Manual:VLANs on Wireless: Difference between revisions
| Line 153: | Line 153: | ||
</pre> | </pre> | ||
=Example with simple bridge and wireless vlan-mode= | ==Example with simple bridge and wireless vlan-mode== | ||
'''R1:''' | '''R1:''' | ||
Revision as of 16:59, 24 April 2018
Summary
RouterOS supports VLAN on wireless interfaces. Configuration examples contain information about VLAN cooperation with wireless interface features. Described cases work in the same way but examples show different approaches how to forward VLANs over wireless interfaces. For example we use wlan1 (Cafe Wifi users) and VirtualAP wlan2 (Wifi for company employees) on one device, and we want to separate both traffics with VLANs. The configurations are sorted by precedence of recommended usage.
Examples
Example with vlan-filtering bridge and wireless vlan-mode (Recommended)
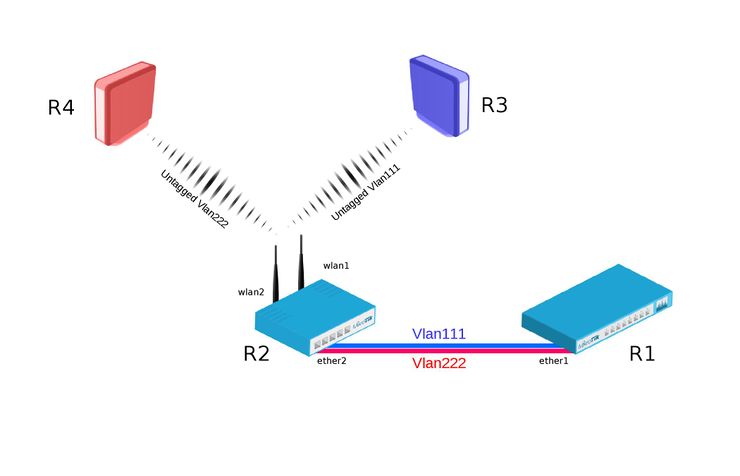
Bridge VLAN Filtering since RouterOS v6.41 provides VLAN aware Layer2 forwarding and VLAN tag modifications within the bridge.
R1:
- Add necessary VLAN interfaces on ethernet interface to make it as a VLAN trunk port. Add ip addresses on VLAN interfaces.
[admin@R1] > /interface vlan add interface=ether1 name=vlan111 vlan-id=111 add interface=ether1 name=vlan222 vlan-id=222 /ip address add address=192.168.1.1/24 interface=vlan111 network=192.168.1.0 add address=172.168.1.1/24 interface=vlan222 network=172.168.1.0
R2:
- Add VirtualAP under wlan1 interface and create wireless security-profiles for wlan1 and wlan2
[admin@R2] > /interface wireless set [ find default-name=wlan1 ] disabled=no mode=ap-bridge security-profile=vlan111 ssid=vlan111 vlan-id=111 vlan-mode=use-tag add disabled=no master-interface=wlan1 name=wlan2 security-profile=vlan222 ssid=vlan222 vlan-id=222 vlan-mode=use-tag
- Create bridge with vlan-filtering=yes
- Add necessary bridge ports
- Add tagged interfaces under interface bridge vlan section with correct vland-ids
[admin@R2] > /interface bridge add fast-forward=no name=bridge1 vlan-filtering=yes /interface bridge port add bridge=bridge1 interface=ether1 add bridge=bridge1 interface=wlan1 add bridge=bridge1 interface=wlan2 /interface bridge vlan add bridge=bridge1 tagged=ether1,wlan1 vlan-ids=111 add bridge=bridge1 tagged=ether1,wlan2 vlan-ids=222
R3:
- Add IP address on wlan1 interface.
- Create wireless security-profile compatible with R2 wlan1.
[admin@R3] > /ip address add address=192.168.1.3/24 interface=wlan1 network=192.168.1.0 /interface wireless set [ find default-name=wlan1 ] disabled=no security-profile=vlan111
R4:
- Add ip address on wlan1 interface.
- Create wireless security-profile compatible with R2 wlan2.
[admin@R4] > /ip address add address=172.168.1.4/24 interface=wlan1 network=172.168.1.0 /interface wireless set [ find default-name=wlan1 ] disabled=no security-profile=vlan222
Example with separate bridges

Warning: This type of configuration is known to cause issues with RSTP and other protocols in 6.41.x and newer versions, you should use bridge VLAN filtering method instead. This example is left for legacy reasons.
R1:
- Add necessary VLAN interfaces on ethernet interface to make it as a VLAN trunk port. Add IP addresses on VLAN interfaces.
[admin@R1] > /interface vlan add interface=ether1 name=vlan111 vlan-id=111 add interface=ether1 name=vlan222 vlan-id=222 /ip address add address=192.168.1.1/24 interface=vlan111 network=192.168.1.0 add address=172.168.1.1/24 interface=vlan222 network=172.168.1.0
R2:
- Add VirtualAP under wlan1 interface. (Also create wireless security-profiles for wlan1 and wlan2)
[admin@R2] > /interface wireless set [ find default-name=wlan1 ] disabled=no mode=ap-bridge security-profile=vlan111 ssid=vlan111 add disabled=no master-interface=wlan1 name=wlan2 security-profile=vlan222 ssid=vlan222
- Add necessary VLAN interfaces on ethernet interface to make it as a VLAN trunk port.
- Add bridges for each VLAN.
- Add VLAN interfaces to their corresponding bridges and wireless interfaces to each bridge.
[admin@R2] > /interface vlan add interface=ether1 name=vlan111-ether1 vlan-id=111 add interface=ether1 name=vlan222-ether1 vlan-id=222 /interface bridge add name=bridge-vlan111 add name=vlan222-bridge /interface bridge port add bridge=bridge-vlan111 interface=vlan111-ether1 add bridge=bridge-vlan111 interface=wlan1 add bridge=vlan222-bridge interface=vlan222-ether1 add bridge=vlan222-bridge interface=wlan2
R3:
- Add IP address on wlan1 interface.
- Create wireless security-profile compatible with R2 wlan1.
[admin@R3] > /ip address add address=192.168.1.3/24 interface=wlan1 network=192.168.1.0 /interface wireless set [ find default-name=wlan1 ] disabled=no security-profile=vlan111
R4:
- Add IP address on wlan1 interface.
- Create wireless security-profile compatible with R2 wlan2.
[admin@R4] > /ip address add address=172.168.1.4/24 interface=wlan1 network=172.168.1.0 /interface wireless set [ find default-name=wlan1 ] disabled=no security-profile=vlan222
Example with simple bridge and wireless vlan-mode
R1:
- Add necessary VLAN interfaces on ethernet interface to make it as a VLAN trunk port. Add ip addresses on VLAN interfaces.
[admin@R1] > /interface vlan add interface=ether1 name=vlan111 vlan-id=111 add interface=ether1 name=vlan222 vlan-id=222 /ip address add address=192.168.1.1/24 interface=vlan111 network=192.168.1.0 add address=172.168.1.1/24 interface=vlan222 network=172.168.1.0
R2:
- Add VirtualAP under wlan1 interface. (Also create wireless security-profiles for wlan1 and wlan2)
[admin@R2] > /interface wireless set [ find default-name=wlan1 ] disabled=no mode=ap-bridge security-profile=vlan111 ssid=vlan111 vlan-id=111 vlan-mode=use-tag add disabled=no master-interface=wlan1 name=wlan2 security-profile=vlan222 ssid=vlan222 vlan-id=222 vlan-mode=use-tag
- Add necessary VLAN interfaces on ethernet,wlan1,wlan2 interfaces.
- Add bridge for VLAN interfaces.
- Add all VLAN interfaces to bridge1.
[admin@R2] > /interface vlan add interface=ether1 name=vlan111-ether1 vlan-id=111 add interface=ether1 name=vlan222-ether1 vlan-id=222 add interface=wlan1 name=vlan111-wlan1 vlan-id=111 add interface=wlan2 name=vlan222-wlan2 vlan-id=222 /interface bridge add name=bridge1 /interface bridge port add bridge=bridge1 interface=vlan111-wlan1 add bridge=bridge1 interface=vlan222-wlan2 add bridge=bridge1 interface=vlan111-ether1 add bridge=bridge1 interface=vlan222-ether1
R3:
- Add IP address on wlan1 interface.
- Create wireless security-profile compatible with R2 wlan1.
[admin@R3] > /ip address add address=192.168.1.3/24 interface=wlan1 network=192.168.1.0 /interface wireless set [ find default-name=wlan1 ] disabled=no security-profile=vlan111
R4:
- Add ip address on wlan1 interface.
- Create wireless security-profile compatible with R2 wlan2.
[admin@R4] > /ip address add address=172.168.1.4/24 interface=wlan1 network=172.168.1.0 /interface wireless set [ find default-name=wlan1 ] disabled=no security-profile=vlan222
