255.11.31/32 interface=loopback /routing ospf network add area=backbone disabled=no network=192.168.168.0/24 add area=backbone disabled=no network=10.255.11.31/32 /mpls ldp set enabled=yes lsr-id=10.255.11.31 transport-address=10.255.11.31 /mpls ldp interface add interface=ether3
- P (RouterOS):
/interface bridge add name=loopback /ip address add address=10.0.11.23/24 interface=ether1 add address=192.168.168.1/24 interface=ether2 add address=10.255.11.23/32 interface=loopback /routing ospf network add area=backbone disabled=no network=10.0.11.0/24 add area=backbone disabled=no network=192.168.168.0/24 add area=backbone disabled=no network=10.255.11.23/32 /mpls ldp set enabled=yes lsr-id=10.255.11.23 transport-address=10.255.11.23 /mpls ldp interface add interface=ether1 add interface=ether2
- PE2 (JunOS):
interfaces {
fe-0/0/0 {
unit 0 {
family inet {
address 10.0.11.201/24;
}
family mpls;
}
}
lo0 {
unit 0 {
family inet {
address 10.255.11.201/32;
}
}
}
}
protocols {
mpls {
interface fe-0/0/0.0;
interface lo0.0;
}
ospf {
export [ export-connected originate ];
area 0.0.0.0 {
interface fe-0/0/0.0;
interface lo0.0 {
passive;
}
}
}
ldp {
egress-policy connected-only;
transport-address 10.255.11.201;
interface all;
}
}
Finally we need to define policy options to advertise label binding for Loopback prefix:
policy-options {
prefix-list loopback-prefix {
10.255.11.201/32;
}
policy-statement connected-only {
from {
prefix-list loopback-prefix;
}
then accept;
}
}
Set up L2VPN
- PE1 (RouterOS):
/interface vpls
add cisco-style=yes cisco-style-id=5 name=junos-l2circuit pw-type=tagged-ethernet \
remote-peer=10.255.11.201
/interface bridge add name=vpn
/interface bridge port
add interface=ether5 bridge=vpn
add interface=junos-l2circuit bridge=vpn
We need to set pw-type=tagged-ethernet since on juniper encapsulation was set to vlan-ccc. Otherwise Juniper will throw an error /EM -- encapsulation mismatch /
- PE2 (JunOS):
protocol {
l2circuit {
neighbor 10.255.11.31 {
interface fe-0/0/1.1 {
virtual-circuit-id 5;
}
}
}
}
Verify Operation
Verify if LDP neighbors are found and forwarding table is created:
- PE1:
[admin@10.0.11.31] /mpls ldp neighbor> print Flags: X - disabled, D - dynamic, O - operational, T - sending-targeted-hello, V - vpls # TRANSPORT LOCAL-TRANSPORT PEER SEN 0 DO 10.255.11.23 10.255.11.31 10.255.11.23:0 no 1 DOTV 10.255.11.201 10.255.11.31 10.255.11.201:0 yes
[admin@10.0.11.31] /mpls forwarding-table> print Flags: L - ldp, V - vpls, T - traffic-eng # IN-LABEL OUT-LABELS DESTINATION I NEXTHOP 0 expl-null 1 L 17 3396 10.255.11.201/32 e 192.168.168.1 2 L 19 10.255.11.23/32 e 192.168.168.1 3 L 23 3390 10.5.101.0/24 e 192.168.168.1 4 V 29 junos-l2circuit
- PE2:
juniper@J4300> show ldp neighbor Address Interface Label space ID Hold time 10.255.11.31 lo0.0 10.255.11.31:0 42 10.0.11.23 fe-0/0/0.0 10.255.11.23:0 13
Verify traffic forwarding over LSP:
- PE1:
[admin@10.0.11.31] /interface vpls> /tool traceroute 10.255.11.201 # ADDRESS RT1 RT2 RT3 STATUS 1 192.168.168.1 1ms 1ms 1ms <MPLS:L=3396,E=0> 2 10.255.11.201 2ms 3ms 3ms
Verify if L2VPN tunnel is up and running:
- PE1
[admin@10.0.11.31] /interface vpls> monitor junos-l2circuit once
remote-label: 577168
local-label: 29
remote-status:
transport: 10.255.11.201/32
transport-nexthop: 192.168.168.1
imposed-labels: 3396,577168
- PE2
juniper@J4300> show l2circuit connections
Layer-2 Circuit Connections:
Legend for connection status (St)
EI -- encapsulation invalid NP -- interface h/w not present
MM -- mtu mismatch Dn -- down
EM -- encapsulation mismatch VC-Dn -- Virtual circuit Down
CM -- control-word mismatch Up -- operational
VM -- vlan id mismatch CF -- Call admission control failure
OL -- no outgoing label IB -- TDM incompatible bitrate
NC -- intf encaps not CCC/TCC TM -- TDM misconfiguration
BK -- Backup Connection ST -- Standby Connection
CB -- rcvd cell-bundle size bad XX -- unknown
Legend for interface status
Up -- operational
Dn -- down
Neighbor: 10.255.11.31
Interface Type St Time last up # Up trans
fe-0/0/1.1(vc 5) rmt Up Apr 19 12:28:30 2012 2
Remote PE: 10.255.11.31, Negotiated control-word: No
Incoming label: 577168, Outgoing label: 29
Local interface: fe-0/0/1.1, Status: Up, Encapsulation: VLAN
juniper@J4300>
BGP Based VPN
Lets consider that we have the same network layout as in LDP based lab and lets assume that IP connectivity, OSPF and LDP are already set up.
In this case we will not use vlans.
First thing to do is to set up BGP peers and then we can add L2VPN configuration.
Adjust MTUs
On RouterOS we do not adjust L2MTU values since I am using RouterBoards that has L2MTU set to 1632 by default. Only MPLS MTU is adjusted.
- PE1 (RouterOS):
/mpls interface set 0 mpls-mtu=1526
- P (RouterOS):
/mpls interface set 0 mpls-mtu=1526
On Juniper router we will adjust L2MTU to 1600 and MPLS MTU to 1526 on interface running MPLS.
We will also set up L2MTU to 1514 on cross circuit interface and set encapsulation to ethernet.
- PE2 (JunOS):
interfaces {
fe-0/0/0 {
mtu 1600;
unit 0 {
family inet {
mtu 1500;
address 10.0.11.201/24;
}
family mpls {
mtu 1526;
}
}
}
fe-0/0/1 {
mtu 1514;
encapsulation ethernet-ccc;
unit 0 {
family ccc;
}
}
}
Set up BGP
- PE1 (RouterOS):
/routing bgp instance
set default as=64201 router-id=10.255.11.31
/routing bgp peer
add address-families=l2vpn name=juniper remote-address=10.255.11.201 \
remote-as=64201 ttl=default
- PE2 (JunOS):
routing-options {
router-id 10.255.11.201;
autonomous-system 64201;
}
protocol {
bgp {
log-updown;
group int {
type internal;
local-address 10.255.11.201;
import match-all;
family l2vpn {
signaling;
}
export match-all;
neighbor 10.255.11.31;
}
}
}
policy-options {
policy-statement match-all {
term acceptable {
then accept;
}
}
}
Set up L2VPN
- PE1 (RouterOS):
/interface bridge
add ame=vpn
/interface bridge port
add interface=ether5 bridge=vpn
/interface vpls bgp-vpls
add bridge=vpn bridge-cost=0 export-route-targets=1:1 \
import-route-targets=1:1 name=juniper-l2vpn pw-type=tagged-ethernet \
route-distinguisher=1:1 site-id=20 use-control-word=no

Note: Parameter pw-type is available starting from v5.16. It allows to choose advertised encapsulation in NLRI used only for comparison. Available options are raw-ethernet (5), tagged-ethernet (4) and vpls (19) which is default setting and was hard coded in previous versions.
- PE2 (JunOS):
At first we define what is allowed to import and export by routing instance:
policy-options {
policy-statement vpn-SPA-export {
term a {
then {
community add SPA-com;
accept;
}
}
term b {
then reject;
}
}
policy-statement vpn-SPA-import {
term a {
from {
protocol bgp;
community SPA-com;
}
then accept;
}
term b {
then reject;
}
}
community SPA-com members target:1:1;
}
Now we can add L2VPN routing instance:
routing-instances {
vpls1 {
instance-type l2vpn;
interface fe-0/0/1.0;
route-distinguisher 1:1;
vrf-import [ match-all vpn-SPA-import ];
vrf-export vpn-SPA-export;
protocols {
l2vpn {
traceoptions {
file VPLS-TEST size 100000 files 7;
flag all;
}
encapsulation-type ethernet;
no-control-word;
site c2 {
site-identifier 21;
interface fe-0/0/1.0 {
remote-site-id 20;
}
}
}
}
}
}

Note: By setting encapsulation-type (pw-type on RouterOS). Does not change actual encapsulation. It is also possible that configured encapsulation types do not match on both ends. In this case you can use ignore-encapsulation-mismatch on Juniper routers.
In this configuration we also have disabled Cotrol Word usage with no-control-word on JunOS and use-control-word=no on RouterOS.
Verify Operation
Verify if BGP peer is up
- PE1 (RouterOS):
[admin@10.0.11.31] /routing bgp peer> print status
Flags: X - disabled, E - established
0 E name="juniper" instance=default remote-address=10.255.11.201
remote-as=64201 tcp-md5-key="" nexthop-choice=default multihop=no
route-reflect=no hold-time=3m ttl=default in-filter="" out-filter=""
address-families=l2vpn default-originate=never remove-private-as=no
as-override=no passive=no use-bfd=no remote-id=10.255.11.201
local-address=10.255.11.31 uptime=1h1m26s prefix-count=0 updates-sent=1
updates-received=1 withdrawn-sent=0 withdrawn-received=0
remote-hold-time=1m30s used-hold-time=1m30s used-keepalive-time=30s
refresh-capability=yes as4-capability=yes state=established
- PE2 (JunOS):
juniper@J4300> show bgp summary Groups: 3 Peers: 4 Down peers: 3 Table Tot Paths Act Paths Suppressed History Damp State Pending inet.0 0 0 0 0 0 0 bgp.l2vpn.0 1 1 0 0 0 0 Peer AS InPkt OutPkt OutQ Flaps Last Up/Dwn State|#Active/Rec... 10.255.11.31 64201 148 152 0 2 59:56 Establ bgp.l2vpn.0: 1/1/1/0 vpls1.l2vpn.0: 1/1/1/0
Verify if L2VPN tunnel is created
- PE1 (RouterOS):
[admin@10.0.11.31] /interface vpls> print
Flags: X - disabled, R - running, D - dynamic,
B - bgp-signaled, C - cisco-bgp-signaled
0 RDB name="vpls2" mtu=1500 l2mtu=1500 mac-address=02:04:3F:CD:06:97
arp=enabled disable-running-check=no remote-peer=10.255.11.201
cisco-style=no cisco-style-id=0 advertised-l2mtu=1500
pw-type=raw-ethernet vpls=juniper-l2vpn
[admin@10.0.11.31] /interface vpls> monitor 0
remote-label: 800021
local-label: 27
remote-status:
transport: 10.255.11.201/32
transport-nexthop: 10.0.11.201
imposed-labels: 800021
- PE2 (JunOS):
juniper@J4300> show l2vpn connections extensive
Layer-2 VPN connections:
Legend for connection status (St)
EI -- encapsulation invalid NC -- interface encapsulation not CCC/TCC/VPLS
EM -- encapsulation mismatch WE -- interface and instance encaps not same
VC-Dn -- Virtual circuit down NP -- interface hardware not present
CM -- control-word mismatch -> -- only outbound connection is up
CN -- circuit not provisioned <- -- only inbound connection is up
OR -- out of range Up -- operational
OL -- no outgoing label Dn -- down
LD -- local site signaled down CF -- call admission control failure
RD -- remote site signaled down SC -- local and remote site ID collision
LN -- local site not designated LM -- local site ID not minimum designated
RN -- remote site not designated RM -- remote site ID not minimum designated
XX -- unknown connection status IL -- no incoming label
MM -- MTU mismatch MI -- Mesh-Group ID not availble
BK -- Backup connection ST -- Standby connection
Legend for interface status
Up -- operational
Dn -- down
Instance: vpls1
Local site: c2 (21)
Number of local interfaces: 1
Number of local interfaces up: 1
fe-0/0/1.1 20
Label-base Offset Range Preference
800020 19 2 100
status-vector: 80
connection-site Type St Time last up # Up trans
20 rmt Up Apr 24 07:30:50 2012 1
Remote PE: 10.255.11.31, Negotiated control-word: No
Incoming label: 800021, Outgoing label: 27
Local interface: fe-0/0/1.0, Status: Up, Encapsulation: ETHERNET
Connection History:
Apr 24 07:30:50 2012 status update timer
Apr 24 07:30:50 2012 PE route changed
Apr 24 07:30:50 2012 Out lbl Update 27
Apr 24 07:30:50 2012 In lbl Update 800021
Apr 24 07:30:50 2012 loc intf up fe-0/0/1.1
juniper@J4300>