Manual:IP/Firewall/Connection tracking: Difference between revisions
Jump to navigation
Jump to search
No edit summary |
|||
| Line 15: | Line 15: | ||
=== Properties === | === Properties === | ||
All properties in connection list are read-only | |||
{{Mr-arg-table-h | |||
|prop=Property | |||
|desc=Description | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=seen reply | |||
|type=yes {{!}} no | |||
|desc= | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=assured | |||
|type=yes {{!}} no | |||
|desc= | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=connection-mark | |||
|type=string | |||
|desc=connection mark set by [[M:IP/Firewall/Mangle | mangle]] rule. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=connection-type | |||
|type=pptp {{!}} ftp {{!}} p2p | |||
|desc=Type of connection, property is empty if connection tracking is unable to determine predefined connection type. | |||
{{Mr-arg-ro-table | |||
|arg=dst-address | |||
|type=ip[:port] | |||
|desc=Destination address and port (if protocol is port based). | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=gre-key | |||
|type=integer | |||
|desc= | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=gre-version | |||
|type=string | |||
|desc= | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=icmp-code | |||
|type=string | |||
|desc= | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=icmp-id | |||
|type=string | |||
|desc= | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=icmp-type | |||
|type=string | |||
|desc= | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=p2p | |||
|type=yes {{!}} no | |||
|desc=Shows if connection is identified as p2p by firewall p2p matcher. | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=protocol | |||
|type=string | |||
|desc=IP protocol type | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=reply-dst-address | |||
|type=ip[:port] | |||
|desc= | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=reply-src-address | |||
|type=ip[:port] | |||
|desc= | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=src-address | |||
|type=ip[:port] | |||
|desc=Source address and port (if protocol is port based). | |||
}} | |||
{{Mr-arg-ro-table | |||
|arg=tcp-state | |||
|type=string | |||
|desc=Current state of TCP connection ( for exampe "established", "time-wait", "close", etc) | |||
}} | |||
{{Mr-arg-ro-table-end | |||
|arg=timeout | |||
|type=time | |||
|desc=Time after connection will be removed from connection list. | |||
}} | |||
==Connection tracking settings== | ==Connection tracking settings== | ||
Revision as of 14:16, 19 May 2011
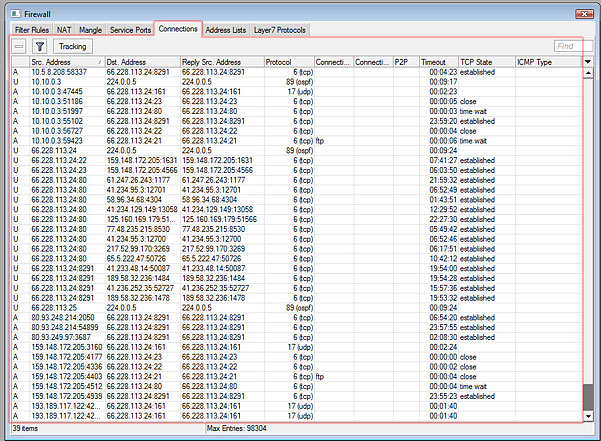
Connection tracking entries
Sub-menu: /ip firewall connection
There are several ways to see what connections are making their way though the router.
In the Winbox Firewall window, you can switch to the Connections tab, to see current connections to/from/through your router. It looks like this:
Properties
All properties in connection list are read-only
{{Mr-arg-ro-table |arg=connection-type |type=pptp | ftp | p2p |desc=Type of connection, property is empty if connection tracking is unable to determine predefined connection type.| Property | Description |
|---|---|
| seen reply (yes | no) | |
| assured (yes | no) | |
| connection-mark (string) | connection mark set by mangle rule. |
| dst-address (ip[:port]) | Destination address and port (if protocol is port based). |
| gre-key (integer) | |
| gre-version (string) | |
| icmp-code (string) | |
| icmp-id (string) | |
| icmp-type (string) | |
| p2p (yes | no) | Shows if connection is identified as p2p by firewall p2p matcher. |
| protocol (string) | IP protocol type |
| reply-dst-address (ip[:port]) | |
| reply-src-address (ip[:port]) | |
| src-address (ip[:port]) | Source address and port (if protocol is port based). |
| tcp-state (string) | Current state of TCP connection ( for exampe "established", "time-wait", "close", etc) |
| timeout (time) | Time after connection will be removed from connection list. |
Connection tracking settings
Sub-menu: /ip firewall connection tracking
Properties
| Property | Description |
|---|---|
| enabled (yes | no; Default: yes) | Allows to disable or enable connection tracking. Disabling connection tracking will cause several firewall features to stop working. See the list of affected features. |
| tcp-syn-sent-timeout (time; Default: 5s) | TCP SYN timeout. |
| tcp-syn-received-timeout (time; Default: 5s) | TCP SYN timeout. |
| tcp-established-timeout (time; Default: 1d) | Time when established TCP connection times out. |
| tcp-fin-wait-timeout (time; Default: 10s) | |
| tcp-close-wait-timeout (time; Default: 10s) | |
| tcp-last-ack-timeout (time; Default: 10s) | |
| tcp-time-wait-timeout (time; Default: 10s) | |
| tcp-close-timeout (time; Default: 10s) | |
| udp-timeout (time; Default: 10s) | |
| udp-stream-timeout (time; Default: 3m) | |
| icmp-timeout (time; Default: 10s) | |
| generic-timeout (time; Default: 10m) | Timeout for all other connection entries |
| tcp-syncookie (yes | no; Default: no) |
Read-only properties
| Property | Description |
|---|---|
| max-entries (integer) | Max amount of entries that connection tracking table can hold. This value depends on installed amount of RAM. |
| total-entries (integer) | Amount of connections that currently connection table holds. |
Features affected by connection tracking
- NAT
- firewall:
- connection-bytes
- connection-mark
- connection-type
- connection-state
- connection-limit
- connection-rate
- layer7-protocol
- p2p
- new-connection-mark
- tarpit
- p2p matching in simple queues