Manual:Interface/Bridge
Summary
Sub-menu: /interface bridge
Standards: IEEE802.1D
Ethernet-like networks (Ethernet, Ethernet over IP, IEEE802.11 in ap-bridge or bridge mode, WDS, VLAN) can be connected together using MAC bridges. The bridge feature allows the interconnection of hosts connected to separate LANs (using EoIP, geographically distributed networks can be bridged as well if any kind of IP network interconnection exists between them) as if they were attached to a single LAN. As bridges are transparent, they do not appear in traceroute list, and no utility can make a distinction between a host working in one LAN and a host working in another LAN if these LANs are bridged (depending on the way the LANs are interconnected, latency and data rate between hosts may vary).
Network loops may emerge (intentionally or not) in complex topologies. Without any special treatment, loops would prevent network from functioning normally, as they would lead to avalanche-like packet multiplication. Each bridge runs an algorithm which calculates how the loop can be prevented. STP and RSTP allows bridges to communicate with each other, so they can negotiate a loop free topology. All other alternative connections that would otherwise form loops, are put to standby, so that should the main connection fail, another connection could take its place. This algorithm exchanges configuration messages (BPDU - Bridge Protocol Data Unit) periodically, so that all bridges are updated with the newest information about changes in network topology. (R)STP selects a root bridge which is responsible for network reconfiguration, such as blocking and opening ports on other bridges. The root bridge is the bridge with the lowest bridge ID.
Bridge Interface Setup
Sub-menu: /interface bridge
To combine a number of networks into one bridge, a bridge interface should be created (later, all the desired interfaces should be set up as its ports). One MAC address will be assigned to all the bridged interfaces (the MAC address of first bridge port which comes up will be chosen automatically).
Properties
| Property | Description |
|---|---|
| admin-mac (MAC address; Default: ) | Static MAC address of the bridge (takes effect if auto-mac=no) |
| ageing-time (time; Default: 00:05:00) | How long a host's information will be kept in the bridge database |
| arp (disabled | enabled | proxy-arp | reply-only; Default: enabled) | Address Resolution Protocol setting
|
| auto-mac (yes | no; Default: yes) | Automatically select one MAC address of bridge ports as a bridge MAC address |
| fast-forward (yes | no; Default: yes) | Special and faster case of Fast Path which works only on bridges with 2 interfaces (enabled by default only for new bridges) |
| forward-delay (time; Default: 00:00:15) | Time which is spent during the initialization phase of the bridge interface (i.e., after router startup or enabling the interface) in listening/learning state before the bridge will start functioning normally |
| l2mtu (integer; read-only) | Layer2 Maximum transmission unit. read more» |
| max-message-age (time; Default: 00:00:20) | How long to remember Hello messages received from other bridges |
| mtu (integer; Default: 1500) | Maximum Transmission Unit |
| name (text; Default: bridgeN) | Name of the bridge interface |
| priority (integer: 0..65535 decimal format or 0x0000-0xffff hex format; Default: 32768 / 0x8000) |
Spanning tree protocol priority for bridge interface. Bridge with the smallest (lowest) bridge ID becomes a Root-Bridge. Bridge ID consists of two numbers - priority and MAC address of the bridge. To compare two bridge IDs, the priority is compared first. If two bridges have equal priority, then the MAC addresses are compared. |
| protocol-mode (none | rstp | stp; Default: rstp) | Select Spanning tree protocol (STP) or Rapid spanning tree protocol (RSTP) to ensure a loop-free topology for any bridged LAN. RSTP provides for faster spanning tree convergence after a topology change. |
| transmit-hold-count (integer: 1..10; Default: 6) | The Transmit Hold Count used by the Port Transmit state machine to limit transmission rate |
Example
To add and enable a bridge interface that will forward all the protocols:
[admin@MikroTik] /interface bridge> add
[admin@MikroTik] /interface bridge> print
Flags: X - disabled, R - running
0 R name="bridge1" mtu=1500 l2mtu=65535 arp=enabled
mac-address=00:00:00:00:00:00 protocol-mode=none priority=0x8000
auto-mac=yes admin-mac=00:00:00:00:00:00 max-message-age=20s
forward-delay=15s transmit-hold-count=6 ageing-time=5m
[admin@MikroTik] /interface bridge>
Spanning Tree Protocol
RouterOS is capable of running bridge interfaces with (R/M)STP support in order to create loop-free and Layer2 redundant environment. It is always recommended to manually set up each bridge priority, port priority and port path cost to ensure proper Layer2 functionality at all times. Leaving STP related values to defaults are acceptable for a network that consists of of 1 to 2 bridges running with (R/M)STP enabled, but it is highly recommended to manually set these values for larger networks. Since STP elects a root bridge and root ports by checking STP related values from bridges over the network, then leaving STP setting to automatic may elect a undesired root bridge and root ports and in case of a hardware failure can result in an inaccessible network.
You can check the STP status of a bridge by using the /interface bridge monitor command, for example:
/interface bridge monitor bridge
state: enabled
current-mac-address: 64:D1:54:D9:27:E6
root-bridge: yes
root-bridge-id: 0x3E8.64:D1:54:D9:27:E6
root-path-cost: 0
root-port: none
port-count: 5
designated-port-count: 5
You can check the STP status of a bridge port by using the /interface bridge port monitor command, for example:
/interface bridge port monitor 2
interface: ether3
status: in-bridge
port-number: 3
role: root-port
edge-port: no
edge-port-discovery: yes
point-to-point-port: yes
external-fdb: no
sending-rstp: yes
learning: yes
forwarding: yes
root-path-cost: 10
designated-bridge: 0x3E8.64:D1:54:D9:27:E6
designated-cost: 0
designated-port-number: 4
hw-offload-group: switch1
Note that root-bridge-id consists of the bridge priority and the bridge's MAC address, for non-root bridges the root bridge will be shown as designated-bridge. One port can have one role in a STP enabled network, here are the possible roles:
- root-port - port that is facing towards the root bridge and will be used to forward traffic from/to the root bridge (Forwarding mode).
- alternate-port - port that is facing towards root bridge, but is not going to forward traffic (Discarding/Blocking mode).
- designated-port - port that is facing away from the root bridge, but is going to forward traffic (Forwarding mode).
- disabled-port - disabled or inactive port (Discarding/Blocking mode).
Election process
To properly configure STP in your network you need to understand the election process and which parameters are involved in which order. In RouterOS the root bridge will be elected based on the smallest priority and the smallest MAC address in this particular order:
- Bridge priority (lowest)
- Bridge MAC address (lowest)
In RouterOS root ports are elected based on lowest port path cost, lowest port priority and lowest bridge port ID in this particular order:
- Port path cost (lowest)
- Port priority (lowest)
- Bridge port ID (lowest)
The following parameters are used to manipulate with the STP root bridge and root port election process:
Sub-menu: /interface bridge
| Property | Description |
|---|---|
| priority (integer: 0..65535 decimal format or 0x0000-0xffff hex format; Default: 32768 / 0x8000) |
Spanning tree protocol priority for bridge interface. Bridge with the smallest (lowest) bridge ID becomes a Root-Bridge. Bridge ID consists of two numbers - priority and MAC address of the bridge. To compare two bridge IDs, the priority is compared first. If two bridges have equal priority, then the MAC addresses are compared. |
Sub-menu: /interface bridge port
| Property | Description |
|---|---|
| path-cost (integer: 0..65535; Default: 10) | Path cost to the interface, used by STP to determine the "best" path |
| priority (integer: 0..240; Default: 128) (i=dec*16 dec={0..15}) (i=hex*0x10 hex={0x0..0xF}) | The priority of the interface in comparison with other going to the same subnet |

Note: Make sure you are using path cost and priority on the right ports. For example, setting path cost on a ports that are in a root bridge has no effect, only port priority has effect on them. Path cost has effect on ports that are facing towards the root bridge and port priority has effect on ports that are facing away from the root bridge.

Note: When electing a root port the path cost will be checked first. If the path cost for multiple paths is the same, then port priority is checked. If port priority is the same, then bridge port ID is checked, port with the lowest values will be elected as a root bridge. Make sure you take into account the election process when designing your network with STP enabled.
http://en.wikipedia.org/wiki/Spanning_Tree_Protocol
Bridge Settings
Sub-menu: /interface bridge settings
| Property | Description |
|---|---|
| use-ip-firewall (yes | no; Default: no) | Force bridged traffic to also be processed by prerouting, forward and postrouting sections of IP routing (http://wiki.mikrotik.com/wiki/Manual:Packet_Flow_v6). This does not apply to routed traffic. |
| use-ip-firewall-for-pppoe (yes | no; Default: no) | Send bridged un-encrypted PPPoE traffic to also be processed by 'IP firewall' (requires use-ip-firewall=yes to work) |
| use-ip-firewall-for-vlan (yes | no; Default: no) | Send bridged VLAN traffic to also be processed by 'IP firewall' (requires use-ip-firewall=yes to work) |
| allow-fast-path (yes | no; Default: yes) | Allows fast path |
| bridge-fast-path-active (yes | no; Default: ) | Shows whether Bridge Fast Path is active |
| bridge-fast-path-packets (integer; Default: ) | Shows packet count forwarded by Bridge Fast Path |
| bridge-fast-path-bytes (integer; Default: ) | Shows byte count forwarded by Bridge Fast Path |
| bridge-fast-forward-packets (integer; Default: ) | Shows packet count forwarded by Bridge Fast Forward |
| bridge-fast-forward-bytes (integer; Default: ) | Shows byte count forwarded by Bridge Fast Forward |
Port Settings
Sub-menu: /interface bridge port
Port submenu is used to enslave interfaces in a particular bridge interface.
| Property | Description |
|---|---|
| auto-isolate (yes | no; Default:no) | Prevents STP blocking port from erroneously moving into a forwarding state if no BPDU's are received on the bridge. |
| bridge (name; Default: none) | The bridge interface the respective interface is grouped in |
| edge (auto | no | no-discover | yes | yes-discover; Default: auto) | Set port as edge port or non-edge port, or enable automatic detection. Edge ports are connected to a LAN that has no other bridges attached. If the port is configured to discover edge port then as soon as the bridge detects a BPDU coming to an edge port, the port becomes a non-edge port. |
| external-fdb (auto | no | yes; Default: auto) | Whether to use wireless registration table to speed up bridge host learning |
| horizon (none | integer 0..429496729; Default: none) | Use split horizon bridging to prevent bridging loops. read more» |
| interface (name; Default: none) | Name of the interface |
| path-cost (integer: 0..65535; Default: 10) | Path cost to the interface, used by STP to determine the "best" path |
| point-to-point (auto | yes | no; Default: auto) | |
| priority (integer: 0..240; Default: 128) (i=dec*16 dec={0..15}) (i=hex*0x10 hex={0x0..0xF}) | The priority of the interface in comparison with other going to the same subnet |
Example
To group ether1 and ether2 in the already created bridge1 bridge
[admin@MikroTik] /interface bridge port> add bridge=bridge1 interface=ether1 [admin@MikroTik] /interface bridge port> add bridge=bridge1 interface=ether2 [admin@MikroTik] /interface bridge port> print Flags: X - disabled, I - inactive, D - dynamic # INTERFACE BRIDGE PRIORITY PATH-COST HORIZON 0 ether1 bridge1 0x80 10 none 1 ether2 bridge1 0x80 10 none [admin@MikroTik] /interface bridge port>
Bridge Monitoring
Sub-menu: /interface bridge monitor
Used to monitor the current status of a bridge.
| Property | Description |
|---|---|
| current-mac-address (MAC address) | Current MAC address of the bridge |
| designated-port-count (integer) | Number of designated bridge ports |
| port-count (integer) | Number of the bridge ports |
| root-bridge (yes | no) | Shows whether bridge is the root bridge of the spanning tree |
| root-bridge-id (text) | The root bridge ID, which is in form of bridge-priority.bridge-MAC-address |
| root-path-cost (integer) | The total cost of the path to the root-bridge |
| root-port (name) | Port to which the root bridge is connected to |
| state (enabled | disabled) | State of the bridge |
Example
To monitor a bridge:
[admin@MikroTik] /interface bridge> monitor bridge1
state: enabled
current-mac-address: 00:0C:42:52:2E:CE
root-bridge: yes
root-bridge-id: 0x8000.00:00:00:00:00:00
root-path-cost: 0
root-port: none
port-count: 2
designated-port-count: 0
[admin@MikroTik] /interface bridge>
Bridge Port Monitoring
Sub-menu: /interface bridge port monitor
Statistics of an interface that belongs to a bridge.
| Property | Description |
|---|---|
| edge-port (yes | no) | Whether port is an edge port or not |
| edge-port-discovery (yes | no) | Whether port is set to automatically detect edge ports |
| external-fdb (yes | no) | Shows whether registration table is used instead of forwarding data base |
| forwarding (yes | no) | Port state |
| learning (yes | no) | Port state |
| port-number (integer 1..4095) | Port identifier |
| point-to-point-port (yes | no) | |
| role (designated | root port | alternate | backup | disabled) |
(R)STP algorithm assigned role of the port:
|
| sending-rstp (yes | no) | Whether the port is sending BPDU messages |
| status (in-bridge | inactive) | Port status |
Example
To monitor a bridge port:
[admin@MikroTik] /interface bridge port> monitor 0
status: in-bridge
port-number: 1
role: designated-port
edge-port: no
edge-port-discovery: yes
point-to-point-port: no
external-fdb: no
sending-rstp: no
learning: yes
forwarding: yes
[admin@MikroTik] /interface bridge port>
Bridge Host Monitoring
Sub-menu: /interface bridge host
| Property | Description |
|---|---|
| age (read-only: time) | The time since the last packet was received from the host |
| bridge (read-only: name) | The bridge the entry belongs to |
| external-fdb (read-only: flag) | Whether the host was learned using wireless registration table |
| local (read-only: flag) | Whether the host entry is of the bridge itself (that way all local interfaces are shown) |
| mac-address (read-only: MAC address) | Host's MAC address |
| on-interface (read-only: name) | Which of the bridged interfaces the host is connected to |
Example
To get the active host table:
[admin@MikroTik] /interface bridge host> print Flags: L - local, E - external-fdb BRIDGE MAC-ADDRESS ON-INTERFACE AGE bridge1 00:00:00:00:00:01 ether2 3s bridge1 00:01:29:FF:1D:CC ether2 0s L bridge1 00:0C:42:52:2E:CF ether2 0s bridge1 00:0C:42:52:2E:D0 ether2 3s bridge1 00:0C:42:5C:A5:AE ether2 0s [admin@MikroTik] /interface bridge host>
Bridge VLAN Filtering
Bridge VLAN Filtering since RouterOS v6.40rc29 provides VLAN aware Layer2 forwarding and VLAN tag modifications within the bridge. This set of features makes bridge operation more like a traditional Ethernet switch and allows to overcome Spanning Tree compatibilty issues compared to configuration when tunnel-like VLAN interfaces are bridged. Bridge VLAN Filtering configuration is highly recommended to comply with STP (802.1D), RSTP (802.1w) standards and is mandatory to enable MSTP (802.1s) support in RouterOS.
Sub-menu: /interface bridge
The main VLAN setting is vlan-filtering which globally controls vlan-awareness and VLAN tag processing in the bridge.
If vlan-filtering=no, bridge ignores VLAN tags, works in a shared-VLAN-learning (SVL) mode and cannot modify VLAN tags of packets.
Turning on vlan-filtering enables all bridge VLAN related functionality and independent-VLAN-learning (IVL) mode.
Besides joining the ports for Layer2 forwarding, bridge itself is also an interface therefore it has Port VLAN ID (pvid).
| Property | Description |
|---|---|
| vlan-filtering (yes | no; Default:no) | Globally enables or disables VLAN functionality for bridge. |
| pvid (1..4094; Default:1) | Port VLAN ID (pvid) specifies which VLAN the untagged ingress traffic is assigned to. It applies e.g. to frames sent from bridge IP and destined to a bridge port. |
Sub-menu: /interface bridge port
The bridge port settings related to vlan filtering are described below.
| Property | Description |
|---|---|
| frame-types (admit-all | admit-only-untagged-and-priority-tagged | admit-only-vlan-tagged; Default:admit-all) | Specifies allowed ingress frame types on a bridge port. |
| ingress-filtering (yes | no; Default:no) | Enables or disables filtering which looks for an ingress port match in the Bridge VLAN table. |
| pvid (1..4094; Default:1) | Port VLAN ID (pvid) specifies which VLAN the untagged ingress traffic is assigned to. |
Sub-menu: /interface bridge vlan
Bridge VLAN table represents per-VLAN port mapping with an egress VLAN tag action.
tagged ports send out frames with a learned VLAN ID tag.
untagged ports remove VLAN tag before sending out frames if the learned VLAN ID matches the port pvid.
| Property | Description |
|---|---|
| bridge (name) | The bridge interface which the respective VLAN entry is intended for. |
| disabled (yes | no; Default:no) | Enables or disables Bridge VLAN entry. |
| tagged (interfaces; Default:none) | Interface list with a VLAN tag adding action in egress. This setting accepts comma separated values. E.g. tagged=ether1,ether2. |
| untagged (interfaces; Default:none) | Interface list with a VLAN tag removing action in egress. This setting accepts comma separated values. E.g. tagged=ether3,ether4. |
| vlan-ids (1..4094) | The list of VLAN IDs for certain port configuration. This setting accepts VLAN ID range as well as comma separated values. E.g. vlan-ids=100-115,120,122,128-130. |
Sub-menu: /interface bridge host
Bridge Host table allows monitoring learned MAC addresses and when vlan-filtering is enabled shows learned VLAN ID as well.
[admin@MikroTik] > interface bridge host print where !local Flags: L - local, E - external-fdb BRIDGE VID MAC-ADDRESS ON-INTERFACE AGE bridge1 200 D4:CA:6D:77:2E:F0 ether3 7s bridge1 200 E4:8D:8C:1B:05:F0 ether2 2s bridge1 300 D4:CA:6D:74:65:9D ether4 3s bridge1 300 E4:8D:8C:1B:05:F0 ether2 2s bridge1 400 4C:5E:0C:4B:89:5C ether5 0s bridge1 400 E4:8D:8C:1B:05:F0 ether2 0s [admin@MikroTik] >

Note: Make sure you have added all needed interfaces to the bridge VLAN table when using bridge VLAN filtering. For routing functions to work properly on the same device through ports that use bridge VLAN filtering, you will need to allow access to the CPU from those ports, this can be done by adding the bridge interface itself to the VLAN table, for tagged traffic you will need to add the bridge interface as a tagged port and create a VLAN interface on the bridge interface. Examples can be found at the Management port section.

Warning: When allowing access to the CPU, you are allowing access from a certain port to the actual router/switch, this is not always desirable. Make sure you implement proper firewall filter rules to secure your device when access to the CPU is allowed from a certain VLAN ID and port, use firewall filter rules to allow access to only certain services.
VLAN Example #1 (Trunk and Access Ports)
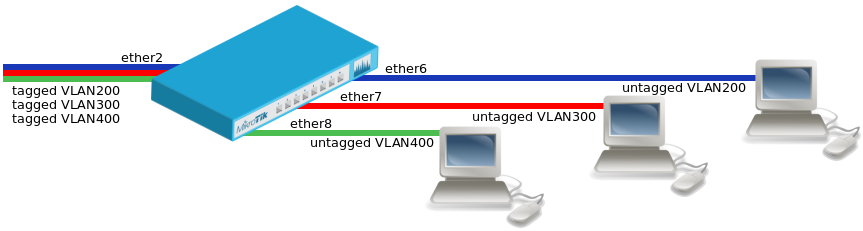
- Create a bridge with disabled
vlan-filteringto avoid losing access to the router before VLANs are completely configured.
/interface bridge add name=bridge1 vlan-filtering=no
- Add bridge ports and specify
pvidfor VLAN access ports to assign their untagged traffic to the intended VLAN.
/interface bridge port add bridge=bridge1 interface=ether2 add bridge=bridge1 interface=ether6 pvid=200 add bridge=bridge1 interface=ether7 pvid=300 add bridge=bridge1 interface=ether8 pvid=400
- Add Bridge VLAN entries and specify tagged and untagged ports in them.
/interface bridge vlan add bridge=bridge1 tagged=ether2 untagged=ether6 vlan-ids=200 add bridge=bridge1 tagged=ether2 untagged=ether7 vlan-ids=300 add bridge=bridge1 tagged=ether2 untagged=ether8 vlan-ids=400
- In the end, when VLAN configuration is complete, enable Bridge VLAN Filtering.
/interface bridge set bridge1 vlan-filtering=yes
VLAN Example #2 (Trunk and Hybrid Ports)
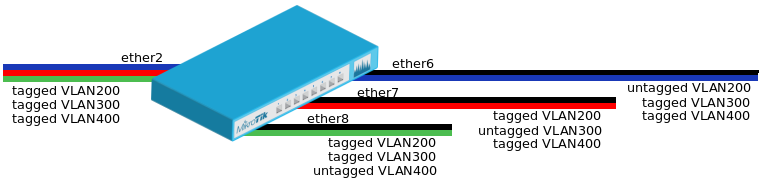
- Create a bridge with disabled
vlan-filteringto avoid losing access to the router before VLANs are completely configured.
/interface bridge add name=bridge1 vlan-filtering=no
- Add bridge ports and specify
pvidon hybrid VLAN ports to assign untagged traffic to the intended VLAN.
/interface bridge port add bridge=bridge1 interface=ether2 add bridge=bridge1 interface=ether6 pvid=200 add bridge=bridge1 interface=ether7 pvid=300 add bridge=bridge1 interface=ether8 pvid=400
- Add Bridge VLAN entries and specify tagged and untagged ports in them. In this example egress VLAN tagging is done on ether6,ether7,ether8 ports too, making them into hybrid ports.
/interface bridge vlan add bridge=bridge1 tagged=ether2,ether7,ether8 untagged=ether6 vlan-ids=200 add bridge=bridge1 tagged=ether2,ether6,ether8 untagged=ether7 vlan-ids=300 add bridge=bridge1 tagged=ether2,ether6,ether7 untagged=ether8 vlan-ids=400
- In the end, when VLAN configuration is complete, enable Bridge VLAN Filtering.
/interface bridge set bridge1 vlan-filtering=yes
VLAN Example #3 (InterVLAN Routing by Bridge)
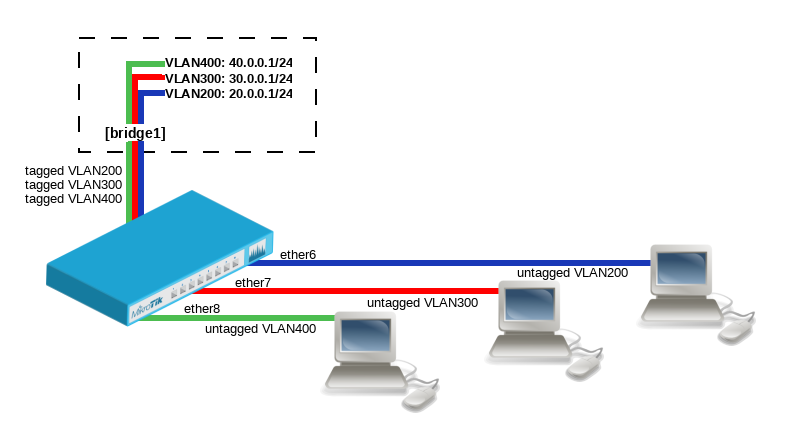
- Create a bridge with disabled
vlan-filteringto avoid losing access to the router before VLANs are completely configured.
/interface bridge add name=bridge1 vlan-filtering=no
- Add bridge ports and specify
pvidfor VLAN access ports to assign their untagged traffic to the intended VLAN.
/interface bridge port add bridge=bridge1 interface=ether6 pvid=200 add bridge=bridge1 interface=ether7 pvid=300 add bridge=bridge1 interface=ether8 pvid=400
- Add Bridge VLAN entries and specify tagged and untagged ports in them. In this example bridge1 interface is the VLAN trunk that will send traffic further to do InterVLAN routing.
/interface bridge vlan add bridge=bridge1 tagged=bridge1 untagged=ether6 vlan-ids=200 add bridge=bridge1 tagged=bridge1 untagged=ether7 vlan-ids=300 add bridge=bridge1 tagged=bridge1 untagged=ether8 vlan-ids=400
- Configure VLAN interfaces on the bridge1 to allow handling of tagged VLAN traffic at routing level and set IP addresses to ensure routing between VLANs as planned.
/interface vlan add interface=bridge1 name=vlan200 vlan-id=200 add interface=bridge1 name=vlan300 vlan-id=300 add interface=bridge1 name=vlan400 vlan-id=400 /ip address add address=20.0.0.1/24 interface=vlan200 network=20.0.0.0 add address=30.0.0.1/24 interface=vlan300 network=30.0.0.0 add address=40.0.0.1/24 interface=vlan400 network=40.0.0.0
- In the end, when VLAN configuration is complete, enable Bridge VLAN Filtering.
/interface bridge set bridge1 vlan-filtering=yes
Management port
There are multiple ways to setup management port on a device that uses bridge VLAN filtering. Below are some of the most popular approaches to properly enable access to a router/switch. Start by creating a bridge without VLAN filtering enabled:
/interface bridge add name=bridge1 vlan-filtering=no
- In case VLAN filtering will not be used and access with untagged traffic is desired
The only requirement is to create an IP address on the bridge interface.
/ip address add address=192.168.99.1/24 interface=bridge1
- In case VLAN filtering is used and access from trunk and/or access ports with tagged traffic is desired
In this example VID99 will be used to access the device, a VLAN interface on the bridge must be created and an IP address must be assigned to it.
/interface vlan add interface=bridge1 name=MGMT vlan-id=99 /ip address add address=192.168.99.1/24 interface=MGMT
For example, if you want to allow access to the router/switch from access ports ether3,ether4 and from trunk port sfp-sfpplus1, then you must add this entry to the VLAN table:
/interface bridge vlan add bridge=bridge1 tagged=bridge1,ether3,ether4,sfp-sfpplus1 vlan-ids=99
After that you can enable VLAN filtering:
/interface bridge set bridge1 vlan-filtering=yes
- In case VLAN filtering is used and access from trunk and/or access ports with untagged traffic is desired
To allow untagged traffic to access the router/switch, start by creating an IP address on the bridge interface.
/ip address add address=192.168.88.1/24 interface=bridge1
It is required to add VID1 to ports from which you want to allow the access to the router/switch, for example, to allow access from access ports ether3,ether4 add this entry to the VLAN table:
/interface bridge vlan add bridge=bridge1 untagged=ether3,ether4 vlan-ids=1
After that you can enable VLAN filtering:
/interface bridge set bridge1 vlan-filtering=yes

Note: If connection to the router/switch through an IP address is not required, then steps adding this IP address can be skipped since connection to the router/switch through Layer2 protocols (e.g. MAC-telnet) will be working either way.
IGMP Snooping
IGMP Snooping which controls multicast streams and prevents multicast flooding is implemented in RouterOS starting from version 6.41.
It's settings are placed in bridge menu and it works independently in every bridge interface.
Software driven implementation works on all devices with RouterOS but CRS1xx/2xx/3xx series switches also support IGMP Snooping with hardware offloading.
Sub-menu: /interface bridge /interface bridge mdb
- Enabling IGMP Snooping on Bridge.
/interface bridge set bridge1 igmp-snooping=yes
- Monitoring multicast groups in the Bridge Multicast Database
[admin@MikroTik] > interface bridge mdb print
BRIDGE VID GROUP PORTS
bridge1 200 229.1.1.2 ether3
ether2
ether1
bridge1 300 231.1.3.3 ether4
ether3
ether2
bridge1 400 229.10.10.4 ether4
ether3
bridge1 500 234.5.1.5 ether5
ether1
[admin@MikroTik] >
Bridge Firewall
Sub-menu: /interface bridge filter, /interface bridge nat
The bridge firewall implements packet filtering and thereby provides security functions that are used to manage data flow to, from and through bridge.
Packet flow diagram shows how packets are processed through router. It is possible to force bridge traffic to go through /ip firewall filter rules (see: Bridge Settings)
There are two bridge firewall tables:
- filter - bridge firewall with three predefined chains:
- input - filters packets, where the destination is the bridge (including those packets that will be routed, as they are destined to the bridge MAC address anyway)
- output - filters packets, which come from the bridge (including those packets that has been routed normally)
- forward - filters packets, which are to be bridged (note: this chain is not applied to the packets that should be routed through the router, just to those that are traversing between the ports of the same bridge)
- nat - bridge network address translation provides ways for changing source/destination MAC addresses of the packets traversing a bridge. Has two built-in chains:
- srcnat - used for "hiding" a host or a network behind a different MAC address. This chain is applied to the packets leaving the router through a bridged interface
- dstnat - used for redirecting some packets to other destinations
You can put packet marks in bridge firewall (filter and NAT), which are the same as the packet marks in IP firewall put by '/ip firewall mangle'. In this way, packet marks put by bridge firewall can be used in 'IP firewall', and vice versa.
General bridge firewall properties are described in this section. Some parameters that differ between nat and filter rules are described in further sections.
Properties
| Property | Description |
|---|---|
| 802.3-sap (integer) | DSAP (Destination Service Access Point) and SSAP (Source Service Access Point) are 2 one byte fields, which identify the network protocol entities which use the link layer service. These bytes are always equal. Two hexadecimal digits may be specified here to match a SAP byte |
| 802.3-type (integer) | Ethernet protocol type, placed after the IEEE 802.2 frame header. Works only if 802.3-sap is 0xAA (SNAP - Sub-Network Attachment Point header). For example, AppleTalk can be indicated by SAP code of 0xAA followed by a SNAP type code of 0x809B |
| arp-dst-address (IP address; default: ) | ARP destination address |
| arp-dst-mac-address (MAC address; default: ) | ARP destination MAC address |
| arp-gratuitous (yes | no; default: ) | Matches ARP gratuitous packets |
| arp-hardware-type (integer; default: 1) | ARP hardware type. This is normally Ethernet (Type 1) |
| arp-opcode (arp-nak | drarp-error | drarp-reply | drarp-request | inarp-reply | inarp-request | reply | reply-reverse | request | request-reverse) |
ARP opcode (packet type)
|
| arp-packet-type (integer: 0..65535 decimal format or 0x0000-0xffff hex format) | ARP Packet Type |
| arp-src-address (IP address; default: ) | ARP source address |
| arp-src-mac-address (MAC address; default: ) | ARP source MAC address |
| chain (text) | Bridge firewall chain, which the filter is functioning in (either a built-in one, or a user defined) |
| dst-address (IP address; default: ) | Destination IP address (only if MAC protocol is set to IPv4) |
| dst-mac-address (MAC address; default: ) | Destination MAC address |
| dst-port (integer 0..65535) | Destination port number or range (only for TCP or UDP protocols) |
| in-bridge (name) | Bridge interface through which the packet is coming in |
| in-interface (name) | Physical interface (i.e., bridge port) through which the packet is coming in |
| ingress-priority (integer 0..63) | Matches ingress priority of the packet. Priority may be derived from VLAN, WMM or MPLS EXP bit. read more» |
| ip-protocol (ddp | egp | encap | etherip | ggp | gre | hmp | icmp | icmpv6 | idpr-cmtp | igmp | ipencap | ipip | ipsec-ah | ipsec-esp | ipv6 | ipv6-frag | ipv6-nonxt | ipv6-opts | ipv6-route | iso-tp4 | l2tp | ospf | pim | pup | rdp | rspf | rsvp | st | tcp | udp | vmtp | vrrp | xns-idp | xtp) |
IP protocol (only if MAC protocol is set to IPv4)
|
| jump-target (name) | If action=jump specified, then specifies the user-defined firewall chain to process the packet |
| limit (integer/time,integer) |
Restricts packet match rate to a given limit.
|
| log-prefix (text) | Defines the prefix to be printed before the logging information |
| mac-protocol (802.2 | arp | ip | ipv6 | ipx | length | mpls-multicast | mpls-unicast | pppoe | pppoe-discovery | rarp | vlan or integer: 0..65535 decimal format or 0x0000-0xffff hex format) | Ethernet payload type (MAC-level protocol)
|
| out-bridge (name) | Outgoing bridge interface |
| out-interface (name) | Interface that the packet is leaving the bridge through |
| packet-mark (name) | Match packets with certain packet mark |
| packet-type (broadcast | host | multicast | other-host) |
MAC frame type:
|
| src-address (IP address; default: ) | Source IP address (only if MAC protocol is set to IPv4) |
| src-mac-address (MAC address; default: ) | Source MAC address |
| src-port (integer 0..65535) | Source port number or range (only for TCP or UDP protocols) |
| stp-flags (topology-change | topology-change-ack) |
The BPDU (Bridge Protocol Data Unit) flags. Bridge exchange configuration messages named BPDU periodically for preventing loops
|
| stp-forward-delay (time 0..65535) | Forward delay timer |
| stp-hello-time (time 0..65535) | STP hello packets time |
| stp-max-age (time 0..65535) | Maximal STP message age |
| stp-msg-age (time 0..65535) | STP message age |
| stp-port (integer 0..65535) | STP port identifier |
| stp-root-address (MAC address) | Root bridge MAC address |
| stp-root-cost (integer 0..65535) | Root bridge cost |
| stp-root-priority (integer 0..65535) | Root bridge priority |
| stp-sender-address (MAC address) | STP message sender MAC address |
| stp-sender-priority (integer 0..65535) | STP sender priority |
| stp-type (config | tcn) |
The BPDU type:
|
| vlan-encap (802.2 | arp | ip | ipv6 | ipx | length | mpls-multicast | mpls-unicast | pppoe | pppoe-discovery | rarp | vlan or integer: 0..65535 decimal format or 0x0000-0xffff hex format) | the MAC protocol type encapsulated in the VLAN frame |
| vlan-id (integer 0..4095) | VLAN identifier field |
| vlan-priority (integer 0..7) | The user priority field |
Notes
- STP matchers are only valid if destination MAC address is 01:80:C2:00:00:00/FF:FF:FF:FF:FF:FF (Bridge Group address), also
stpshould be enabled.
- ARP matchers are only valid if mac-protocol is
arporrarp
- VLAN matchers are only valid for
vlanethernet protocol
- IP-related matchers are only valid if mac-protocol is set as
ipv4
- 802.3 matchers are only consulted if the actual frame is compliant with IEEE 802.2 and IEEE 802.3 standards (note: it is not the industry-standard Ethernet frame format used in most networks worldwide!). These matchers are ignored for other packets.
Bridge Packet Filter
Sub-menu: /interface bridge filter
This section describes bridge packet filter specific filtering options, that are specific to '/interface bridge filter'.
Properties
| Property | Description |
|---|---|
| action (accept | drop | jump | log | mark-packet | passthrough | return | set-priority) |
|
Bridge NAT
Sub-menu: /interface bridge nat
This section describes bridge NAT options, that are specific to '/interface bridge nat'.
Properties
| Property | Description |
|---|---|
| action (accept | drop | jump | mark-packet | redirect | set-priority | arp-reply | dst-nat | log | passthrough | return | src-nat) |
|
| to-arp-reply-mac-address (MAC address) | Source MAC address to put in Ethernet frame and ARP payload, when action=arp-reply is selected |
| to-dst-mac-address (MAC address) | Destination MAC address to put in Ethernet frames, when action=dst-nat is selected |
| to-src-mac-address (MAC address) | Source MAC address to put in Ethernet frames, when action=src-nat is selected |
[ Top | Back to Content ]
