Manual:Packet Flow v6: Difference between revisions
Jump to navigation
Jump to search
| Line 19: | Line 19: | ||
==Examples== | ==Examples== | ||
[[Image:PacketFlowDiagram_v6_examples_a.gif|Example 1 | [[Image:PacketFlowDiagram_v6_examples_a.gif|Example 1|center]] | ||
[[Image:PacketFlowDiagram_v6_examples_b.gif|Example 2 | [[Image:PacketFlowDiagram_v6_examples_b.gif|Example 2|center]] | ||
[[Image:PacketFlowDiagram_v6_examples_c.gif|Example 3 | [[Image:PacketFlowDiagram_v6_examples_c.gif|Example 3|center]] | ||
[[Image:PacketFlowDiagram_v6_examples_d.gif|Example 4 | [[Image:PacketFlowDiagram_v6_examples_d.gif|Example 4|center]] | ||
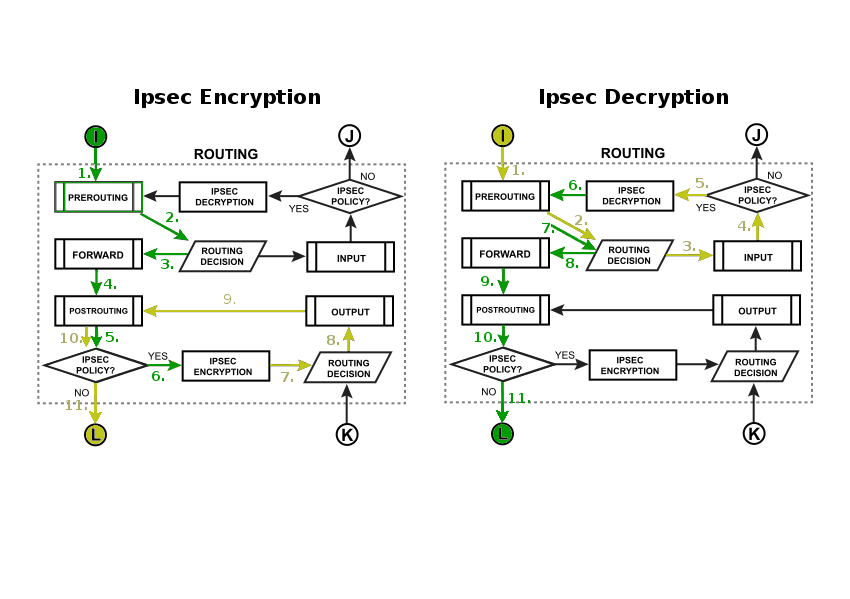
===Ipsec Encryption/Decryption=== | ===Ipsec Encryption/Decryption=== | ||
[[Image:IpsecFlow.png|Example 5 | [[Image:IpsecFlow.png|Example 5|center]] | ||
Revision as of 10:25, 28 May 2015
Overview
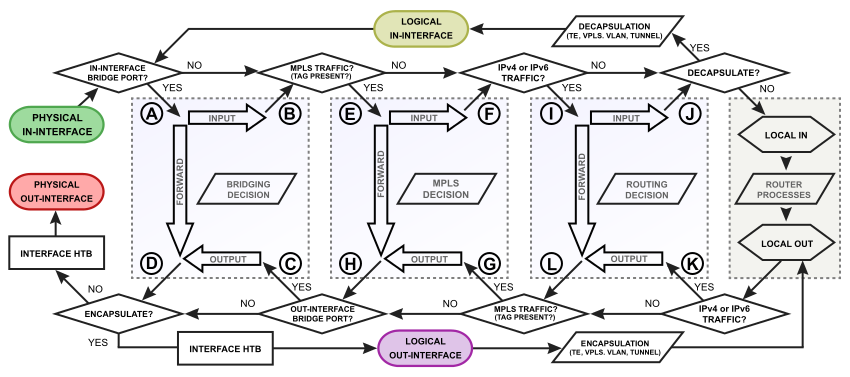
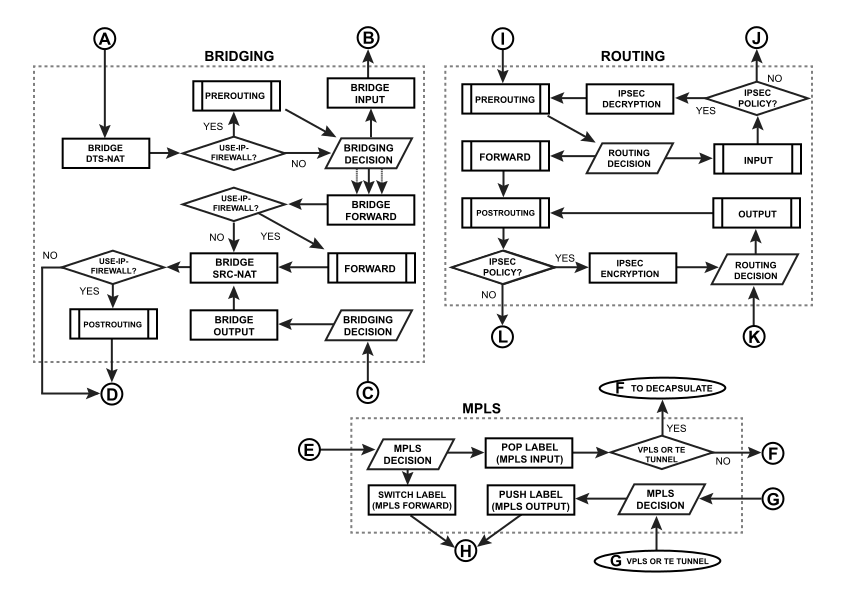
Diagram
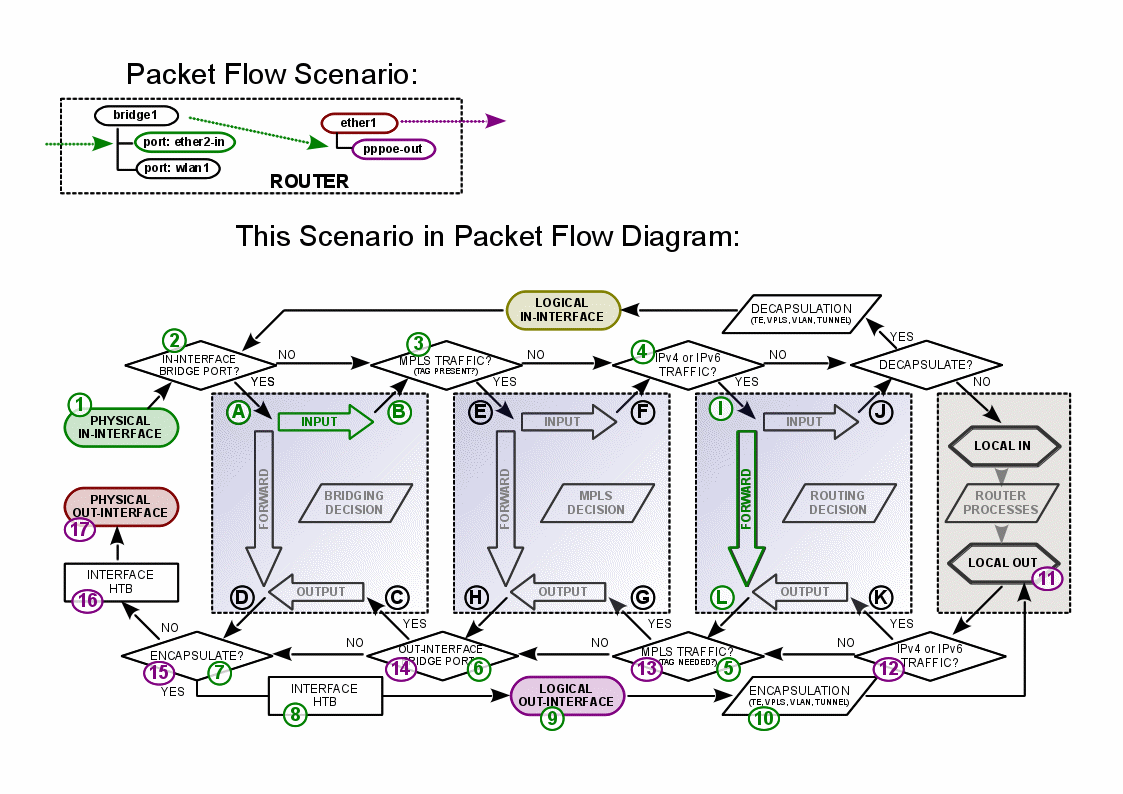
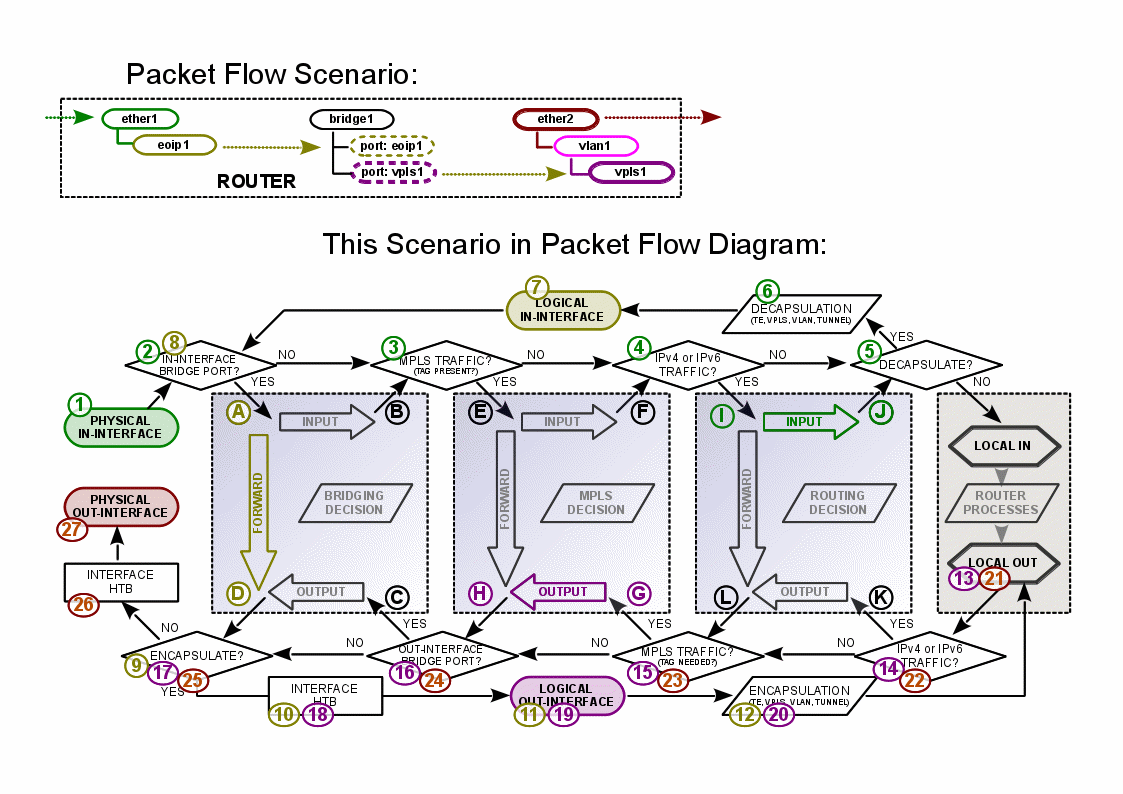
Examples
Ipsec Encryption/Decryption
[ Top | Back to Content ]
