Manual:Interface/EoIP: Difference between revisions
| Line 58: | Line 58: | ||
<tr> | <tr> | ||
<td><var><b>ipsec-secret</b></var> (<em>string</em>; Default: <b></b>)</td> | <td><var><b>ipsec-secret</b></var> (<em>string</em>; Default: <b></b>)</td> | ||
<td>When secret is specified, router adds dynamic ipsec peer to remote-address with pre-shared key and policy with default values (by default phase2 uses sha1/aes128cbc) | <td>When secret is specified, router adds dynamic ipsec peer to remote-address with pre-shared key and policy with default values (by default phase2 uses sha1/aes128cbc).</td> | ||
<tr> | <tr> | ||
<tr> | <tr> | ||
Revision as of 18:06, 19 December 2019
Summary
Sub-menu: /interface eoip
Standards: GRE RFC 1701
Ethernet over IP (EoIP) Tunneling is a MikroTik RouterOS protocol that creates an Ethernet tunnel between two routers on top of an IP connection. The EoIP tunnel may run over IPIP tunnel, PPTP tunnel or any other connection capable of transporting IP.
When the bridging function of the router is enabled, all Ethernet traffic (all Ethernet protocols) will be bridged just as if there where a physical Ethernet interface and cable between the two routers (with bridging enabled). This protocol makes multiple network schemes possible.
Network setups with EoIP interfaces:
- Possibility to bridge LANs over the Internet
- Possibility to bridge LANs over encrypted tunnels
- Possibility to bridge LANs over 802.11b 'ad-hoc' wireless networks
The EoIP protocol encapsulates Ethernet frames in GRE (IP protocol number 47) packets (just like PPTP) and sends them to the remote side of the EoIP tunnel.
Properties
| Property | Description |
|---|---|
| arp (disabled | enabled | proxy-arp | reply-only; Default: enabled) | Address Resolution Protocol mode.
|
| clamp-tcp-mss (yes | no; Default: yes) | |
| dont-fragment (inherit | no; Default: no) | |
| dscp (integer: 0-63; Default: inherited) | DSCP value of packet. Inherited option means that dscp value will be inherited from packet which is going to be encapsulated. |
| ipsec-secret (string; Default: ) | When secret is specified, router adds dynamic ipsec peer to remote-address with pre-shared key and policy with default values (by default phase2 uses sha1/aes128cbc). |
| keepalive (integer[/time],integer 0..4294967295; Default: 10s,10) | Tunnel keepalive parameter sets the time interval in which the tunnel running flag will remain even if the remote end of tunnel goes down. If configured time,retries fail, interface running flag is removed.
Parameters are written in following format: KeepaliveInterval,KeepaliveRetries where KeepaliveInterval is time interval and KeepaliveRetries - number of retry attempts. By default keepalive is set to 10 seconds and 10 retries. |
| l2mtu (integer; read-only) | Layer2 Maximum transmission unit. Not configurable for EoIP. Read more>> |
| local-address (IP; Default: ) | Source address of the tunnel packets, local on the router. |
| mac-address (MAC; Default: ) | Media Access Control number of an interface. The address numeration authority IANA allows the use of MAC addresses in the range from 00:00:5E:80:00:00 - 00:00:5E:FF:FF:FF freely |
| mtu (integer; Default: auto) | Layer3 Maximum transmission unit |
| name (string; Default: ) | Interface name |
| remote-address (IP; Default: ) | IP address of remote end of EoIP tunnel |
| tunnel-id (integer: 65536; Default: ) | Unique tunnel identifier, which must match other side of the tunnel |
Notes
tunnel-id is method of identifying tunnel. It must be unique for each EoIP tunnel.
mtu should be set to 1500 to eliminate packet refragmentation inside the tunnel (that allows transparent bridging of Ethernet-like networks, so that it would be possible to transport full-sized Ethernet frame over the tunnel).
When bridging EoIP tunnels, it is highly recommended to set unique MAC addresses for each tunnel for the bridge algorithms to work correctly. For EoIP interfaces you can use MAC addresses that are in the range from 00:00:5E:80:00:00 - 00:00:5E:FF:FF:FF , which IANA has reserved for such cases. Alternatively, you can set the second bit of the first byte to modify the auto-assigned address into a 'locally administered address', assigned by the network administrator and thus use any MAC address, you just need to ensure they are unique between the hosts connected to one bridge.
Setup examples
Let us assume we want to bridge two networks: 'Office LAN' and 'Remote LAN'. By using EoIP setup can be made so that Office and Remote LANs are in the same Layer2 broadcast domain.
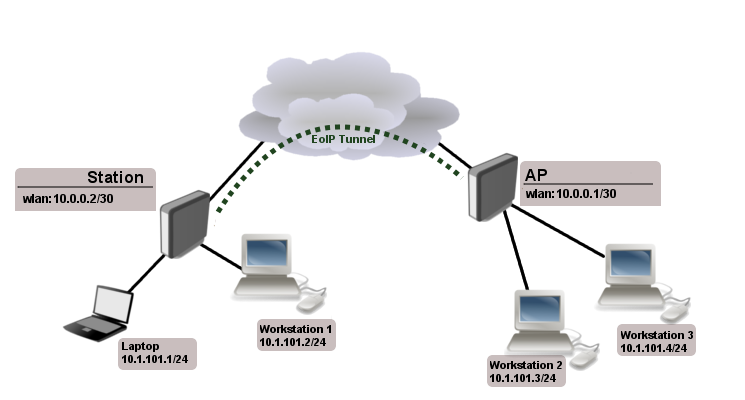
Consider following setup:
As you know wireless station cannot be bridged, to overcome this limitation (not involving WDS) we will create EoIP tunnel over the wireless link and bridge it with interfaces connected to local networks.
We will not cover wireless configuration in this example, lets assume that wireless link is already established
At first we create EoIP tunnel on our gateway ...
[admin@Our_GW] interface eoip> add name="eoip-remote" tunnel-id=0 \ \... remote-address=10.0.0.2 [admin@Our_GW] interface eoip> enable eoip-remote [admin@Our_GW] interface eoip> print Flags: X - disabled, R - running 0 name=eoip-remote mtu=1500 arp=enabled remote-address=10.0.0.2 tunnel-id=0 [admin@Our_GW] interface eoip>
... and on Remote router
[admin@Remote] interface eoip> add name="eoip-main" tunnel-id=0 \ \... remote-address=10.0.0.1 [admin@Remote] interface eoip> enable eoip-main [admin@Remote] interface eoip> print Flags: X - disabled, R - running 0 name=eoip mtu=1500 arp=enabled remote-address=10.0.0.1 tunnel-id=0 [admin@Remote] interface eoip>
Next step is to bridge local interfaces with EoIP tunnel On Our GW ...
[admin@Our_GW] interface bridge> add
[admin@Our_GW] interface bridge> print
Flags: X - disabled, R - running
0 R name="bridge1" mtu=1500 arp=enabled mac-address=00:00:00:00:00:00
protocol-mode=none priority=0x8000 auto-mac=yes
admin-mac=00:00:00:00:00:00 max-message-age=20s forward-delay=15s
transmit-hold-count=6 ageing-time=5m
[admin@Our_GW] interface bridge> port add bridge=bridge1 interface=eoip-remote
[admin@Our_GW] interface bridge> port add bridge=bridge1 interface=office-eth
[admin@Our_GW] interface bridge> port print
Flags: X - disabled, I - inactive, D - dynamic
# INTERFACE BRIDGE PRIORITY PATH-COST
0 eoip-remote bridge1 128 10
1 office-eth bridge1 128 10
[admin@Our_GW] interface bridge>
... and Remote router:
[admin@Remote] interface bridge> add
[admin@Remote] interface bridge> print
Flags: X - disabled, R - running
0 R name="bridge1" mtu=1500 arp=enabled mac-address=00:00:00:00:00:00
protocol-mode=none priority=0x8000 auto-mac=yes
admin-mac=00:00:00:00:00:00 max-message-age=20s forward-delay=15s
transmit-hold-count=6 ageing-time=5m
[admin@Remote] interface bridge> port add bridge=bridge1 interface=ether
[admin@Remote] interface bridge> port add bridge=bridge1 interface=eoip-main
[admin@Remote] interface bridge> port print
Flags: X - disabled, I - inactive, D - dynamic
# INTERFACE BRIDGE PRIORITY PATH-COST
0 ether bridge1 128 10
1 eoip-main bridge1 128 10
[admin@Remote] interface bridge>
Now both sites are in the same Layer2 broadcast domain. You can set up IP addresses from the same network on both sites.
[ Top | Back to Content ]