Manual:IP/Fasttrack: Difference between revisions
No edit summary |
|||
| (3 intermediate revisions by 2 users not shown) | |||
| Line 4: | Line 4: | ||
=== Description === | === Description === | ||
IPv4 FastTrack handler is automatically used for marked connections. Use firewall action "fasttrack-connection" to mark connections for | IPv4 FastTrack handler is automatically used for marked connections. Use firewall action "fasttrack-connection" to mark connections for FastTrack. Currently only TCP and UDP connections can be actually FastTracked (even though any connection can be marked for FastTrack). IPv4 FastTrack handler supports NAT (SNAT, DNAT or both). | ||
Note that not all packets in a connection can be | Note that not all packets in a connection can be FastTracked, so it is likely to see some packets going through slow path even though connection is marked for FastTrack. This is the reason why fasttrack-connection is usually followed by identical action=accept rule. FastTracked packets bypass firewall, connection tracking, simple queues, queue tree with parent=global, <del>ip traffic-flow</del>(restriction removed in 6.33), IP accounting, IPSec, hotspot universal client, VRF assignment, so it is up to administrator to make sure FastTrack does not interfere with other configuration; | ||
=== Requirements === | === Requirements === | ||
| Line 16: | Line 16: | ||
* /tool mac-scan is not actively used; | * /tool mac-scan is not actively used; | ||
* /tool ip-scan is not actively used; | * /tool ip-scan is not actively used; | ||
* FastPath and Route cache is enabled under IP/Settings | |||
=== Supported hardware === | === Supported hardware === | ||
FastTrack is supported on the listed devices. | |||
<table class="styled_table"> | <table class="styled_table"> | ||
| Line 47: | Line 47: | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td ><b>RB1100 | <td ><b>RB1100, RB1000AHx2</b></td> | ||
<td >ether1-11</td> | <td >ether1-11</td> | ||
</tr> | |||
<tr> | |||
<td ><b>RB1000AHx2</b></td> | |||
<td >all ports</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 56: | Line 60: | ||
<tr> | <tr> | ||
<td ><b>RB3011 series</b></td> | <td ><b>RB3011 series</b></td> | ||
<td >all ports</td> | |||
</tr> | |||
<tr> | |||
<td ><b>RB4011 series</b></td> | |||
<td >all ports</td> | <td >all ports</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td ><b>CRS series routers</b></td> | <td ><b>CRS series routers</b></td> | ||
<td >all ports</td> | <td >all ports except management interface (if the device has one) </td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td ><b>CCR series routers</b></td> | <td ><b>CCR series routers</b></td> | ||
<td >all ports</td> | <td >all ports except management interface (if the device has one) </td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td ><b>All devices</b></td> | <td ><b>All devices</b></td> | ||
<td >wireless interfaces, if wireless-fp | <td >wireless interfaces, if wireless-fp, wireless-cm2, wireless-rep or wireless (starting from 6.37) package used</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
| Line 74: | Line 82: | ||
=== Examples === | === Examples === | ||
==== Initial configuration ==== | ==== Initial configuration ==== | ||
For example, in home routers with factory default configuration, you could | For example, in home routers with factory default configuration, you could FastTrack all LAN traffic with this one rule placed at the top of the Firewall Filter. The same configuration accept rule is required: | ||
/ip firewall filter add chain=forward action=fasttrack-connection connection-state=established,related | /ip firewall filter add chain=forward action=fasttrack-connection connection-state=established,related | ||
| Line 92: | Line 100: | ||
[[File:Fasttrackon2011.png|center|frame]] | [[File:Fasttrackon2011.png|center|frame]] | ||
[[Category:Manual|Firewall| | [[Category:Manual|Firewall|Fasttrack]] | ||
Latest revision as of 09:18, 10 December 2018
Description
IPv4 FastTrack handler is automatically used for marked connections. Use firewall action "fasttrack-connection" to mark connections for FastTrack. Currently only TCP and UDP connections can be actually FastTracked (even though any connection can be marked for FastTrack). IPv4 FastTrack handler supports NAT (SNAT, DNAT or both).
Note that not all packets in a connection can be FastTracked, so it is likely to see some packets going through slow path even though connection is marked for FastTrack. This is the reason why fasttrack-connection is usually followed by identical action=accept rule. FastTracked packets bypass firewall, connection tracking, simple queues, queue tree with parent=global, ip traffic-flow(restriction removed in 6.33), IP accounting, IPSec, hotspot universal client, VRF assignment, so it is up to administrator to make sure FastTrack does not interfere with other configuration;
Requirements
IPv4 FastTrack is active if following conditions are met:
- no mesh, metarouter interface configuration;
- sniffer, torch and traffic generator is not running;
no active mac-ping, mac-telnet or mac-winbox sessionsrestriction removed in 6.33;- /tool mac-scan is not actively used;
- /tool ip-scan is not actively used;
- FastPath and Route cache is enabled under IP/Settings
Supported hardware
FastTrack is supported on the listed devices.
| RouterBoard | Interfaces |
|---|---|
| RB6xx series | ether1,2 |
| RB7xx series | all ports |
| RB800 | ether1,2 |
| RB9xx series | all ports |
| RB1000 | all ports |
| RB1100, RB1000AHx2 | ether1-11 |
| RB1000AHx2 | all ports |
| RB2011 series | all ports |
| RB3011 series | all ports |
| RB4011 series | all ports |
| CRS series routers | all ports except management interface (if the device has one) |
| CCR series routers | all ports except management interface (if the device has one) |
| All devices | wireless interfaces, if wireless-fp, wireless-cm2, wireless-rep or wireless (starting from 6.37) package used |
Examples
Initial configuration
For example, in home routers with factory default configuration, you could FastTrack all LAN traffic with this one rule placed at the top of the Firewall Filter. The same configuration accept rule is required:
/ip firewall filter add chain=forward action=fasttrack-connection connection-state=established,related /ip firewall filter add chain=forward action=accept connection-state=established,related
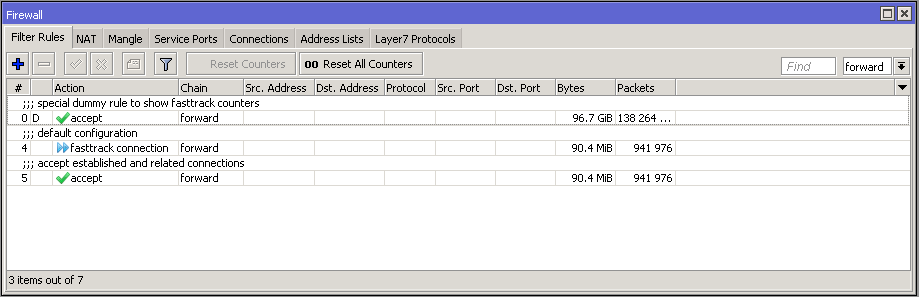
View of simple FastTrack rules in the firewall, it is important to have other filter or mangle rules to get the advantage of the FastTrack:
- /ip firewall filter
- /ip firewall mangle
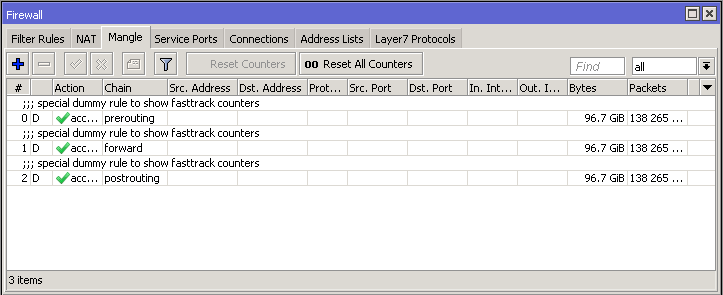

Warning: Queues (except Queue Trees parented to interfaces), firewall filter and mangle rules will not be applied for FastTracked traffic.
- Connection is FastTracked until connection is closed, timed-out or router is rebooted.
- Dummy rules will dissapear only after FastTrack firewall rules will be deleted/disabled and router rebooted.
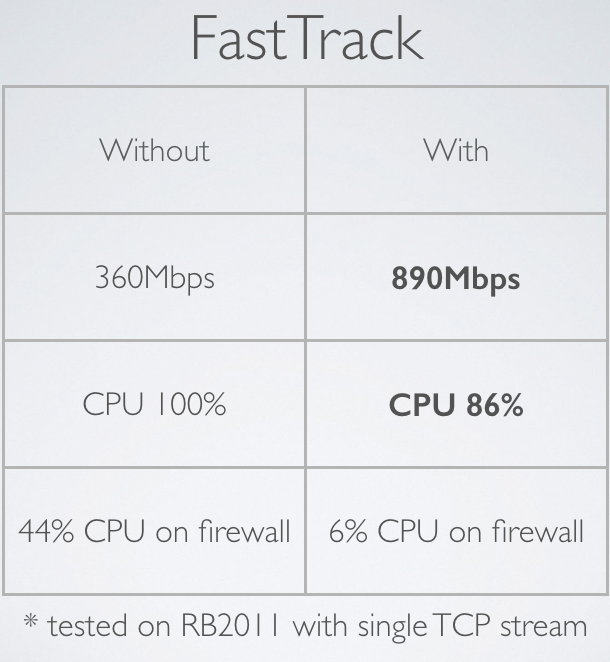
FastTrack on RB2011
FastTrack is enabled on RB2011 at chain=forward with the rule from previous example. Bandwidth test with single TCP stream is sent,