Manual:Securing Your Router: Difference between revisions
Created page with "The following steps are recommendation how to protect your router. We strongly suggest to keep default firewall, it can be patched by other rules that fullfils your setup requ..." |
No edit summary |
||
| Line 25: | Line 25: | ||
x.x.x.x/yy - your IP or network subnet that is allowed to access your router. | x.x.x.x/yy - your IP or network subnet that is allowed to access your router. | ||
==Router services== | |||
All production routers have to be administred by SSH, secured Winbox or HTTPs services. Use the latest Winbox version for secure access. | |||
[[File:Screenshot_2017-03-23_14.53.51.png | 900px]] | |||
===RouterOS services=== | |||
Most of RouterOS administrative tools are configured at | |||
<pre> /ip service print </pre> | |||
Keep only secure ones, | |||
/ip service print | <pre>/ip service disable telnet,ftp,www,api,api-ssl | ||
/ip service print </pre> | |||
Additionaly each /ip service entity might be secured by allowed IP address (the address service will reply to) | |||
<pre>/ip service set winbox allowed-address=192.168.88.0/24</pre> | |||
Additionaly each /ip service entity might be secured by allowed address (the address service will reply to) | |||
/ip service set winbox allowed-address=192.168.88.0/24 | |||
=== RouterOS MAC-access=== | |||
RouterOS has built-in options for easy management access to network devices. The particular services should be shutdown on production networks. | RouterOS has built-in options for easy management access to network devices. The particular services should be shutdown on production networks. | ||
====MAC-Telnet==== | |||
Disable mac-telnet services, | Disable mac-telnet services, | ||
/tool mac-server set [find] disabled=yes | <pre>/tool mac-server set [find] disabled=yes | ||
/tool mac-server print | /tool mac-server print</pre> | ||
====MAC-Winbox==== | |||
Disable mac-winbox services, | Disable mac-winbox services, | ||
/tool mac-server mac-winbox set [find] disabled=yes | <pre>/tool mac-server mac-winbox set [find] disabled=yes | ||
/tool mac-server mac-winbox print | /tool mac-server mac-winbox print</pre> | ||
====MAC-Ping==== | |||
Disable mac-ping service, | Disable mac-ping service, | ||
/tool mac-server ping set enabled=no | <pre>/tool mac-server ping set enabled=no | ||
/tool mac-server ping print | /tool mac-server ping print</pre> | ||
=== Neighbor Discovery=== | |||
MikroTik Neighbor discovery protocol is used to show and recognize other MikroTik routers in the network, disable neighbor discovery on all interfaces, | MikroTik Neighbor discovery protocol is used to show and recognize other MikroTik routers in the network, disable neighbor discovery on all interfaces, | ||
/ip neighbor discovery | <pre>/ip neighbor discovery set [find] discover=no </pre> | ||
=== Bandwidth server=== | |||
Bandwidth server is used to test throughput between two MikroTik routers. Disable it in production enironment. | |||
<pre>/tool bandwidth-server set enabled=no </pre> | |||
===DNS cache=== | |||
Router might have DNS cache enabled, that decreases resolving time for DNS requests from clients to remote servers. In case DNS cache is not required on your router or another router is used for such purposes, disable it. | |||
<pre>ip dns set allow-remote-requests=no</pre> | |||
===Other clients services=== | |||
RouterOS might have other services enabled (they are disabled by default RouterOS configuration). | |||
MikroTik caching proxy, | |||
<pre>/ip proxy set set enabled=no</pre> | |||
/ip | MikroTik socks proxy, | ||
<pre>/ip socks set enabled=no</pre> | |||
MikroTik UPNP service, | |||
<pre>/ip upnp set enabled=no</pre> | |||
MikroTik | MikroTik dynamic name service or ip cloud, | ||
<pre>ip cloud set ddns-enabled=no update-time=no</pre> | |||
===More Secure SSH access=== | |||
RouterOS utilises stronger crypto for SSH, most newer programs use it, to turn on SSH strong crypto: | |||
<pre>/ip ssh set strong-crypto=yes</pre> | |||
==Router interface== | |||
===Ethernet/SFP interfaces=== | |||
It is good practice to disable all unused interfaces on your router, in order to decrease unauthorised access to your router. | |||
<pre>/interface print | |||
/interface set x disabled=yes</pre> | |||
*x number of unused interfaces. | |||
===LCD=== | |||
Some RouterBOARDs have LCD module for informational purpose, set pin or disable it. | |||
<pre>/lcd set enabled=no</pre> | |||
==Firewall== | |||
/interface | We strongly suggest to keep default firewall on. Here are few adjustment to make it more secure, make sure to apply the rules, when you understand what are they doing. | ||
/interface | ===IPv4 firewall to a router=== | ||
* work with new connections to decrease load on a router; | |||
* create address-list for IP addresses, that are allowed to access your router; | |||
* enable ICMP access (optionally); | |||
* drop everything else, log=yes might be added to log packets that hit the specific rule; | |||
<pre>/ip firewall filter | |||
add action=accept chain=input comment="default configuration" connection-state=established,related | |||
add action=accept chain=input src-address-list=allowed_to_router | |||
add action=accept chain=input protocol=icmp | |||
add action=drop chain=input | |||
/ip firewall address-list | |||
add address=192.168.88.2-192.168.88.254 list=allowed_to_router</pre> | |||
===IPv4 firewall for clients=== | |||
* Established/related packets are added to [[M:IP/Fasttrack | fasttrack]] for faster data throughput, firewall will work with new connections only; | |||
* drop invalid connection and log them with prefix invalid; | |||
* drop attempts to reach not public addresses from your local network, apply address-list=not_in_internet before, bridge1 is local network interface, log attempts with !public_from_LAN; | |||
* drop incoming packets that are not NATed, ether1 is public interface, log attempts with !NAT prefix; | |||
* drop incoming packets from Internet, which are not public IP addresses, ether1 is public interface, log attempts with prefix !public; | |||
* drop packets from LAN that does not have LAN IP, 192.168.88.0/24 is local network used subnet; | |||
<pre> | |||
/ip firewall filter | |||
add action=fasttrack-connection chain=forward comment=FastTrack connection-state=established,related | |||
add action=accept chain=forward comment="Established, Related" connection-state=established,related | |||
add action=drop chain=forward comment="Drop invalid" connection-state=invalid log=yes log-prefix=invalid | |||
add action=drop chain=forward comment="Drop tries to reach not public addresses from LAN" dst-address-list=not_in_internet in-interface=bridge1 log=yes log-prefix=!public_from_LAN out-interface=!bridge1 | |||
add action=drop chain=forward comment="Drop incoming packets that are not NATted" connection-nat-state=!dstnat connection-state=new in-interface=ether1 log=yes log-prefix=!NAT | |||
add action=drop chain=forward comment="Drop incoming from internet which is not public IP" in-interface=ether1 log=yes log-prefix=!public src-address-list=not_in_internet | |||
add action=drop chain=forward comment="Drop packets from LAN that do not have LAN IP" in-interface=bridge1 log=yes log-prefix=LAN_!LAN src-address=!192.168.88.0/24 | |||
/ip firewall address-list | |||
add address=0.0.0.0/8 comment=RFC6890 list=not_in_internet | |||
add address=172.16.0.0/12 comment=RFC6890 list=not_in_internet | |||
add address=192.168.0.0/16 comment=RFC6890 list=not_in_internet | |||
add address=10.0.0.0/8 comment=RFC6890 list=not_in_internet | |||
add address=169.254.0.0/16 comment=RFC6890 list=not_in_internet | |||
add address=127.0.0.0/8 comment=RFC6890 list=not_in_internet | |||
add address=224.0.0.0/4 comment=Multicast list=not_in_internet | |||
add address=198.18.0.0/15 comment=RFC6890 list=not_in_internet | |||
add address=192.0.0.0/24 comment=RFC6890 list=not_in_internet | |||
add address=192.0.2.0/24 comment=RFC6890 list=not_in_internet | |||
add address=198.51.100.0/24 comment=RFC6890 list=not_in_internet | |||
add address=203.0.113.0/24 comment=RFC6890 list=not_in_internet | |||
add address=100.64.0.0/10 comment=RFC6890 list=not_in_internet | |||
add address=240.0.0.0/4 comment=RFC6890 list=not_in_internet | |||
add address=192.88.99.0/24 comment="6to4 relay Anycast [RFC 3068]" list=not_in_internet</pre> | |||
==IPv6== | |||
Currently IPv6 package is disabled by default. Please enable package with care, as router does not have firewall at the moment. | |||
/ | ===IPv6 ND=== | ||
Disable IPv6 Neighbour Discovery | |||
<pre>/ipv6 nd set [find] disabled=yes</pre> | |||
===IPv6 firewall to a router=== | |||
* work with new packets, accept established/related packets; | |||
* drop link-local addresses from Internet interface; | |||
* accept access to a router from link-local addresses, accept multicast addresses for management purposes, accept your address for router access; | |||
* drop anything else; | |||
<pre> | |||
/ipv6 firewall filter | |||
add action=accept chain=input comment="allow established and related" connection-state=established,related | |||
add action=drop chain=input in-interface=sit1 log=yes log-prefix=dropLL_from_public src-address=fe80::/16 | |||
add action=accept chain=input comment="allow allowed addresses" src-address-list=allowed | |||
add action=drop chain=input | |||
/ipv6 firewall address-list | |||
add address=fe80::/16 list=allowed | |||
add address=xxxx::/48 list=allowed | |||
add address=ff02::/16 comment=multicast list=allowed | |||
</pre> | |||
===IPv6 firewall for clients=== | |||
Enabled IPv6 puts your clients available for publci networks, set proper firewall to protect your customers. | |||
<pre> | |||
/ipv6 firewall filter | |||
* accept established/related and work with new packets; | |||
* drop invalid packets and put prefix for rules; | |||
* accept ICMP packets; | |||
* accept new connection from your clients to the Internet; | |||
* drop everything else. | |||
add action=accept chain=forward comment=established,related connection-state=established,related | |||
add action=drop chain=forward comment=invalid connection-state=invalid log=yes log-prefix=ipv6,invalid | |||
add action=accept chain=forward comment=icmpv6 in-interface=!sit1 protocol=icmpv6 | |||
add action=accept chain=forward comment="local network" in-interface=!sit1 src-address-list=allowed | |||
add action=drop chain=forward log-prefix=IPV6 | |||
Revision as of 17:17, 23 March 2017
The following steps are recommendation how to protect your router. We strongly suggest to keep default firewall, it can be patched by other rules that fullfils your setup requirements. Other tweaks and configuration options to harden your router's security are described later.
Access to a router
Access username
Change default username admin to different name, custom name helps to protect access to your rotuer, if anybody got direct access to your router.
/user print /user set 0 name=myname
Access password
MikroTik routers requires password configuration, we suggest to use pwgen or other password generator tool to create secure and non-repeating passwords,
/user set 0 password="!={Ba3N!"40TуX+GvKBz?jTLIUcx/,"
Another option to set a password,
/password
We strongly suggest to use second method or Winbox interface to apply new password for your router, just to keep it safe from other unauthorised access.
Access by IP address
Besides the fact that default firewall protects your router from unauthorized access from outer networks, it is possible to restrict username access for the specific IP address
/user set 0 allowed-address=x.x.x.x/yy
x.x.x.x/yy - your IP or network subnet that is allowed to access your router.
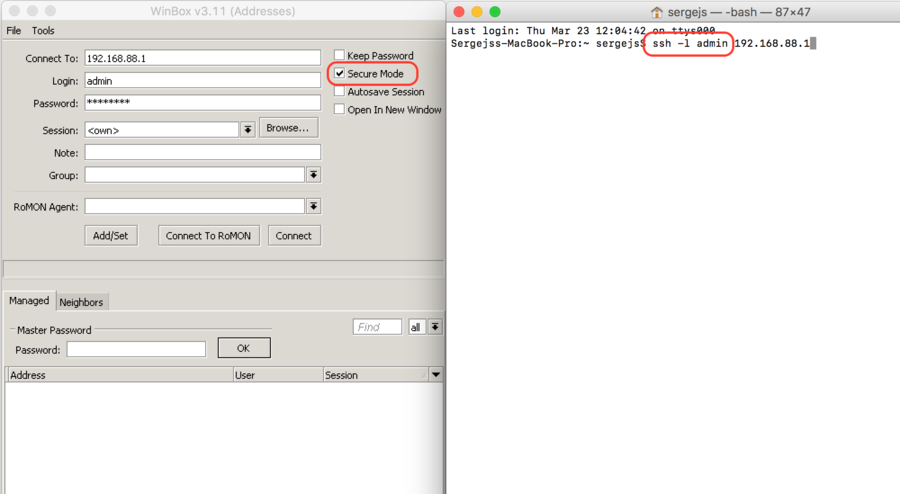
Router services
All production routers have to be administred by SSH, secured Winbox or HTTPs services. Use the latest Winbox version for secure access.
RouterOS services
Most of RouterOS administrative tools are configured at
/ip service print
Keep only secure ones,
/ip service disable telnet,ftp,www,api,api-ssl /ip service print
Additionaly each /ip service entity might be secured by allowed IP address (the address service will reply to)
/ip service set winbox allowed-address=192.168.88.0/24
RouterOS MAC-access
RouterOS has built-in options for easy management access to network devices. The particular services should be shutdown on production networks.
MAC-Telnet
Disable mac-telnet services,
/tool mac-server set [find] disabled=yes /tool mac-server print
MAC-Winbox
Disable mac-winbox services,
/tool mac-server mac-winbox set [find] disabled=yes /tool mac-server mac-winbox print
MAC-Ping
Disable mac-ping service,
/tool mac-server ping set enabled=no /tool mac-server ping print
Neighbor Discovery
MikroTik Neighbor discovery protocol is used to show and recognize other MikroTik routers in the network, disable neighbor discovery on all interfaces,
/ip neighbor discovery set [find] discover=no
Bandwidth server
Bandwidth server is used to test throughput between two MikroTik routers. Disable it in production enironment.
/tool bandwidth-server set enabled=no
DNS cache
Router might have DNS cache enabled, that decreases resolving time for DNS requests from clients to remote servers. In case DNS cache is not required on your router or another router is used for such purposes, disable it.
ip dns set allow-remote-requests=no
Other clients services
RouterOS might have other services enabled (they are disabled by default RouterOS configuration). MikroTik caching proxy,
/ip proxy set set enabled=no
MikroTik socks proxy,
/ip socks set enabled=no
MikroTik UPNP service,
/ip upnp set enabled=no
MikroTik dynamic name service or ip cloud,
ip cloud set ddns-enabled=no update-time=no
More Secure SSH access
RouterOS utilises stronger crypto for SSH, most newer programs use it, to turn on SSH strong crypto:
/ip ssh set strong-crypto=yes
Router interface
Ethernet/SFP interfaces
It is good practice to disable all unused interfaces on your router, in order to decrease unauthorised access to your router.
/interface print /interface set x disabled=yes
- x number of unused interfaces.
LCD
Some RouterBOARDs have LCD module for informational purpose, set pin or disable it.
/lcd set enabled=no
Firewall
We strongly suggest to keep default firewall on. Here are few adjustment to make it more secure, make sure to apply the rules, when you understand what are they doing.
IPv4 firewall to a router
- work with new connections to decrease load on a router;
- create address-list for IP addresses, that are allowed to access your router;
- enable ICMP access (optionally);
- drop everything else, log=yes might be added to log packets that hit the specific rule;
/ip firewall filter add action=accept chain=input comment="default configuration" connection-state=established,related add action=accept chain=input src-address-list=allowed_to_router add action=accept chain=input protocol=icmp add action=drop chain=input /ip firewall address-list add address=192.168.88.2-192.168.88.254 list=allowed_to_router
IPv4 firewall for clients
- Established/related packets are added to fasttrack for faster data throughput, firewall will work with new connections only;
- drop invalid connection and log them with prefix invalid;
- drop attempts to reach not public addresses from your local network, apply address-list=not_in_internet before, bridge1 is local network interface, log attempts with !public_from_LAN;
- drop incoming packets that are not NATed, ether1 is public interface, log attempts with !NAT prefix;
- drop incoming packets from Internet, which are not public IP addresses, ether1 is public interface, log attempts with prefix !public;
- drop packets from LAN that does not have LAN IP, 192.168.88.0/24 is local network used subnet;
/ip firewall filter add action=fasttrack-connection chain=forward comment=FastTrack connection-state=established,related add action=accept chain=forward comment="Established, Related" connection-state=established,related add action=drop chain=forward comment="Drop invalid" connection-state=invalid log=yes log-prefix=invalid add action=drop chain=forward comment="Drop tries to reach not public addresses from LAN" dst-address-list=not_in_internet in-interface=bridge1 log=yes log-prefix=!public_from_LAN out-interface=!bridge1 add action=drop chain=forward comment="Drop incoming packets that are not NATted" connection-nat-state=!dstnat connection-state=new in-interface=ether1 log=yes log-prefix=!NAT add action=drop chain=forward comment="Drop incoming from internet which is not public IP" in-interface=ether1 log=yes log-prefix=!public src-address-list=not_in_internet add action=drop chain=forward comment="Drop packets from LAN that do not have LAN IP" in-interface=bridge1 log=yes log-prefix=LAN_!LAN src-address=!192.168.88.0/24 /ip firewall address-list add address=0.0.0.0/8 comment=RFC6890 list=not_in_internet add address=172.16.0.0/12 comment=RFC6890 list=not_in_internet add address=192.168.0.0/16 comment=RFC6890 list=not_in_internet add address=10.0.0.0/8 comment=RFC6890 list=not_in_internet add address=169.254.0.0/16 comment=RFC6890 list=not_in_internet add address=127.0.0.0/8 comment=RFC6890 list=not_in_internet add address=224.0.0.0/4 comment=Multicast list=not_in_internet add address=198.18.0.0/15 comment=RFC6890 list=not_in_internet add address=192.0.0.0/24 comment=RFC6890 list=not_in_internet add address=192.0.2.0/24 comment=RFC6890 list=not_in_internet add address=198.51.100.0/24 comment=RFC6890 list=not_in_internet add address=203.0.113.0/24 comment=RFC6890 list=not_in_internet add address=100.64.0.0/10 comment=RFC6890 list=not_in_internet add address=240.0.0.0/4 comment=RFC6890 list=not_in_internet add address=192.88.99.0/24 comment="6to4 relay Anycast [RFC 3068]" list=not_in_internet
IPv6
Currently IPv6 package is disabled by default. Please enable package with care, as router does not have firewall at the moment.
IPv6 ND
Disable IPv6 Neighbour Discovery
/ipv6 nd set [find] disabled=yes
IPv6 firewall to a router
- work with new packets, accept established/related packets;
- drop link-local addresses from Internet interface;
- accept access to a router from link-local addresses, accept multicast addresses for management purposes, accept your address for router access;
- drop anything else;
/ipv6 firewall filter add action=accept chain=input comment="allow established and related" connection-state=established,related add action=drop chain=input in-interface=sit1 log=yes log-prefix=dropLL_from_public src-address=fe80::/16 add action=accept chain=input comment="allow allowed addresses" src-address-list=allowed add action=drop chain=input /ipv6 firewall address-list add address=fe80::/16 list=allowed add address=xxxx::/48 list=allowed add address=ff02::/16 comment=multicast list=allowed
IPv6 firewall for clients
Enabled IPv6 puts your clients available for publci networks, set proper firewall to protect your customers.
/ipv6 firewall filter * accept established/related and work with new packets; * drop invalid packets and put prefix for rules; * accept ICMP packets; * accept new connection from your clients to the Internet; * drop everything else. add action=accept chain=forward comment=established,related connection-state=established,related add action=drop chain=forward comment=invalid connection-state=invalid log=yes log-prefix=ipv6,invalid add action=accept chain=forward comment=icmpv6 in-interface=!sit1 protocol=icmpv6 add action=accept chain=forward comment="local network" in-interface=!sit1 src-address-list=allowed add action=drop chain=forward log-prefix=IPV6