Manual:CRS3xx series switches: Difference between revisions
| Line 172: | Line 172: | ||
{{ Note | On CRS3xx series switches bridge STP/RSTP/MSTP, IGMP Snooping and VLAN filtering settings don't affect hardware offloading, since RouterOS v6.42 Bonding interfaces are also hardware offloaded.}} | {{ Note | On CRS3xx series switches bridge STP/RSTP/MSTP, IGMP Snooping and VLAN filtering settings don't affect hardware offloading, since RouterOS v6.42 Bonding interfaces are also hardware offloaded.}} | ||
=VLAN= | =VLAN= | ||
Revision as of 19:21, 10 January 2019
Summary
The Cloud Router Switch series are highly integrated switches with high performance ARM CPU and feature-rich packet processor. The CRS switches can be designed into various Ethernet applications including unmanaged switch, Layer 2 managed switch, carrier switch and wired unified packet processing.
Features
| Features | Description |
|---|---|
| Forwarding |
|
| Mirroring |
|
| VLAN |
|
| Bonding |
|
| Quality of Service (QoS) |
|
| Port isolation |
|
| Access Control List |
|
Models
This table clarifies main differences between Cloud Router Switch models.
| Model | Switch Chip | CPU | Cores | Wireless | SFP+ port | Access Control List | Jumbo Frame (Bytes) |
| CRS326-24G-2S+ | Marvell-98DX3236 | 800MHz | 1 | - | + | + | 10218 |
| CRS328-24P-4S+ | Marvell-98DX3236 | 800MHz | 1 | - | + | + | 10218 |
| CRS328-4C-20S-4S+ | Marvell-98DX3236 | 800MHz | 1 | - | + | + | 10218 |
| CRS305-1G-4S+ | Marvell-98DX3236 | 800MHz | 1 | - | + | + | 10218 |
| CRS317-1G-16S+ | Marvell-98DX8216 | 800MHz | 2 | - | + | + | 10218 |
Abbreviations
- FDB - Forwarding Database
- MDB - Multicast Database
- SVL - Shared VLAN Learning
- IVL - Independent VLAN Learning
- PVID - Port VLAN ID
- ACL - Access Control List
- CVID - Customer VLAN ID
- SVID - Service VLAN ID
Port switching
In order to setup port switching on CRS3xx series switches, check the Bridge Hardware Offloading page.

Warning: Currently it is possible to create only one bridge with hardware offloading on CRS3xx series devices. Use the hw parameter to select which bridge will use hardware offloading.

Note: On CRS3xx series switches bridge STP/RSTP/MSTP, IGMP Snooping and VLAN filtering settings don't affect hardware offloading, since RouterOS v6.42 Bonding interfaces are also hardware offloaded.
VLAN
Since RouterOS v6.41 bridges provides VLAN aware Layer2 forwarding and VLAN tag modifications within the bridge. This set of features makes bridge operation more like a traditional Ethernet switch and allows to overcome Spanning Tree compatibilty issues compared to configuration when tunnel-like VLAN interfaces are bridged. Bridge VLAN Filtering configuration is highly recommended to comply with STP (802.1D), RSTP (802.1w) standards and is mandatory to enable MSTP (802.1s) support in RouterOS.
VLAN Filtering
The main VLAN setting is vlan-filtering which globally controls vlan-awareness and VLAN tag processing in the bridge. If vlan-filtering=no, bridge ignores VLAN tags, works in a shared-VLAN-learning (SVL) mode and cannot modify VLAN tags of packets. Turning on vlan-filtering enables all bridge VLAN related functionality and independent-VLAN-learning (IVL) mode. Besides joining the ports for Layer2 forwarding, bridge itself is also an interface therefore it has Port VLAN ID (pvid).

Note: Since RouterOS v6.41 all VLAN switching related parameters are moved to the bridge section. On CRS3xx series devices VLAN switching must be configured under the bridge section as well, this will not limit the device's performance, CRS3xx is designed to use the built-in switch chip to work with bridge VLAN filtering, you are able to achieve full non-blocking wire-speed switching performance while using bridges and bridge VLAN filtering. Make sure that all bridge ports have the "H" flag, which indicates that the device is using the switch chip to forward packets.
Sub-menu: /interface bridge
| Property | Description |
|---|---|
| vlan-filtering (yes | no; Default: no) | Globally enables or disables VLAN functionality for bridge. |
| pvid (1..4094; Default: 1) | Port VLAN ID (pvid) specifies which VLAN the untagged ingress traffic is assigned to. It applies e.g. to frames sent from bridge IP and destined to a bridge port. |
Sub-menu: /interface bridge port
| Property | Description |
|---|---|
| frame-types (admit-all | admit-only-untagged-and-priority-tagged | admit-only-vlan-tagged; Default: admit-all) | Specifies allowed ingress frame types on a bridge port. Only has effect when ingress-filtering is enabled. |
| ingress-filtering (yes | no; Default: no) | Enables or disables ingress filtering, which checks if an entry exists for the ingress port and the VLAN ID in the bridge VLAN table. Should be used with frame-types to specify if the ingress traffic should be tagged or untagged. |
| pvid (1..4094; Default: 1) | Port VLAN ID (pvid) specifies which VLAN the untagged ingress traffic is assigned to. |
VLAN Table
Bridge VLAN table represents per-VLAN port mapping with an egress VLAN tag action.
tagged ports send out frames with a learned VLAN ID tag.
untagged ports remove VLAN tag before sending out frames if the learned VLAN ID matches the port pvid.
Sub-menu: /interface bridge vlan
| Property | Description |
|---|---|
| bridge (name) | The bridge interface which the respective VLAN entry is intended for. |
| disabled (yes | no; Default: no) | Enables or disables Bridge VLAN entry. |
| tagged (interfaces; Default: none) | Interface list with a VLAN tag adding action in egress. This setting accepts comma separated values. E.g. tagged=ether1,ether2. |
| untagged (interfaces; Default: none) | Interface list with a VLAN tag removing action in egress. This setting accepts comma separated values. E.g. tagged=ether3,ether4. |
| vlan-ids (1..4094) | The list of VLAN IDs for certain port configuration. This setting accepts VLAN ID range as well as comma separated values. E.g. vlan-ids=100-115,120,122,128-130. |
Setup examples
Port Based VLAN
- The configuration for CRS3xx switches is described in the Bridge VLAN FIltering section.

Note: It is possible to use the built-in switch chip and the CPU at the same time to create a Switch-Router setup, where a device acts as a switch and as a router at the same time. You can find a configuration example in the CRS-Router guide.
MAC Based VLAN
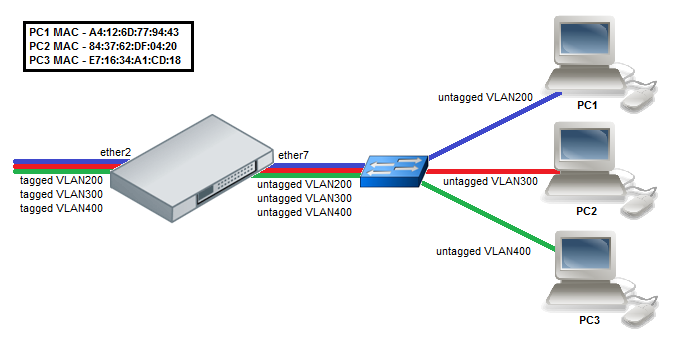

Note: The CRS3xx Switch Rule table is used for MAC Based VLAN functionality, it supports up to 128 entries.
- Enable switching on ports by creating a bridge with enabled hw-offloading.
/interface bridge add name=bridge1 vlan-filtering=yes /interface bridge port add bridge=bridge1 interface=ether2 hw=yes add bridge=bridge1 interface=ether7 hw=yes
- Add VLANs in the Bridge VLAN table and specify ports.
/interface bridge vlan add bridge=bridge1 tagged=ether2 untagged=ether7 vlan-ids=200,300,400
- Add Switch rules which assign VLAN id based on MAC address.
/interface ethernet switch rule add switch=switch1 ports=ether7 src-mac-address=A4:12:6D:77:94:43/FF:FF:FF:FF:FF:FF new-vlan-id=200 add switch=switch1 ports=ether7 src-mac-address=84:37:62:DF:04:20/FF:FF:FF:FF:FF:FF new-vlan-id=300 add switch=switch1 ports=ether7 src-mac-address=E7:16:34:A1:CD:18/FF:FF:FF:FF:FF:FF new-vlan-id=400
Protocol Based VLAN
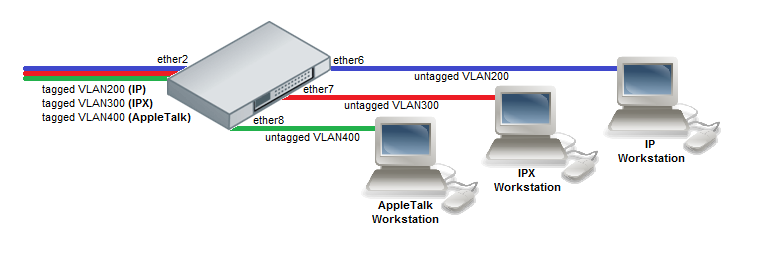

Note: The CRS3xx Switch Rule table is used for Protocol Based VLAN functionality, it supports up to 128 entries.
- Enable switching on ports by creating a bridge with enabled hw-offloading.
/interface bridge add name=bridge1 vlan-filtering=yes /interface bridge port add bridge=bridge1 interface=ether2 hw=yes add bridge=bridge1 interface=ether6 hw=yes add bridge=bridge1 interface=ether7 hw=yes add bridge=bridge1 interface=ether8 hw=yes
- Add VLANs in the Bridge VLAN table and specify ports.
/interface bridge vlan add bridge=bridge1 tagged=ether2 untagged=ether6 vlan-ids=200 add bridge=bridge1 tagged=ether2 untagged=ether7 vlan-ids=300 add bridge=bridge1 tagged=ether2 untagged=ether8 vlan-ids=400
- Add Switch rules which assign VLAN id based on MAC protocol.
/interface ethernet switch rule add mac-protocol=ip new-vlan-id=200 ports=ether6 switch=switch1 add mac-protocol=ipx new-vlan-id=300 ports=ether7 switch=switch1 add mac-protocol=0x80F3 new-vlan-id=400 ports=ether8 switch=switch1
VLAN Tunneling (Q-in-Q)
Since RouterOS v6.43 it is possible to use a provider bridge (IEEE 802.1ad) VLAN filtering and hardware offloading at the same time on CRS3xx series switches. The configuration for CRS3xx switches is described in the Bridge VLAN Tunneling (Q-in-Q) section.
Ingress VLAN translation
It is possible to translate a certain VLAN ID to a different VLAN ID using ACL rules on an ingress port. In this example we create two ACL rules, allowing a bidirectional communication. This can be done by doing the following:
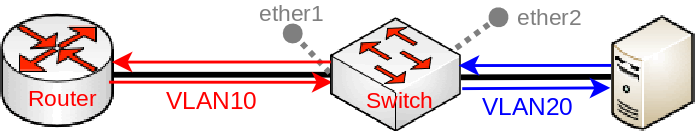
- Create a new bridge and add ports to it with hardware offloading:
/interface bridge add name=bridge1 vlan-filtering=no /interface bridge port add interface=ether1 bridge=bridge1 hw=yes add interface=ether2 bridge=bridge1 hw=yes
- Add ACL rules to translate a VLAN ID in each direction:
/interface ethernet switch rule add new-vlan-id=20 ports=ether1 switch=switch1 vlan-id=10 add new-vlan-id=10 ports=ether2 switch=switch1 vlan-id=20
- Add both VLAN IDs to the bridge VLAN table:
/interface bridge vlan add bridge=bridge1 tagged=ether1 vlan-ids=10 add bridge=bridge1 tagged=ether2 vlan-ids=20
- Enable bridge VLAN filtering:
/interface bridge set bridge1 vlan-filtering=yes

Warning: By enabling vlan-filtering you will be filtering out traffic destined to the CPU, before enabling VLAN filtering you should make sure that you set up a Management port
(R/M)STP
CRS3xx series switches are capable of running STP, RSTP and MSTP on a hardware level. For more detailed information you should check out the Spanning Tree Protocol manual page.
Bonding
Since RouterOS v6.42 all CRS3xx series switches support hardware offloading with bonding interfaces. Only 802.3ad and balance-xor bonding modes are hardware offloaded, other bonding modes will use the CPU's resources. You can find more information about the bonding interfaces in the Bonding Interface section. If 802.3ad mode is used, then LACP (Link Aggregation Control Protocol) is supported.
To create a hardware offloaded bonding interface, you must create a bonding interface with a supported bonding mode:
/interface bonding add mode=802.3ad name=bond1 slaves=ether1,ether2
This interface can be added to a bridge alongside with other interfaces:
/interface bridge add name=bridge /interface bridge port add bridge=bridge interface=bond1 hw=yes add bridge=bridge interface=ether3 hw=yes add bridge=bridge interface=ether4 hw=yes

Note: Don't add interfaces to a bridge that are already in a bond, RouterOS will not allow you to add an interface that is already a slave to a bridge as there is no need to do it since a bonding interface already contains the slave interfaces.
Make sure that the bonding interface is hardware offloaded by checking the "H" flag:
/interface bridge port print Flags: X - disabled, I - inactive, D - dynamic, H - hw-offload # INTERFACE BRIDGE HW 0 H bond1 bridge yes 1 H ether3 bridge yes 2 H ether4 bridge yes

Note: The built-in switch chip will always use Layer2+Layer3+Layer4 for transmit hash policy, changing the transmit hash policy manually will have no effect.
Port isolation
Since RouterOS v6.43 is it possible to create a Private VLAN setup on CRS3xx series switches, example can be found in the Switch chip port isolation manual page.
IGMP Snooping
CRS3xx series switches are capable of using IGMP Snooping on a hardware level. To see more detailed information, you should check out the IGMP Snooping manual page.
DHCP Snooping and DHCP Option 82
CRS3xx series switches are capable of using DHCP Snooping with Option 82 on a hardware level. To see more detailed information, you should check out the DHCP Snooping and DHCP Option 82 manual page.
Mirroring
Mirroring lets the switch 'sniff' all traffic that is going in a switch chip and send a copy of those packets out to another port (mirror-target). This feature can be used to easily set up a 'tap' device that allows you to inspect the traffic on your network on a traffic analyzer device. It is possible to set up a simple port based mirroring where, but it is also possible to setup more complex mirroring based on various parameters. Note that mirror-target port has to belong to same switch. (See which port belong to which switch in /interface ethernet menu). Also mirror-target can have a special 'cpu' value, which means that 'sniffed' packets will be sent out of switch chips cpu port. There are many possibilities that can be used to mirror certain traffic, below you can find most common mirroring examples:
- Port Based Mirroring
/interface ethernet switch set switch1 mirror-source=ether2 mirror-target=ether3
- VLAN Based Mirroring
/interface bridge set bridge1 vlan-filtering=yes /interface ethernet switch set switch1 mirror-target=ether3 mirror-source=none /interface ethernet switch rule add mirror=yes ports=ether1 switch=switch1 vlan-id=11

Warning: By enabling vlan-filtering you will be filtering out traffic destined to the CPU, before enabling VLAN filtering you should make sure that you set up a Management port
- MAC Based Mirroring
/interface ethernet switch set switch1 mirror-target=ether3 mirror-source=none /interface ethernet switch rule add mirror=yes ports=ether1 switch=switch1 dst-mac-address=64:D1:54:D9:27:E6/FF:FF:FF:FF:FF:FF add mirror=yes ports=ether1 switch=switch1 src-mac-address=64:D1:54:D9:27:E6/FF:FF:FF:FF:FF:FF
- Protocol Based Mirroring
/interface ethernet switch set switch1 mirror-target=ether3 mirror-source=none /interface ethernet switch rule add mirror=yes ports=ether1 switch=switch1 mac-protocol=ipx
- IP Based Mirroring
/interface ethernet switch set switch1 mirror-target=ether3 mirror-source=none /interface ethernet switch rule add mirror=yes ports=ether1 switch=switch1 src-address=192.168.88.0/24 add mirror=yes ports=ether1 switch=switch1 dst-address=192.168.88.0/24
There are other options as well, check the ACL section to find out all possible parameters that can be used to match packets.
Quality of Service (QoS)
It is possible to limit certain type of traffic using ACL rules. For CRS3xx series switches it is possible to limit ingress traffic that matches certain parameters and it is possible to limit ingress/egress traffic per port basis. For ingress traffic QoS policer is used, for egress traffic QoS shaper is used.
- Port Based QoS
/interface ethernet switch port set ether1 ingress-rate=10M egress-rate=5M
- MAC Based QoS
/interface ethernet switch rule add ports=ether1 switch=switch1 src-mac-address=64:D1:54:D9:27:E6/FF:FF:FF:FF:FF:FF rate=10M
- VLAN Based QoS
/interface bridge set bridge1 vlan-filtering=yes /interface ethernet switch rule add ports=ether1 switch=switch1 vlan-id=11 rate=10M

Warning: By enabling vlan-filtering you will be filtering out traffic destined to the CPU, before enabling VLAN filtering you should make sure that you set up a Management port
- Protocol Based QoS
/interface ethernet switch rule add ports=ether1 switch=switch1 mac-protocol=ipx rate=10M
There are other options as well, check the ACL section to find out all possible parameters that can be used to match packets.
Traffic Storm Control
Since RouterOS v6.42 it is possible to enable traffic storm control on CRS3xx series devices. It is possible to limit broadcast, unknown multicast and unknown unicast traffic. These settings should be applied to ingress ports, the egress traffic will be limited.

Note: The storm control parameter is specified in percentage (%) of the link speed. If your link speed is 1Gbps, then specifying storm-rate as 10 will allow only 100Mbps of broadcast, unknown multicast and/or unknown unicast traffic to be forwarded.
Sub-menu: /interface ethernet switch port
| Property | Description |
|---|---|
| limit-broadcasts (yes | no; Default: yes) | Limit broadcast traffic on switch port. |
| limit-unknown-multicasts (yes | no; Default: no) | Limit unknown multicast traffic on switch port. |
| limit-unknown-unicasts (yes | no; Default: no) | Limit unknown unicast traffic on switch port. |
| storm-rate (integer 0..100; Default: 100) | Amount of broadcast, unknown multicast and/or unknown unicast traffic is limited to in percentage of the link speed. |

Warning: Devices with Marvell-98DX3236 switch chip cannot distinguish unknown multicast traffic from all multicast traffic. For example, CRS326-24G-2S+ will limit all multicast traffic when limit-unknown-multicasts and storm-rate is used. For other devices, for example, CRS317-1G-16S+ the limit-unknown-multicasts parameter will limit only unknown multicast traffic (addresses that are not present in /interface bridge mdb
- For example, to limit 1% (10Mbps) of broadcast and unknown unicast traffic on ether1 (1Gbps), use the following commands:
/interface ethernet switch port set ether1 storm-rate=1 limit-broadcasts=yes limit-unknown-unicasts=yes
MPLS hardware offloading
Since RouterOS v6.41 it is possible to offload certain MPLS functions to the switch chip, the switch must be a (P)rovider router in a PE-P-PE setup in order to achieve hardware offloading. Setup example can be found in the Basic MPLS setup example manual page.

Note: Currently only CRS317-1G-16S+ using RouterOS v6.41 and newer is capable of hardware offloading certain MPLS functions. CRS317-1G-16S+ built-in switch chip is not capable of popping MPLS labels from packets, in a PE-P-PE setup you either have to use explicit null or disable TTL propagation in MPLS network to achieve hardware offloading.
Switch Rules (ACL)
Access Control List contains of ingress policy and egress policy engines and allows to configure up to 128 policy rules (limited by RouterOS). It is advanced tool for wire-speed packet filtering, forwarding and modifying based on Layer2, Layer3 and Layer4 protocol header field conditions.

Note: ACL rules are checked for each packet until a match has been found. If there are multiple rules that can match, then only the first rule will be triggered. A rule without any action parameters is a rule to accept the packet.
Sub-menu: /interface ethernet switch rule
| Property | Description |
|---|---|
| copy-to-cpu (no | yes; Default: no) | Clones the matching packet and sends it to the CPU. |
| disabled (yes | no; Default: no) | Enables or disables ACL entry. |
| dscp (0..63) | Matching DSCP field of the packet. |
| dst-address (IP address/Mask) | Matching destination IP address and mask. |
| dst-address6 (IPv6 address/Mask) | Matching destination IPv6 address and mask. |
| dst-mac-address (MAC address/Mask) | Matching destination MAC address and mask. |
| dst-port (0..65535) | Matching destination protocol port number. |
| flow-label (0..1048575) | Matching IPv6 flow label. |
| mac-protocol (802.2 | arp | homeplug-av | ip | ipv6 | ipx | lldp | loop-protect | mpls-multicast | mpls-unicast | packing-compr | packing-simple | pppoe | pppoe-discovery | rarp | service-vlan | vlan | or 0..65535 | or 0x0000-0xffff) | Matching particular MAC protocol specified by protocol name or number |
| mirror (no | yes) | Clones the matching packet and sends it to the mirror-target port. |
| new-dst-ports (ports) | Changes the destination port as specified. An empty setting will drop the packet. A specified port will redirect the packet to it. When the parameter is not used, the packet will be accepted. Multiple "new-dst-ports" are not supported on CRS3xx series switches. |
| new-vlan-id (0..4095) | Changes the VLAN ID to the specified value. Requires vlan-filtering=yes. |
| new-vlan-priority (0..7) | Changes the VLAN priority tag. Requires vlan-filtering=yes. |
| ports (ports) | Matching ports on which will the rule apply on received traffic. |
| protocol (dccp | ddp | egp | encap | etherip | ggp | gre | hmp | icmp | icmpv6 | idpr-cmtp | igmp | ipencap | ipip | ipsec-ah | ipsec-esp | ipv6 | ipv6-frag | ipv6-nonxt | ipv6-opts | ipv6-route | iso-tp4 | l2tp | ospf | pim | pup | rdp | rspf | rsvp | sctp | st | tcp | udp | udp-lite | vmtp | vrrp | xns-idp | xtp | or 0..255) | Matching particular IP protocol specified by protocol name or number. |
| redirect-to-cpu (no | yes) | Changes the destination port of a matching packet to the CPU. |
| src-address (IP address/Mask) | Matching source IP address and mask. |
| src-address6 (IPv6 address/Mask) | Matching source IPv6 address and mask. |
| src-mac-address (MAC address/Mask) | Matching source MAC address and mask. |
| src-port (0..65535) | Matching source protocol port number. |
| switch (switch group) | Matching switch group on which will the rule apply. |
| traffic-class (0..255) | Matching IPv6 traffic class. |
| vlan-id (0..4095) | Matching VLAN ID. Requires vlan-filtering=yes. |
| vlan-header (not-present | present) | Matching VLAN header, whether the VLAN header is present or not. |
| vlan-priority (0..7) | Matching VLAN priority. |
Action parameters:
- copy-to-cpu
- redirect-to-cpu
- mirror
- new-dst-ports (can be used to drop packets)
- new-vlan-id
- new-vlan-priority
- rate
Conditional parameters:
- Layer2 conditions:
- dst-mac-address
- mac-protocol
- src-mac-address
- vlan-id
- vlan-header
- vlan-priority
- Layer3 conditions:
- dscp
- protocol
- IPv4 conditions:
- dst-address
- src-address
- IPv6 conditions:
- dst-address6
- flow-label
- src-address6
- traffic-class
- Layer4 conditions:
- dst-port
- src-port

Note: For VLAN related matchers or VLAN related action parameters to work, you need to enable vlan-filtering on the bridge interface and make sure that hardware offloading is enabled on those ports, otherwise these parameters will not have any effect.

Warning: When vlan-protocol is set to 802.1Q, then VLAN related ACL rules are relevant to 0x8100 (CVID) packets, this includes vlan-id and new-vlan-id. When vlan-protocol is set to 802.1ad, then ACL rules are relevant to 0x88A8 (SVID) packets. For example, with 802.1Q the vlan-id matcher will match CVID packets, but with 802.1ad the vlan-id matcher will match SVID packets.
Port Security
It is possible to limit allowed MAC addresses on a single switch port on CRS3xx series switches. For example, to allow 64:D1:54:81:EF:8E start by switching multiple ports together, in this example 64:D1:54:81:EF:8E is going to be located behind ether1.
- Create an ACL rule to allow the given MAC address and drop all other traffic on ether1 (for ingress traffic):
/interface ethernet switch rule add ports=ether1 src-mac-address=64:D1:54:81:EF:8E/FF:FF:FF:FF:FF:FF switch=switch1 add new-dst-ports="" ports=ether1 switch=switch1
- Switch all required ports together, disable MAC learning and disable unknown unicast flooding on ether1:
/interface bridge add name=bridge1 /interface bridge port add bridge=bridge1 interface=ether1 hw=yes learn=no unknown-unicast-flood=no add bridge=bridge1 interface=ether2 hw=yes
- Add a static hosts entry for
64:D1:54:81:EF:8E(for egress traffic):
/interface bridge host add bridge=bridge1 interface=ether1 mac-address=64:D1:54:81:EF:8E

Warning: Broadcast traffic will still be sent out from ether1. To limit broadcast traffic flood on a bridge port, you can use the broadcast-flood parameter to toggle it. Do note that some protocols depend on broadcast traffic, such as streaming protocols and DHCP.
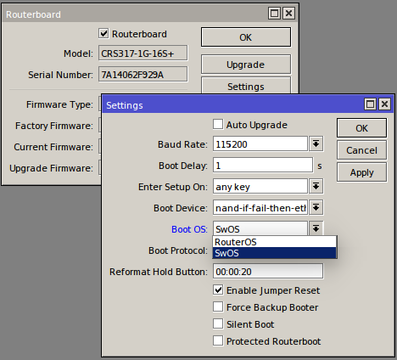
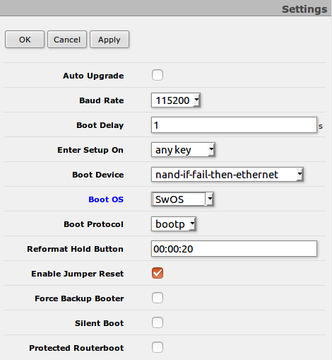
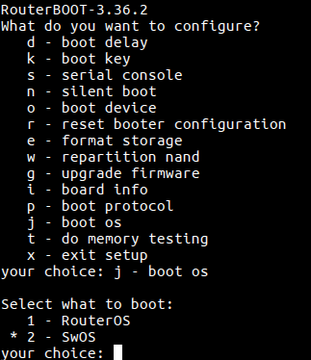
Dual Boot
“Dual boot” feature allows you to choose which operating system you prefer to use, RouterOS or SwOS. Device operating system could be changed using:
- Serial Terminal (/system routerboard settings set boot-os=swos)
- Winbox
- Webfig
- Serial Console
 |
 |
 |
More details about SwOS are described here: SwOS manual
Configuring SwOS using RouterOS
Since RouterOS 6.43 it is possible to load, save and reset SwOS configuration, as well as upgrade SwOS and set an IP address for the switch by using RouterOS.
- Save configuration with
/system swos save-config

Note: Configuration will be saved on the same device with swos.config as filename, make sure you download the file off your device since the configuration file will be removed after a reboot.
- Load configuration with
/system swos load-config
- Reset configuration with
/system swos reset-config
- Set static IP address with
/system swos set-address

Note: By setting a static IP address you are not changing the IP address acquisition process, which is DHCP with fallback by default. This means that the configured static IP address will become active only when there is going to be no DHCP servers in the same broadcast domain.
- Upgrade SwOS from RouterOS using
/system swos upgrade

Note: The upgrade command will automatically install the latest available SwOS version, make sure that your device has access to the Internet in order for the upgrade process to work properly.
See also
- CRS Router
- CRS3xx VLANs with Bonds
- Basic VLAN switching
- Bridge Hardware Offloading
- Spanning Tree Protocol
- IGMP Snooping
- DHCP Snooping and Option 82
- MTU on RouterBOARD
- Layer2 misconfiguration
- Bridge VLAN Table
[ Top | Back to Content ]
