Manual:Interface/Dot1x: Difference between revisions
mNo edit summary |
|||
| Line 208: | Line 208: | ||
|type=time | |type=time | ||
|default=1m | |default=1m | ||
|desc= | |desc=Total time available for EAP authentication. | ||
}} | }} | ||
| Line 229: | Line 229: | ||
|type=time | |type=time | ||
|default=30s | |default=30s | ||
|desc= | |desc=Time interval between message retransmissions if no response is received from supplicant. | ||
}} | }} | ||
| Line 275: | Line 275: | ||
* <var>authorized</var> - access to interface is granted; | * <var>authorized</var> - access to interface is granted; | ||
* <var>iface-down</var> - interface is not running; | * <var>iface-down</var> - interface is not running; | ||
* <var>rejected-holding</var> | * <var>rejected-holding</var> - access was rejected by the RADIUS server; | ||
* <var>un-authorized</var> - access to interface is not granted. | * <var>un-authorized</var> - access to interface is not granted. | ||
}} | }} | ||
Revision as of 11:45, 8 May 2019
Summary
Sub-menu: /interface dot1x
Dot1x is implementation of IEEE 802.1X standard in RouterOS. Main purpose is to provide port-based network access control using EAP over LAN also known as EAPOL. 802.1X consists of a supplicant, an authenticator and an authentication server (RADIUS server). Currently both authenticator and supplicant sides are supported in RouterOS. Supported EAP methods for supplicant are EAP-TLS, EAP-TTLS, EAP-MSCHAPv2 and PEAPv0/EAP-MSCHAPv2.
Client
Properties
| Property | Description |
|---|---|
| anon-identity (string; Default: ) | Identity for outer layer EAP authentication. Used only with eap-ttls and eap-peap methods. If not set, value from identity parameter will be used for outer layer EAP authentication. |
| client-certificate (string; Default: ) | Name of a certificate listed in System/Certificates. Necessary when eap-tls method is used. |
| disabled (yes | no; Default: no) | Whether client is enabled or not. |
| eap-methods (eap-tls | eap-ttls | eap-peap | eap-mschapv2; Default: ) | Ordered list of EAP methods used for authentication. |
| identity (string; Default: ) | Supplicant identity used for EAP authentication. |
| interface (string; Default: ) | Name of the interface the client will run on. |
| password (string; Default: ) | Cleartext password for supplicant. |
Read only properties
| Property | Description |
|---|---|
| status (authenticated | authenticating | disabled) | Possible statuses:
|
Server
Properties
| Property | Description |
|---|---|
| disabled (yes | no; Default: no) | Whether server config is enabled or not. |
| interface (string; Default: ) | Name of the interface or interface list the server will run on. |
| profile (string; Default: default) | Name of the profile template that will be used by this instance. |
Active
Currently authenticated clients are listed in this menu.
Read only properties
| Property | Description |
|---|---|
| interface (string) | Name of the interface. |
| session-id (string) | Unique session identifier. |
| user-mac (mac-address) | MAC Address of the supplicant. |
| username (string) | Identity of the supplicant. |
| vlan (string) | Untagged VLAN ID that is assigned to the interface. VLAN ID filtering must be enabled on bridge. |
Profile
Properties
| Property | Description |
|---|---|
| accounting (yes | no; Default: yes) | Whether to send RADIUS accounting requests to authentication server. |
| auth-timeout (time; Default: 1m) | Total time available for EAP authentication. |
| interim-update (time; Default: 0s) | Interval between scheduled RADIUS Interim-Update messages. |
| name (string; Default: ) | Name of the profile. |
| retrans-timeout (time; Default: 30s) | Time interval between message retransmissions if no response is received from supplicant. |
Read only properties
| Property | Description |
|---|---|
| default (yes | no) | Whether this is a default system entry. |
| default-name (string) | Default profile name in case it has changed. |
State
Statuses of all active dot1x server interfaces are listed in this menu.
Read only properties
| Property | Description |
|---|---|
| interface (string) | Name of the interface. |
| status (string) | Possible interface statuses:
|
Application Example
RouterOS Authenticator configuration
Start off by adding a new RADIUS client. The authentication server (RADIUS) does not necessary have to be in the same LAN as authenticator, but it must be reachable from the authenticator, so any firewall limitations must be considered.
/radius add address=10.1.2.3 secret=radiussecret service=dot1x

Note: if RADIUS communication is done over public network, it is advised to use RadSec for RADIUS communication. More information: RADIUS Client
Add new dot1x server profiles if necessary and server instances.
/interface dot1x server profile add name=accounted interim-update=30s add name=notaccounted accounting=no
/interface dot1x server add interface=ether2 profile=accounted add interface=ether12 profile=notaccounted
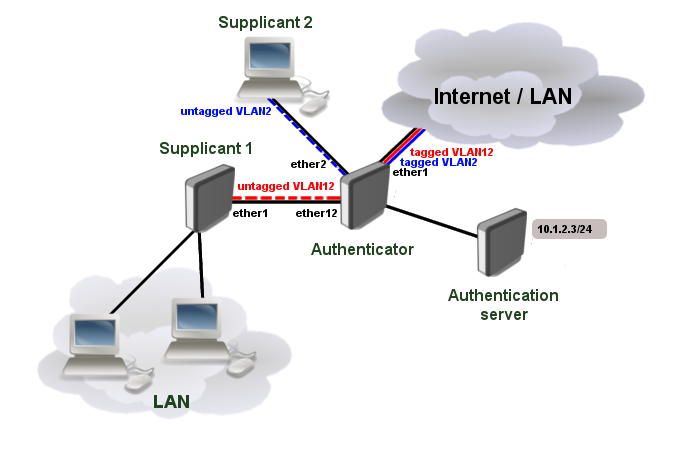
Port based VLAN ID assignment
It is possible to assign an authenticated interface to a specific VLAN ID using bridge VLAN filtering. This can be done using RADIUS Tunnel-Type, Tunnel-Medium-Type and Tunnel-Private-Group-ID attributes. Note that only devices with hardware offloaded VLAN filtering will be able to do this in switch chip. See Bridge Hardware Offloading.
First of all, make sure the interface is added to a bridge which has VLAN filtering enabled.
/interface bridge add name=bridge1 vlan-filtering=yes /interface bridge port add bridge=bridge1 interface=ether1 add bridge=bridge1 interface=ether2 add bridge=bridge1 interface=ether12
It is necessary to add static VLAN configuration for tagged VLAN traffic to be sent over ether1 interface.
/interface bridge vlan add bridge=bridge1 tagged=ether1 vlan-ids=2 add bridge=bridge1 tagged=ether1 vlan-ids=12
With enabled RADIUS debug logs it is possible to see complete RADIUS message packets with all attributes. In our example, Tunnel attributes are received in Access-Accept message from RADIUS server:
09:51:45 radius,debug,packet received Access-Accept with id 64 from 10.1.2.3:1812 09:51:45 radius,debug,packet Tunnel-Type = 13 09:51:45 radius,debug,packet Tunnel-Medium-Type = 6 09:51:45 radius,debug,packet Tunnel-Private-Group-ID = "12" (..) 09:51:45 radius,debug,packet User-Name = "dot1x-user"
The VLAN ID is now present in active session list and untagged ports are added to previously created static VLAN configuration.
/interface dot1x server active print 0 interface=ether12 username="dot1x-user" user-mac=00:0C:42:EB:71:F6 session-id="86b00006" vlan=12
/interface bridge vlan print detail Flags: X - disabled, D - dynamic 0 D bridge=bridge1 vlan-ids=1 tagged="" untagged="" current-tagged="" current-untagged=bridge1,ether3 1 bridge=bridge1 vlan-ids=2 tagged=ether1 untagged="" current-tagged=ether1 current-untagged=ether2 2 bridge=bridge1 vlan-ids=12 tagged=ether1 untagged="" current-tagged=ether1 current-untagged=ether12
RouterOS Supplicant configuration
CA certificates are required for eap-tls, eap-ttls and eap-peap authentication methods. Additionally a client certificate is required for eap-tls method. For this example we have already imported a P12 certificate bundle with self signed client and CA certificates. For more information how to import certificates in RouterOS, please visit System/Certificates.
/certificate print Flags: K - private-key, L - crl, C - smart-card-key, A - authority, I - issued, R - revoked, E - expired, T - trusted # NAME COMMON-NAME SUBJECT-ALT-NAME FINGERPRINT 0 K A T dot1x-client ez_dot1x-client IP:10.1.2.34 1 L A T dot1x CA ca
Simply add a new dot1x client instance that will initiate authentication process.
/interface dot1x client add anon-identity=anonymous client-certificate=dot1x-client eap-methods=eap-tls identity=dot1x-user interface=ether1 password=dot1xtest
If authentication was successful, the interface should have status authenticated.
/interface dot1x client print Flags: I - inactive, X - disabled 0 interface=ether1 eap-methods=eap-peap identity="dot1x-user" password="dot1xtest" anon-identity="anonymous" client-certificate=dot1x-client status="authenticated"
[ Top | Back to Content ]