Load Balancing over Multiple Gateways: Difference between revisions
No edit summary |
No edit summary |
||
| Line 1: | Line 1: | ||
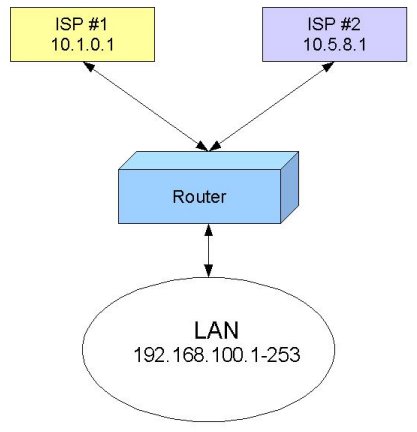
The typical situation where you got one router and want to connect to two ISPs: | The typical situation where you got one router and want to connect to two ISPs: | ||
[[Image:dual_gw_01.jpg]] | |||
Of course, you want to do load balancing | Of course, you want to do load balancing! There are several ways how to do it. Depending on the particular situation, you may find one best suited for you. | ||
== Policy Routing based on Client IP Address == | == Policy Routing based on Client IP Address == | ||
If you have a number of hosts, you may group them by IP addresses. Then, send the traffic out through Gateway 1 or 2 depending on the source IP address. | If you have a number of hosts, you may group them by IP addresses. Then, send the traffic out through Gateway 1 or 2 depending on the source IP address. This is not the best approach, giving you perfect load balancing, but it's easy to implement, and gives you some control too. | ||
Let us assume we use for our workstations IP addresses from network 192.168.100.0/24. The IP addresses are assigned as follows: | Let us assume we use for our workstations IP addresses from network 192.168.100.0/24. The IP addresses are assigned as follows: | ||
* 192.168.100.1-127 are used for Group A workstations | * 192.168.100.1-127 are used for Group A workstations | ||
* 192.168.100.128-253 are used for Group B workstations | * 192.168.100.128-253 are used for Group B workstations | ||
* 192.168.100.254 is | * 192.168.100.254 is used for the router. | ||
All workstations have IP configuration with the IP address from the relevant group, they all have network mask 255.255.255.0, and the default gateway 192.168.100.254 | All workstations have IP configuration with the IP address from the relevant group, they all have network mask 255.255.255.0, and the default gateway 192.168.100.254 | ||
| Line 18: | Line 18: | ||
We will talk about DNS servers later. | We will talk about DNS servers later. | ||
Next, we need to configure policy routing. We have workstations | Next, we need to configure policy routing. We have workstations divided into groups, where we can refer to them using subnet addressing: | ||
* Group A is 192.168.100.0/25, i.e., addresses 192.168.100.0-127 | * Group A is 192.168.100.0/25, i.e., addresses 192.168.100.0-127 | ||
* Group B is 192.168.100.128/25, i.e., addresses 192.18.100.128-255 | * Group B is 192.168.100.128/25, i.e., addresses 192.18.100.128-255 | ||
If you do not understand this, take the TCP/IP Basics course, or, look for some resources about subnetting on the Internet! | If you do not understand this, take the TCP/IP Basics course, or, look for some resources about subnetting on the Internet! | ||
We need to add two IP Firewall Mangle rules to mark the packets originated from Group A or B workstations. | We need to add two IP Firewall Mangle rules to mark the packets originated from Group A or B workstations. | ||
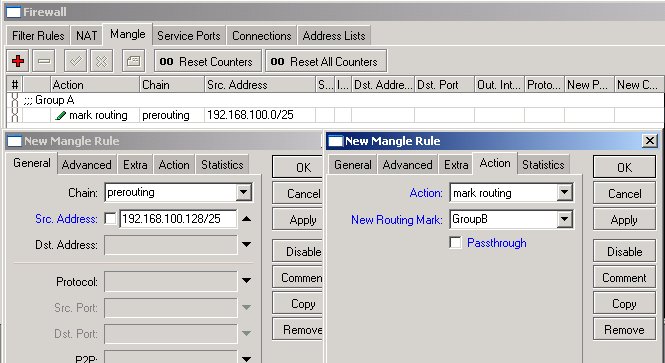
For '''Group A''', | For '''Group A''', specify | ||
* Chain '''prerouting''' and Src. Address '''192.168.100.0/25''' | |||
* Action '''mark routing''' and New Routing Mark '''GroupA'''. | |||
[[Image: | [[Image:dual_gw_21.jpg]] | ||
It is a good practice to add a comment as well. Your mangle rules might be interesting for someone else and for yourself as well after some time. | It is a good practice to add a comment as well. Your mangle rules might be interesting for someone else and for yourself as well after some time. | ||
For '''Group B''', specify | For '''Group B''', specify | ||
* Chain ''' | * Chain '''prerouting''' and Src. Address '''192.168.100.128/25''' | ||
* Action '''mark routing''' and New Routing Mark '''GroupB''' | * Action '''mark routing''' and New Routing Mark '''GroupB''' | ||
| Line 50: | Line 46: | ||
[[Image:dual_gw_26.jpg]] | [[Image:dual_gw_26.jpg]] | ||
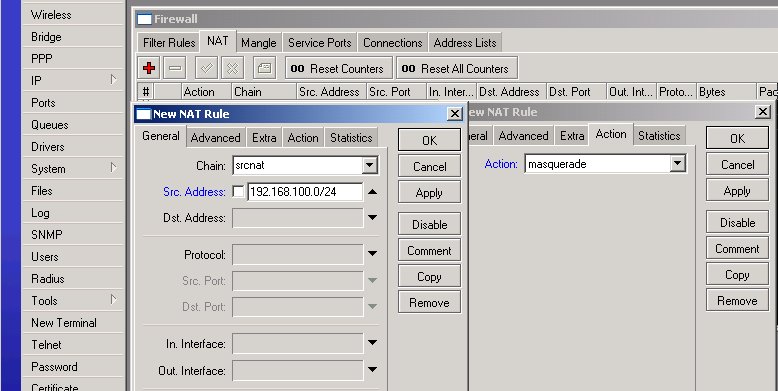
This thing is not going to work, unless you do masquerading for your LAN! The | This thing is not going to work, unless you do masquerading for your LAN! The simplest way to it is by adding one NAT rule for Src. Address '''192.168.100.0/24''' and Action '''masquerade''': | ||
[[Image:dual_gw_28.jpg]] | [[Image:dual_gw_28.jpg]] | ||
| Line 76: | Line 72: | ||
... | ... | ||
You can specify | You can specify the DNS server for workstations quite freely, just make it can be reached (test it by tracing the route to DNS server's IP address)! | ||
Revision as of 22:00, 21 December 2005
The typical situation where you got one router and want to connect to two ISPs:
Of course, you want to do load balancing! There are several ways how to do it. Depending on the particular situation, you may find one best suited for you.
Policy Routing based on Client IP Address
If you have a number of hosts, you may group them by IP addresses. Then, send the traffic out through Gateway 1 or 2 depending on the source IP address. This is not the best approach, giving you perfect load balancing, but it's easy to implement, and gives you some control too.
Let us assume we use for our workstations IP addresses from network 192.168.100.0/24. The IP addresses are assigned as follows:
- 192.168.100.1-127 are used for Group A workstations
- 192.168.100.128-253 are used for Group B workstations
- 192.168.100.254 is used for the router.
All workstations have IP configuration with the IP address from the relevant group, they all have network mask 255.255.255.0, and the default gateway 192.168.100.254
We will talk about DNS servers later.
Next, we need to configure policy routing. We have workstations divided into groups, where we can refer to them using subnet addressing:
- Group A is 192.168.100.0/25, i.e., addresses 192.168.100.0-127
- Group B is 192.168.100.128/25, i.e., addresses 192.18.100.128-255
If you do not understand this, take the TCP/IP Basics course, or, look for some resources about subnetting on the Internet!
We need to add two IP Firewall Mangle rules to mark the packets originated from Group A or B workstations.
For Group A, specify
- Chain prerouting and Src. Address 192.168.100.0/25
- Action mark routing and New Routing Mark GroupA.
It is a good practice to add a comment as well. Your mangle rules might be interesting for someone else and for yourself as well after some time.
For Group B, specify
- Chain prerouting and Src. Address 192.168.100.128/25
- Action mark routing and New Routing Mark GroupB
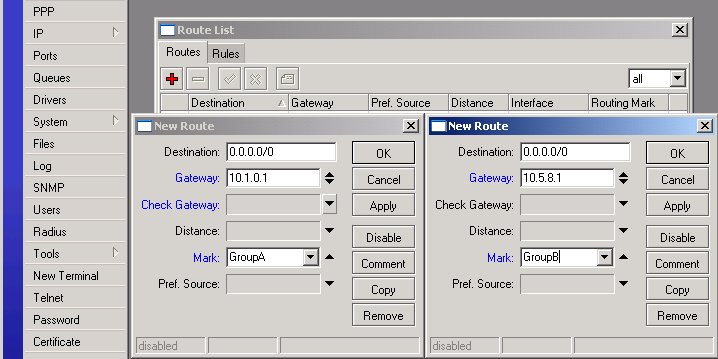
All IP traffic coming from workstations is marked with the routing marks GroupA or GroupB. We can use these marks in the routing table.
Next, we should specify two default routes (destination 0.0.0.0/0) with appropriate routing marks and gateways:
This thing is not going to work, unless you do masquerading for your LAN! The simplest way to it is by adding one NAT rule for Src. Address 192.168.100.0/24 and Action masquerade:
Test the setup by using traceroute to some IP address on the Internet!
From a workstation of Group A, it should go like this:
C:\>tracert -d 8.8.8.8 Tracing route to 8.8.8.8 over a maximum of 30 hops 1 2 ms 2 ms 2 ms 192.168.100.254 2 10 ms 4 ms 3 ms 10.1.0.1 ...
From a workstation of Group B, it should go like this:
C:\>tracert -d 8.8.8.8 Tracing route to 8.8.8.8 over a maximum of 30 hops 1 2 ms 2 ms 2 ms 192.168.100.254 2 10 ms 4 ms 3 ms 10.5.8.1 ...
You can specify the DNS server for workstations quite freely, just make it can be reached (test it by tracing the route to DNS server's IP address)!