Manual:CRS1xx/2xx series switches examples: Difference between revisions
| Line 25: | Line 25: | ||
</pre> | </pre> | ||
* Add initial VLAN assignments to VLAN access ports. | * Add initial VLAN assignments (PVID) to VLAN access ports. | ||
<pre> | <pre> | ||
| Line 41: | Line 41: | ||
add tagged-ports=ether2 vlan-id=300 | add tagged-ports=ether2 vlan-id=300 | ||
add tagged-ports=ether2 vlan-id=400 | add tagged-ports=ether2 vlan-id=400 | ||
</pre> | |||
* The last required thing for proper isolation is VLAN membership definition in the VLAN table. Adding entries with VLAN id and ports makes that VLAN traffic valid on those ports. After valid VLAN configuration unknown/invalid VLAN forwarding can be disabled in global switch settings. | |||
<pre> | |||
/interface ethernet switch vlan | |||
add ports=ether2,ether6 vlan-id=200 learn=yes | |||
add ports=ether2,ether7 vlan-id=300 learn=yes | |||
add ports=ether2,ether8 vlan-id=400 learn=yes | |||
/interface ethernet switch | |||
set drop-if-invalid-or-src-port-not-member-of-vlan-on-ports=ether2,ether6,ether7,ether8 | |||
</pre> | </pre> | ||
Revision as of 07:19, 3 June 2014
Summary
Basic switch-chip configuration examples for Cloud Router Switch.
VLAN
Port Based VLAN
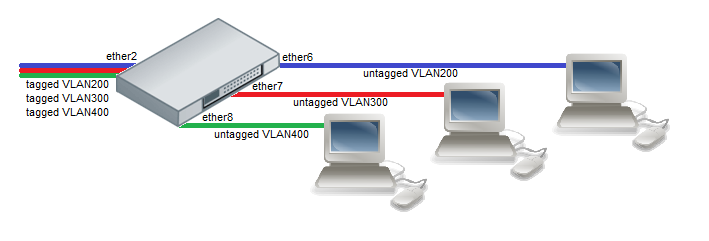
- Create a group of switched ports.
/interface ethernet set ether6 master-port=ether2 set ether7 master-port=ether2 set ether8 master-port=ether2
- Add initial VLAN assignments (PVID) to VLAN access ports.
/interface ethernet switch ingress-vlan-translation add ports=ether6 customer-vid=0 new-customer-vid=200 sa-learning=yes add ports=ether7 customer-vid=0 new-customer-vid=300 sa-learning=yes add ports=ether8 customer-vid=0 new-customer-vid=400 sa-learning=yes
- Add VLAN 200, VLAN 300 and VLAN 400 tagging on ether2 port to create it as VLAN trunk port.
/interface ethernet switch egress-vlan-tag add tagged-ports=ether2 vlan-id=200 add tagged-ports=ether2 vlan-id=300 add tagged-ports=ether2 vlan-id=400
- The last required thing for proper isolation is VLAN membership definition in the VLAN table. Adding entries with VLAN id and ports makes that VLAN traffic valid on those ports. After valid VLAN configuration unknown/invalid VLAN forwarding can be disabled in global switch settings.
/interface ethernet switch vlan add ports=ether2,ether6 vlan-id=200 learn=yes add ports=ether2,ether7 vlan-id=300 learn=yes add ports=ether2,ether8 vlan-id=400 learn=yes /interface ethernet switch set drop-if-invalid-or-src-port-not-member-of-vlan-on-ports=ether2,ether6,ether7,ether8
Protocol Based VLAN
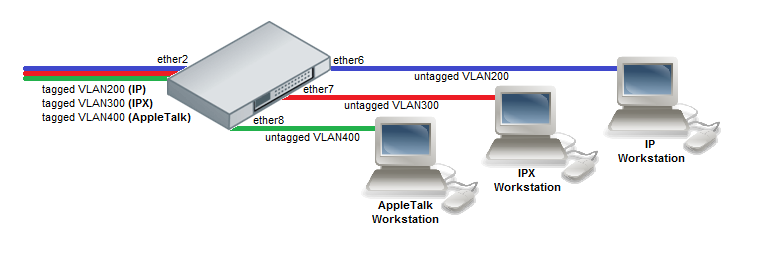
- Create a group of switched ports.
/interface ethernet set ether6 master-port=ether2 set ether7 master-port=ether2 set ether8 master-port=ether2
- Set VLAN for IP and ARP protocols
/interface ethernet switch protocol-based-vlan add port=ether2 protocol=arp set-customer-vid-for=all new-customer-vid=0 add port=ether6 protocol=arp set-customer-vid-for=all new-customer-vid=200 add port=ether2 protocol=ip set-customer-vid-for=all new-customer-vid=0 add port=ether6 protocol=ip set-customer-vid-for=all new-customer-vid=200
- Set VLAN for IPX protocol
/interface ethernet switch protocol-based-vlan add port=ether2 protocol=ipx set-customer-vid-for=all new-customer-vid=0 add port=ether7 protocol=ipx set-customer-vid-for=all new-customer-vid=300
- Set VLAN for AppleTalk AARP and AppleTalk DDP protocols
/interface ethernet switch protocol-based-vlan add port=ether2 protocol=0x80F3 set-customer-vid-for=all new-customer-vid=0 add port=ether8 protocol=0x80F3 set-customer-vid-for=all new-customer-vid=400 add port=ether2 protocol=0x809B set-customer-vid-for=all new-customer-vid=0 add port=ether8 protocol=0x809B set-customer-vid-for=all new-customer-vid=400
MAC Based VLAN
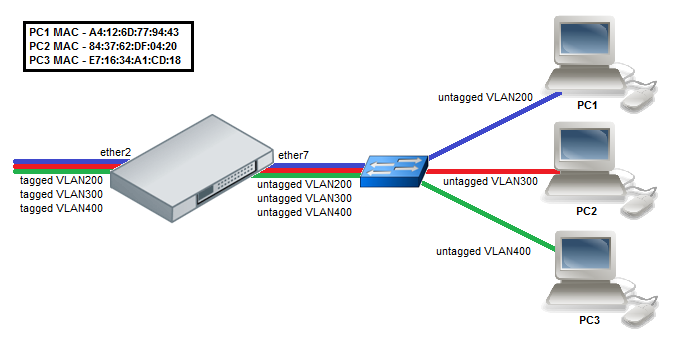
- Create a group of switched ports.
/interface ethernet set ether7 master-port=ether2
- Enable MAC based VLAN translation on access port.
/interface ethernet switch port set ether7 allow-fdb-based-vlan-translate=yes allow-mac-based-customer-vlan-assignment-for=tagged-frame-only
- Add MAC-to-VLAN mapping entries in MAC based VLAN table.
/interface ethernet switch mac-based-vlan add src-mac=A4:12:6D:77:94:43 new-customer-vid=200 add src-mac=84:37:62:DF:04:20 new-customer-vid=300 add src-mac=E7:16:34:A1:CD:18 new-customer-vid=400
- Set VLAN id untagging for tagged frames coming from the trunk port.
/interface ethernet switch ingress-vlan-translation add ports=ether2 customer-vlan-format=tagged new-customer-vid=0 sa-learning=yes
Management IP Configuration
- Management IP address has to be assigned to master-port.
/ip address add address=192.168.88.1/24 interface=ether2 network=192.168.88.0
- Or add VLAN 99 interface and assign IP address to it. Since the master-port receives all the traffic coming from switch-cpu port, VLAN has to be configured on master-port, in this case "ether2" port.
/interface vlan add name=vlan99 vlan-id=99 interface=ether2 /ip address add address=192.168.88.1/24 interface=vlan99 network=192.168.88.0
InterVLAN Routing
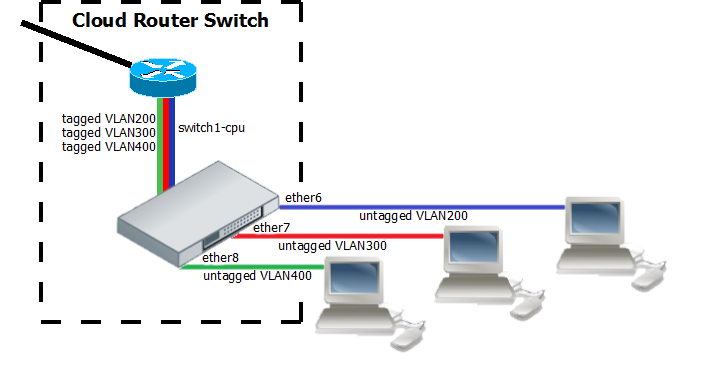
InterVLAN routing configuration consists of two main parts – VLAN tagging in switch-chip and routing in RouterOS. This configuration can be used in many applications by combining it with DHCP server, Hotspot, PPP and other features for each VLAN. Additionally this example covers blocking of unwanted other VLAN traffic on ports.
- Create a group of switched ports.
/interface ethernet set ether6 master-port=ether2 set ether7 master-port=ether2 set ether8 master-port=ether2
- Set VLAN tagging on CPU port for all VLANs to make packets tagged before they are routed and add ingress VLAN translation rules to ensure correct VLAN id assignment is done on access ports.
/interface ethernet switch egress-vlan-tag add tagged-ports=switch1-cpu vlan-id=200 add tagged-ports=switch1-cpu vlan-id=300 add tagged-ports=switch1-cpu vlan-id=400 /interface ethernet switch ingress-vlan-translation add ports=ether6 customer-vid=0 new-customer-vid=200 sa-learning=yes add ports=ether7 customer-vid=0 new-customer-vid=300 sa-learning=yes add ports=ether8 customer-vid=0 new-customer-vid=400 sa-learning=yes
- For routing add VLAN interfaces on master-port because it connects with CPU port and add IP addresses to created VLAN interfaces. In this example three 192.168.x.1 addresses are added to vlan200, vlan300 and vlan400 interfaces.
/interface vlan add name=vlan200 interface=ether2 vlan-id=200 add name=vlan300 interface=ether2 vlan-id=300 add name=vlan400 interface=ether2 vlan-id=400 /ip address add address=192.168.20.1/24 interface=vlan200 network=192.168.20.0 add address=192.168.30.1/24 interface=vlan300 network=192.168.30.0 add address=192.168.40.1/24 interface=vlan400 network=192.168.40.0
Unknown/Invalid VLAN filtering
VLAN membership is defined in the VLAN table. Adding entries with VLAN id and ports makes that VLAN traffic valid on those ports. After valid VLAN configuration unknown/invalid VLAN forwarding can be disabled in global switch settings. This VLAN filtering configuration example applies to InterVLAN Routing setup.
/interface ethernet switch vlan add ports=switch1-cpu,ether6 vlan-id=200 learn=yes add ports=switch1-cpu,ether7 vlan-id=300 learn=yes add ports=switch1-cpu,ether8 vlan-id=400 learn=yes /interface ethernet switch set forward-unknown-vlan=no
Mirroring
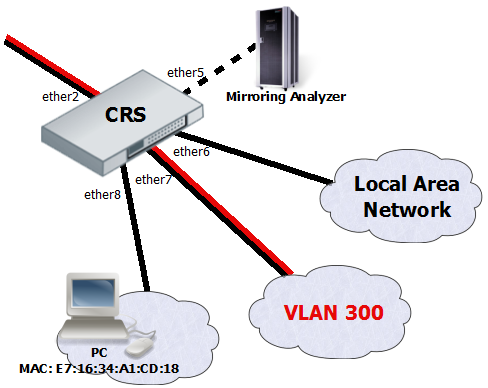
The Cloud Router Switches support three types of mirroring. Port based mirroring can be applied to any of switch-chip ports, VLAN based mirroring works for all specified VLANs regardless switch-chip ports and MAC based mirroring copies traffic sent or received from specific device reachable from the port configured in Unicast Forwarding Database.
Port Based Mirroring
The first configuration sets ether5 port as a mirror0 analyzer port for both ingress and egress mirroring, mirrored traffic will be sent to this port. Port based ingress and egress mirroring is enabled from ether7 port.
/interface ethernet switch set ingress-mirror0=ether8 egress-mirror0=ether8 /interface ethernet switch port set ether7 egress-mirror-to=mirror0 ingress-mirror-to=mirror0
VLAN Based Mirroring
The second example requires ports to be switched in a group. Mirroring configuration sets ether5 port as a mirror0 analyzer port and sets mirror0 port to be used when mirroring from VLAN occurs. VLAN table entry enables mirroring only for VLAN 300 traffic between ether2 and ether7 ports.
/interface ethernet set ether7 master-port=ether2 /interface ethernet switch set ingress-mirror0=ether5 vlan-uses=mirror0 /interface ethernet switch vlan add ports=ether2,ether7 vlan-id=300 learn=yes ingress-mirror=yes
MAC Based Mirroring
The third configuration also requires ports to be switched in a group. Mirroring configuration sets ether5 port as a mirror0 analyzer port and sets mirror0 port to be used when mirroring from Unicast Forwarding database occurs. The entry from Unicast Forwarding database enables mirroring for packets with source or destination MAC address E7:16:34:A1:CD:18 from ether8 port.
/interface ethernet set ether8 master-port=ether2 /interface ethernet switch set ingress-mirror0=ether5 fdb-uses=mirror0 /interface ethernet switch unicast-fdb add port=ether8 mirror=yes svl=yes mac-address=E7:16:34:A1:CD:18
Trunking
The Trunking in the Cloud Router Switches provides IEEE802.3ad and IEEE802.1ax compliant link aggregation with hardware automatic failover and load balancing. Up to 8 Trunk groups are supported with up to 8 Trunk member ports per Trunk group.
- Configuration requires a group of switched ports and an entry in the Trunk table.
/interface ethernet set ether6 master-port=ether2 set ether7 master-port=ether2 set ether8 master-port=ether2 /interface ethernet switch trunk add name=trunk1 member-ports=ether6,ether7,ether8
- This example also shows proper bonding configuration in RouterOS on the other end.
/interface bonding add name=bonding1 slaves=ether2,ether3,ether4 mode=802.3ad transmit-hash-policy=layer-2-and-3 \ lacp-rate=30secs link-monitoring=mii mii-interval=100ms
Port-level Isolation
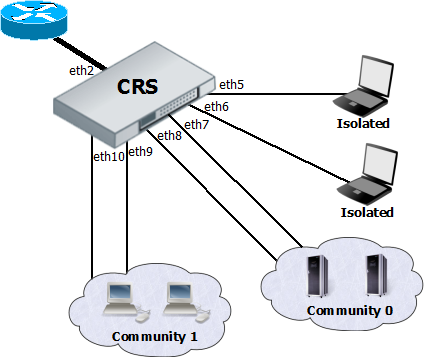
Port-level isolation is often used for Private VLAN, where:
- One or multiple uplink ports are shared among all users for accessing gateway or router.
- Port group Isolated Ports is for guest users. Communication is through the uplink ports only.
- Port group Community 0 is for department A. Communication is allowed between the group members and through uplink ports.
- Port group Community X is for department X. Communication is allowed between the group members and through uplink ports.
The Cloud Router Switches use port-level isolation profiles for Private VLAN implementation:
- Uplink ports – Port-level isolation profile 0
- Isolated ports – Port-level isolation profile 1
- Community 0 ports - Port-level isolation profile 2
- Community X (X <= 30) ports - Port-level isolation profile X
This example requires a group of switched ports. Assume that all ports used in this example are in one switch group configured with master-port setting.
The first part of port isolation configuration is setting the Uplink port – set port profile to 0 for ether2.
/interface ethernet switch port set ether2 isolation-leakage-profile-override=0
Then continue with setting isolation profile 1 to all isolated ports and adding the communication port for port isolation profile 1.
/interface ethernet switch port set ether5 isolation-leakage-profile-override=1 set ether6 isolation-leakage-profile-override=1 /interface ethernet switch port-isolation add port-profile=1 ports=ether2 type=dst
Configuration to set Community 0 and Community 1 ports is similar.
/interface ethernet switch port set ether7 isolation-leakage-profile-override=2 set ether8 isolation-leakage-profile-override=2 /interface ethernet switch port-isolation add port-profile=2 ports=ether2,ether7,ether8 type=dst
/interface ethernet switch port set ether9 isolation-leakage-profile-override=3 set ether10 isolation-leakage-profile-override=3 /interface ethernet switch port-isolation add port-profile=3 ports=ether2,ether9,ether10 type=dst
[ Top | Back to Content ]

