Manual:Load balancing multiple same subnet links: Difference between revisions
mNo edit summary |
No edit summary |
||
| Line 12: | Line 12: | ||
Provider is giving us two links with IP addresses from the same network range (10.1.101.10/24 and 10.1.101.18/24). Gateway for both of these links is the same 10.1.101.1 | Provider is giving us two links with IP addresses from the same network range (10.1.101.10/24 and 10.1.101.18/24). Gateway for both of these links is the same 10.1.101.1 | ||
<h3>Configuration</h3> | <h3>Configuration Example 1</h3> | ||
Here is the whole configuration for those who want to copy&paste | Here is the whole configuration for those who want to copy&paste | ||
| Line 40: | Line 40: | ||
<h4>IP address</h4> | <h4>IP address</h4> | ||
In previous RouterOS version multiple IP addresses from the same subnet on different interfaces were not allowed. Fortunately v4 allows such configurations. | In previous RouterOS version, multiple IP addresses from the same subnet on different interfaces were not allowed. Fortunately, from v4 RouterOS allows such configurations. | ||
In this example our provider assigned two upstream links, one connected to <b>ether1</b> and other to <b>ether2</b>. Our local network has two subnets 192.168.1.0/24 and 192.168.2.0/24 | In this example our provider assigned two upstream links, one connected to <b>ether1</b> and other to <b>ether2</b>. Our local network has two subnets 192.168.1.0/24 and 192.168.2.0/24 | ||
| Line 57: | Line 57: | ||
gateway-status=ether1 reachable,ether2 reachable distance=0 scope=10 | gateway-status=ether1 reachable,ether2 reachable distance=0 scope=10 | ||
</pre> | </pre> | ||
<h4>Mangle and NAT</h4> | <h4>Mangle and NAT</h4> | ||
| Line 105: | Line 103: | ||
</pre> | </pre> | ||
Finally, we have one additional entry specifying that traffic from the router itself (the traffic without any routing marks) will be resolved in main routing table. | Finally, we have one additional entry specifying that traffic from the router itself (the traffic without any routing marks) will be resolved in the main routing table. | ||
<pre> | <pre> | ||
/ip route | /ip route | ||
| Line 111: | Line 109: | ||
</pre> | </pre> | ||
</div> | </div> | ||
<h3>Configuration Example 2</h3> | |||
[[File:Dual-wan.png|300px|]] | |||
<h4>IP address</h4> | |||
In this example our provider assigned two upstream links, one connected to <b>ether1</b> and other to <b>ether2</b>. Our local network has two subnets 192.168.1.0/24 and 192.168.2.0/24 | |||
<pre> | |||
/ip address | |||
add address=10.1.101.18/24 interface=ether1 | |||
add address=10.1.200.18/24 interface=ether2 | |||
add address=192.168.1.1/24 interface=Local | |||
add address=192.168.2.1/24 interface=Local | |||
</pre> | |||
<h4>Mangle and NAT</h4> | |||
In this example connections going through the ehter1 interface is marked as <b>"first"</b> and packets going through the ether2 is marked as <b>"other"</b>. | |||
<pre> | |||
/ip firewall mangle | |||
add action=mark-connection chain=forward connection-mark=no-mark new-connection-mark=first out-interface=ether1 passthrough=yes | |||
add action=mark-connection chain=forward connection-mark=no-mark new-connection-mark=other out-interface=ether2 passthrough=yes | |||
</pre> | |||
Instead of masquerade, we will use src-nat for our local networks, because we do not want to purge connections which is one of masquarades main features when a primary link fails. We will restrict them with a firewall rules (later in this example) | |||
<pre> | |||
/ip firewall nat | |||
add action=src-nat chain=srcnat out-interface=ether1 to-address=10.1.101.18/24 | |||
add action=src-nat chain=srcnat out-interface=ether2 to-address=10.1.200.18/24 | |||
</pre> | |||
When the primary link will fail, we will reject all the established connections, so a new connections will pass through the secondary link. The same behavior will happen when a primary link will come back again and here we will prevent local IP leakage to a public network, which is one of <span class="plainlinks">[https://wiki.mikrotik.com/wiki/Manual:IP/Firewall/NAT#Masquerade masquerades disadvantages]</span>. | |||
<pre> | |||
add action=reject chain=forward connection-mark=other out-interface=ether1 reject-with=icmp-network-unreachable | |||
add action=reject chain=forward connection-mark=first out-interface=ether2 reject-with=icmp-network-unreachable | |||
</pre> | |||
<h4>Routes</h4> | |||
We will add two default routes. With <code>distance</code> parameter we set routes preference: | |||
<pre> | |||
/ip route add gateway=10.1.101.1 distance=1 check-gateway=ping | |||
/ip route add gateway=10.1.200.1 distance=2 | |||
</pre> | |||
[[Category:Unfinished]] | [[Category:Unfinished]] | ||
Revision as of 09:01, 24 July 2019
Summary
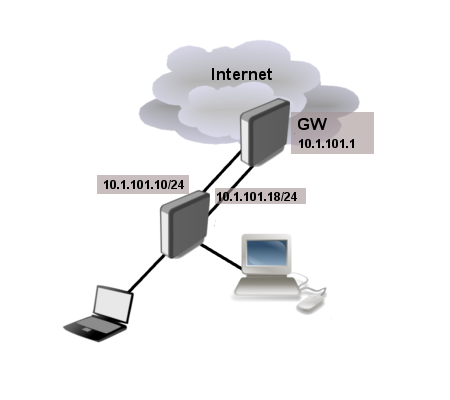
This example demonstrates how to set up load balancing if provider is giving IP addresses from the same subnet for all links.
Application Example
Provider is giving us two links with IP addresses from the same network range (10.1.101.10/24 and 10.1.101.18/24). Gateway for both of these links is the same 10.1.101.1
Configuration Example 1
Here is the whole configuration for those who want to copy&paste
/ip address add address=10.1.101.18/24 interface=ether1 add address=10.1.101.10/24 interface=ether2 add address=192.168.1.1/24 interface=Local add address=192.168.2.1/24 interface=Local /ip route add gateway=10.1.101.1 add gateway=10.1.101.1%ether1 routing-mark=first add gateway=10.1.101.1%ether2 routing-mark=other /ip firewall nat add action=masquerade chain=srcnat out-interface=ether1 add action=masquerade chain=srcnat out-interface=ether2 /ip firewall mangle add action=mark-routing chain=prerouting src-address=192.168.1.0/24 new-routing-mark=first add action=mark-routing chain=prerouting src-address=192.168.2.0/24 new-routing-mark=other
IP address
In previous RouterOS version, multiple IP addresses from the same subnet on different interfaces were not allowed. Fortunately, from v4 RouterOS allows such configurations.
In this example our provider assigned two upstream links, one connected to ether1 and other to ether2. Our local network has two subnets 192.168.1.0/24 and 192.168.2.0/24
/ip address add address=10.1.101.18/24 interface=ether1 add address=10.1.101.10/24 interface=ether2 add address=192.168.1.1/24 interface=Local add address=192.168.2.1/24 interface=Local
After IP address is set up, connected route will be installed as ECMP route
[admin@MikroTik] /ip route> print detail
0 ADC dst-address=10.1.101.0/24 pref-src=10.1.101.18 gateway=ether1,ether2
gateway-status=ether1 reachable,ether2 reachable distance=0 scope=10
Mangle and NAT
In our example very simple policy routing is used. Clients from 192.168.1.0/24 subnet is marked to use "first" routing table and 192.168.2.0/24 to use "other" subnet.

Note: The same can be achieved by setting up route rules instead of mangle.
/ip firewall mangle add action=mark-routing chain=prerouting src-address=192.168.1.0/24 new-routing-mark=first add action=mark-routing chain=prerouting src-address=192.168.2.0/24 new-routing-mark=other
And masquerade our local networks
/ip firewall nat add action=masquerade chain=srcnat out-interface=ether1 add action=masquerade chain=srcnat out-interface=ether2

Warning: You will also have to deal with traffic coming to and from the router itself. For explanations look at PCC configuration example.
IP route
We are adding two gateways, one to resolve in "first" routing table and another to "other" routing table.
/ip route add gateway=10.1.101.1%ether1 routing-mark=first add gateway=10.1.101.1%ether2 routing-mark=other
Interesting part of these routes is how we set gateway. gateway=10.1.101.1%ether1 means that gateway 10.1.101.1 will be explicitly reachable over ether1
[admin@MikroTik] /ip route> print detail
Flags: X - disabled, A - active, D - dynamic,
C - connect, S - static, r - rip, b - bgp, o - ospf, m - mme,
B - blackhole, U - unreachable, P - prohibit
0 A S dst-address=0.0.0.0/0 gateway=10.1.101.1%ether2
gateway-status=10.1.101.1 reachable ether2 distance=1 scope=30
target-scope=10 routing-mark=other
1 A S dst-address=0.0.0.0/0 gateway=10.1.101.1%ether1
gateway-status=10.1.101.1 reachable ether1 distance=1 scope=30
target-scope=10 routing-mark=first
Finally, we have one additional entry specifying that traffic from the router itself (the traffic without any routing marks) will be resolved in the main routing table.
/ip route add gateway=10.1.101.1
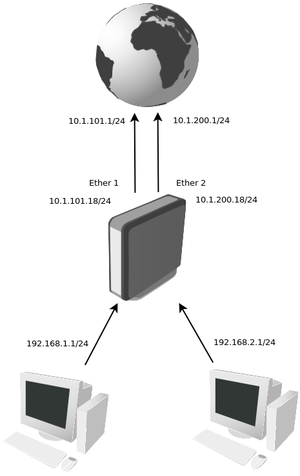
Configuration Example 2
IP address
In this example our provider assigned two upstream links, one connected to ether1 and other to ether2. Our local network has two subnets 192.168.1.0/24 and 192.168.2.0/24
/ip address add address=10.1.101.18/24 interface=ether1 add address=10.1.200.18/24 interface=ether2 add address=192.168.1.1/24 interface=Local add address=192.168.2.1/24 interface=Local
Mangle and NAT
In this example connections going through the ehter1 interface is marked as "first" and packets going through the ether2 is marked as "other".
/ip firewall mangle add action=mark-connection chain=forward connection-mark=no-mark new-connection-mark=first out-interface=ether1 passthrough=yes add action=mark-connection chain=forward connection-mark=no-mark new-connection-mark=other out-interface=ether2 passthrough=yes
Instead of masquerade, we will use src-nat for our local networks, because we do not want to purge connections which is one of masquarades main features when a primary link fails. We will restrict them with a firewall rules (later in this example)
/ip firewall nat add action=src-nat chain=srcnat out-interface=ether1 to-address=10.1.101.18/24 add action=src-nat chain=srcnat out-interface=ether2 to-address=10.1.200.18/24
When the primary link will fail, we will reject all the established connections, so a new connections will pass through the secondary link. The same behavior will happen when a primary link will come back again and here we will prevent local IP leakage to a public network, which is one of masquerades disadvantages.
add action=reject chain=forward connection-mark=other out-interface=ether1 reject-with=icmp-network-unreachable add action=reject chain=forward connection-mark=first out-interface=ether2 reject-with=icmp-network-unreachable
Routes
We will add two default routes. With distance parameter we set routes preference:
/ip route add gateway=10.1.101.1 distance=1 check-gateway=ping /ip route add gateway=10.1.200.1 distance=2